2016 has been tabbed as the “Year of Ransomware.” So, what will 2017 bring? It’s looking like ransomware and extortion attacks, Internet of Things (IoT) attacks, and internal threats will continue to…
Jordan Kadlec

Popcorn Time Ransomware Spreading Christmas Cheer!
Cybercriminals are taking ransomware to another level with the latest variant named Popcorn Time. The new malware gives users the option of paying the ransom of one bitcoin (about $772), or they can…
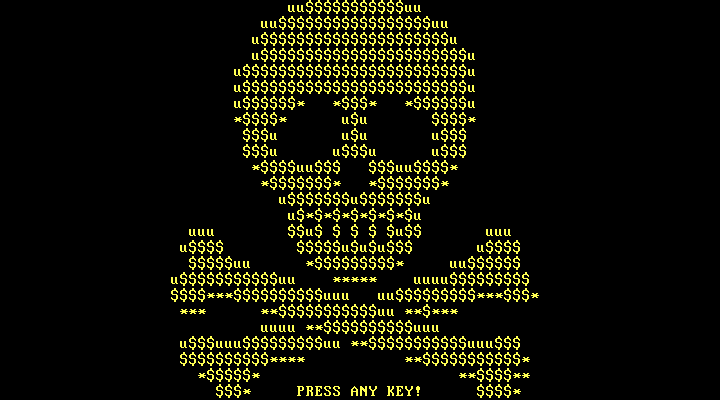
GoldenEye Ransomware - A New Variant of Petya Ransomware
The creators of Petya ransomware, going by the name of Janus, have come out with a new variant tabbed as GoldenEye ransomware. Continuing with the James Bond theme, the GoldenEye ransomware is almost…
Kelihos Botnet Making Its Return by Distributing Ransomware
The Kelihos botnet, also known as Waledac, has become one of the primary sources for distributing ransomware over the last few months. After keeping a low profile following takedown attempts back in…
November Ransomware in Review
New to WatchPoint is a review of ransomware variants that have appeared throughout the month. While there are numerous variants that are released each week, many will never make it too far into…
Locky Ransomware Infiltrates Facebook Through JPG Images
Cybercriminals are continuously finding new ways to infiltrate users’ systems using ransomware. Researchers have recently discovered that hackers are using .JPG images to distribute Locky Ransomware…
San Francisco Public Transit Hit by Ransomware Attack
On one of the busiest shopping days of the year, the San Francisco Municipal Transportation Agency (SFMTA) was hit by ransomware. The attack caused ticket machines for the SFMTA’s light rail transit…
Adult Friend Finder Exposed in Latest Breach
You would think after the Ashley Madison incident, where nearly 37 million cheating men and women had their data stolen, sites like Adult Friend Finder would up their cybersecurity. Wrong! On Sunday…
RATs Everywhere
Remote Access Trojans, or RATs for short, are malicious programs that run invisibly on host PCs and permit an intruder remote access and control. On a basic level, many RATs mimic the functionality…