The latest variant of the Dyre virus was discovered by Trend Micro in early 2015. Dyre is financial malware that targets banks and uses propagation and evasion techniques to reproduce itself and avoid detection. In this article, I’d like to identify how the virus works and discuss how to avoid getting this nasty virus on your network. WatchPoint forensic analysts have had first-hand experience detecting, analyzing and removing the Dyre virus for our customers. To provide an example and protect our customer’s anonymity I will discuss an example attack we have remediated, and I will refer to that company as Acme Insurance.
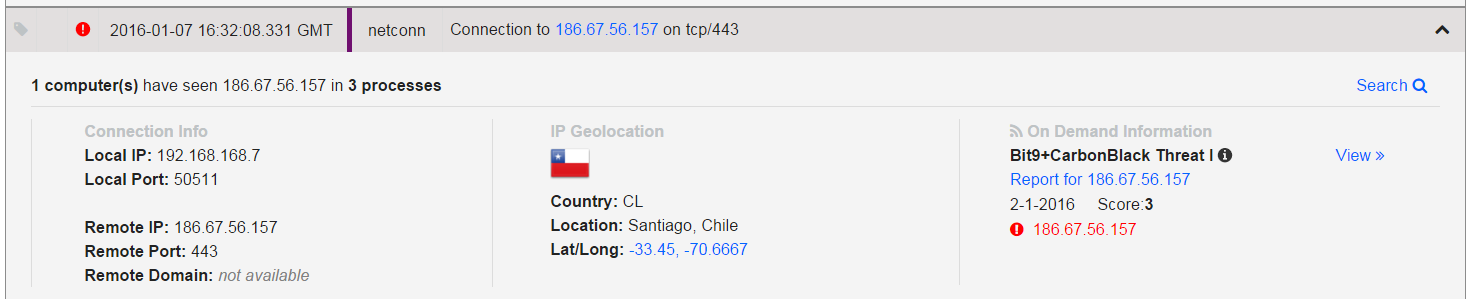
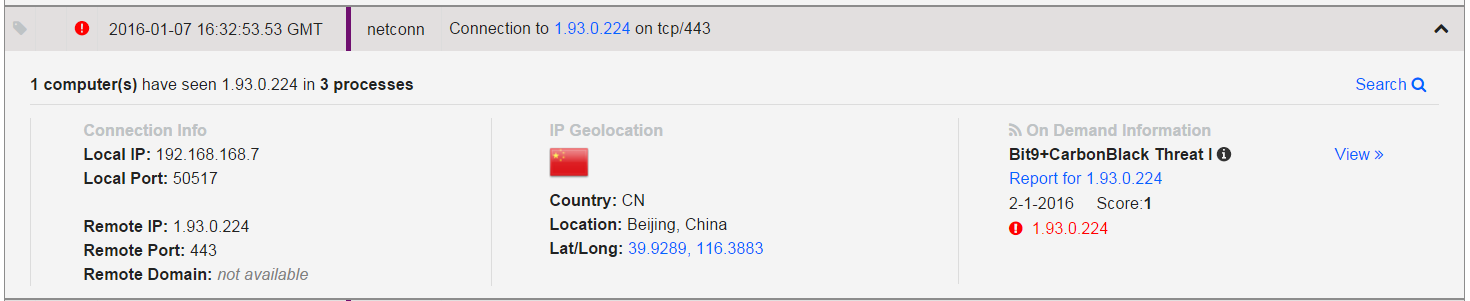
The Dyre  virus was designed to steal information from 206 websites but was expanded to 355 targets in 2015. Most of the targets are websites belonging to banks and Bitcoin wallets. With Acme Insurance, the ultimate goal of the infection was to steal information from the user’s computers to facilitate the theft of their financial information. Acme was infected with malware that opened network connections between their financial institution and the attackers. WatchPoint uses Carbon Black to detect suspicious behavior of our customer’s endpoints, and we were alerted to a number of network connections that the cybercriminals had initiated outbound outside of the United States to places like Czech Republic, Brazil, and China. Since Acme doesn’t bank in those countries, we were able to identify rather quickly that this was suspicious behavior.
virus was designed to steal information from 206 websites but was expanded to 355 targets in 2015. Most of the targets are websites belonging to banks and Bitcoin wallets. With Acme Insurance, the ultimate goal of the infection was to steal information from the user’s computers to facilitate the theft of their financial information. Acme was infected with malware that opened network connections between their financial institution and the attackers. WatchPoint uses Carbon Black to detect suspicious behavior of our customer’s endpoints, and we were alerted to a number of network connections that the cybercriminals had initiated outbound outside of the United States to places like Czech Republic, Brazil, and China. Since Acme doesn’t bank in those countries, we were able to identify rather quickly that this was suspicious behavior.
Network Connections Initiated by Dyre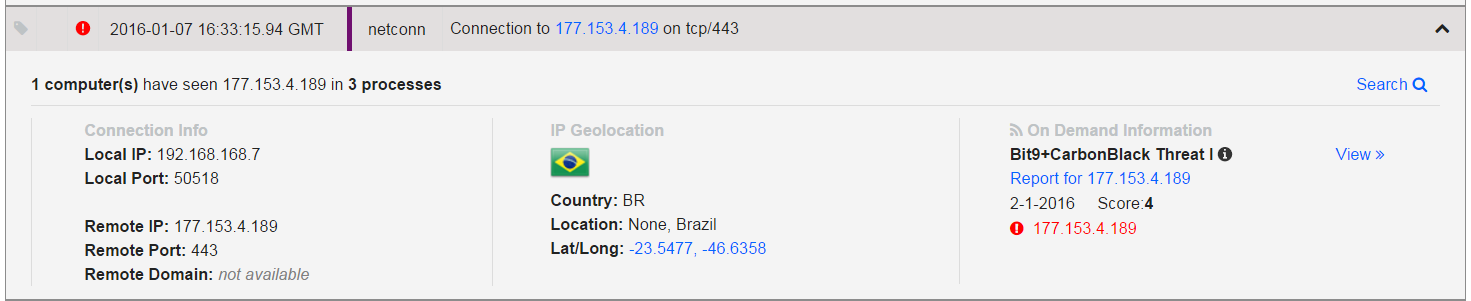
Dyre Infections detected by Trend Micro:
- 68% located in the United States
- 10% located in Canada
- 4% located in Chile
The Infection Process
The attack is quite sophisticated and originates, like many others, from an unsolicited email. The spam email contains the Upatre downloader which is disguised as a fax or package delivery. When opened, the Upatre downloads the Dyre Trojan which then downloads a worm called WORM_MAILSPAM.XDP. The worm uses Microsoft Outlook to send spam emails with the Upatre downloader attached. The malware uses Outlook’s msmapi32.dll library to process the job. The attached Upatre malware repeats the cycle by downloading Dyre, which allows Dyre to spread rapidly. Interestingly the worm doesn’t use the Outlook contact list to spread. It uses email addresses obtained from a command and control (C&C) server. After the emails are sent, the worm deletes itself. Dyre even uses the SSL protocol to hide the communication with the C&C servers. SSL is normally used to secure passwords when logging into websites. This entire process can make the virus quite difficult to detect. Once WatchPoint detected the infection at Acme Insurance, our forensic expert assisted our customer with running multiple virus scans on the infected machine to see if it would be detected. In this case, anti-virus was zero percent effective, and not one of the products detected this attack.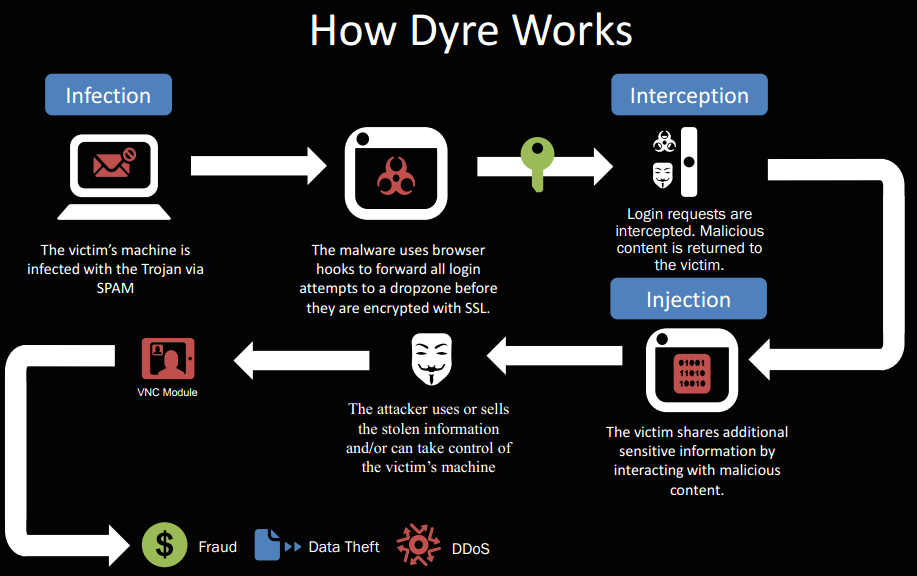
Multiple Attack Vectors
The C&C server addresses are hard-coded into the binary, and if Dyre cannot connect to the C&C servers, the threat will attempt to connect to a URL provided by the malware’s Domain Generation Algorithm (DGA). Using DGA, a URL is generated by producing a 34-character string append to one of the six Top Level Domains (TLD): .cc, .ws, .to, .in, .hk, .cn, .tk, and .so.
Dyre can also connect to a hard-coded address on the Invisible Internet Project (i2P) which is an anonymity network used by the online drug marketplace, Silk Road Reloaded, and the CryptoWall 4.0 ransomware. Symantec reported in early 2015 that cybercriminals were using the Cutwail botnet for short-term, high-volume spam blasts, each lasting just a few minutes but generating millions of spam emails. These emails contained links that pointed to a malicious website that was set up to serve out a variant of Dyre or alternatively linked to phishing websites.
After the infection was discovered at Acme Insurance, the forensic experts at WatchPoint were able to isolate the host from the network while the attack was analyzed. Due to how embedded the virus was, the machine had to be reimaged before it could be placed back into production, but that is a small price to pay. Ultimately, WatchPoint was able to help Acme Insurance keep their money in their bank account where it belongs. Now that we have a general idea of what Dyre is and how it propagates, it’s important to advise all the users on your network to be on the lookout for phishing and social engineering attacks, and to adhere to the following best practices as presented by Symantec.
- Exercise caution when receiving unsolicited, unexpected, or suspicious emails.
- Avoid clicking on links in unsolicited, unexpected, or suspicious emails.
- Avoid opening attachments in unsolicited, unexpected, or suspicious emails.
- Keep security software up-to-date.

