
April was an extremely busy month in the world of ransomware. There are several new ransomware variants that look like they are going to stay around for a while. Cerber has taken over the reigns as the most distributed ransomware. However, Locky is looking to come back strong after its demise in 2016. We have also added several decryptors to our list, which is the largest you’ll find on the internet. The best news about ransomware in April is it looks like there weren’t any new attack vectors for Android users.
New Ransomware Variants
Each month, there are copious amounts of ransomware variants that pop up and never seem to come to fruition. Whether that is because a decryptor is released or they don’t see much success, depends on the variants. However, we aim to educate and inform our readers on the variants we believe will have the biggest impact on the cybersecurity world for the foreseeable future.
Matrix Ransomware
Matrix ransomware has been out for quite some time. However, it was a variant that never really reached its potential; until now. Matrix recently started distributing its ransomware via hacked sites that have the EITest scripts injected into them. When an individual goes to one of these hacked sites, a RIG exploit kit is used to attempt to take advantage of vulnerable programs on the computer in order to install the ransomware.
What’s interesting about Matrix and what makes it look like a ransomware variant that is going to be around for a while is that it also contains a worm. The worm feature allows the ransomware to spread to other machines through folder shortcuts. Basically, Matrix will hide a folder and then create a shortcut with the same name. The newly created folder will contain ransomware and can be transferred to new computers via network shares or removable drives.
Mole Ransomware
Mole ransomware appeared on the scene in the middle of April. It has been confirmed that the ransomware is a member of the CryptoMix family. The ransomware is being distributed like many other variants, through SPAM email campaigns. Mole is distributed as a fake USPS failed delivery email with a link that will take you to a Microsoft Word Online site that displays a supposedly unreadable document.
In the article we released about Mole, we discussed the complex steps the ransomware goes through to install. Mole goes through this process to gain administrative privileges. To read about the full process of Mole ransomware, read our article here.
It appears that Mole may not have garnered the attention or victims wanted as they quickly changed tactics and increased the complexity of the ransomware only two days after its release. We can see the timeline of the very quick changes below.
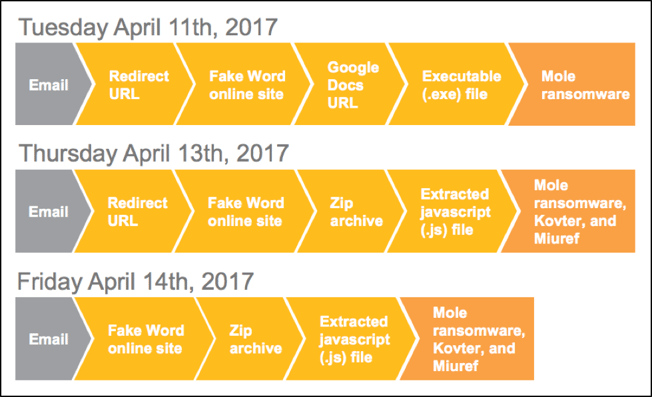
On Thursday, April 13th victims infected with Mole ransomware would also be infected with both Kovter and Miuref ransomware. On the following day, the hackers stopped using a redirected link in the malicious spam and instead linked the ransomware directly to a fake Word online site. With the original version of Mole, there were several steps that had to be taken after the Word file was executed for the ransomware to be installed. With the updated version, Mole is installed after the victim has executed the Word document.
Cerber Update
The distributors of the ransomware have been quite busy as Cerber has taken over as the most circulated ransomware in the world for the first quarter of 2017. As you can see in the graph below, Cerber has had anywhere between 70% to almost 87% of the market share for ransomware in the first three months.
Cerber’s rise to the #1 spot is attributed to the numerous versions that have been released this year, including one whose features allow it to evade security products that rely on machine learning and behavioral analysis. Furthermore, Cerber has adopted the increasingly popular Ransomware-as-a-Service model. This model relies on greedy and money hungry hacking groups to keep Cerber in distribution. Remember, you heard it here first, 2017 will be known as the year of ‘Ransomware-as-a-Service.’
Locky Returns!
It appears that Locky doesn’t like being the shadows of Cerber and is looking to make its return to dominance. Just a week after it was announced that Cerber is the most distributed ransomware in the world, Locky returned via a new email campaign. In its very simple campaign, emails containing Locky ransomware are appearing to be a payment receipt from random companies. The PDF attached contains the malware, and when macros are enabled, Locky is installed, and the encryption process begins.
It’s too early in the newly regenerated Locky campaign to see whether they are having success. However, we will make sure to follow up in the month of May to see how they are doing.
Decryptors
At WatchPoint, we are very proud to have the largest list of ransomware decryptors on the internet. Below are the decryptors we found during the month of April. The list, which can be found here, is continuously updated. Remember, decryptors are your last effort at ridding your device of ransomware, and you should never rely on them to save you from being infected with ransomware.
Here are the ransomware decryptors we found in April:
- MacandCheese
- MafiaWare
- Mahasaraswati
- Maktub Locker
- SamSam
- Mamba
- Cry9
- BarRax
- Damage
- Crypton
- PHP Ransomware
- TM Ransomware
Instead of relying on decryptors, WatchPoint has a product to stop a ransomware attack in seconds; CryptoStopper. CryptoStopper stops ransomware attacks in their tracks. It uses deception technology in the form of Watcher Files placed on your network. The program continuously monitors the Watcher Files for the encryption process to start and will immediately identify and isolate the infected workstation. Upon isolating the attack, CryptoStopper will shut down the infected workstation and will send you an email notification informing you that a ransomware attack has been discovered and contained. On average, CryptoStopper stops a ransomware attack in 17 seconds, preventing all your targeted files from being encrypted and minimizing the damage done.

