
Ransomware is a type of malware that denies access to a device or files until a ransom is
paid, at which point the cyber criminals will provide a decryption key to allow the user to regain access to their system or files. The majority of ransomware attacks demand a bitcoin payment of $250 to $1000 although we have seen much larger ransom demands presented to larger corporations. The main attack vectors used to infect a computer include phishing emails, compromised websites, online advertisements and free downloads.
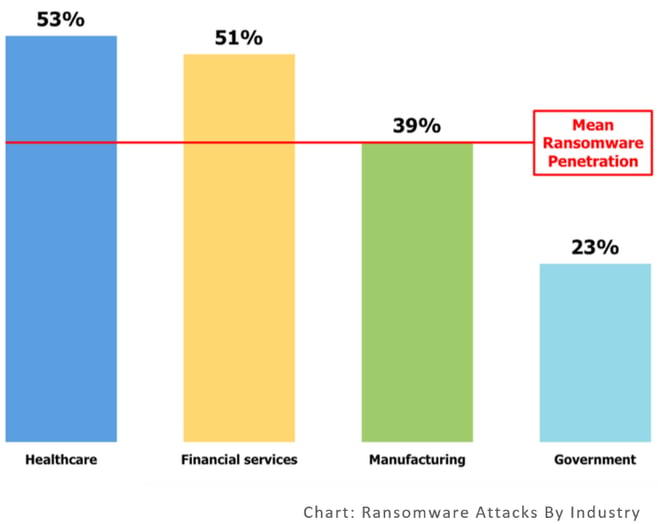
Odds of Ransomware Attack Close to 50%
Ransomware infections continue to rise. In 2015 40% of US businesses where infected by ransomware. An Osterman Research survey from July of 2016, found that 54% of U.S. businesses surveyed had come under attack from ransomware in the trailing 12 months. Of the 540 companies surveyed by Osterman, the most commonly targeted types of business were in the healthcare or finance industries.
 015.
015.
"In the last six to 12 months, this has just gone so aggressively to the business environment," Kleczynski of Malwarebytes says. "We see companies from 25 people all the way to 250,000 people getting hit with ransomware."
With so many ransomware attacks in 2015 and considering that the targets are largely healthcare and financial services, you would assume these industries would increase their cyber defenses and attempt to thwart any attempt to encrypt their data and hold it for ransom. In a recent interview, Malwarebytes CEO Marcin Kleczynski said that simply isn’t the case for the banks.
According to Kleczynski, banks are stockpiling bitcoins in case they get attacked with ransomware. “I talked to a couple of banks, and they say they have 50-100 bitcoin ready at all times in a wallet to deploy if a ransomware attack hits,” he said.
Examining the Banks Response to Ransomware
The response to this ransomware epidemic by banks is perplexing, to say the least. If a criminal walked into a bank, held the teller hostage and then demanded a $10,000 ransom, that criminal would be pursued to the fullest extent of the law until arrested, put on trial and imprisoned for their crime. A cybercriminal launching an attack from China or Russia is almost impossible to capture and prosecute so increasing network defenses using deception technology, endpoint protection, and propriety CryptoStopper.io™ software from WatchPoint would be ideal solutions to dealing with ransomware attacks. CryptoStopper can identify an attack, isolate the offending workstation and stop the encryption process in seconds. However, instead of increasing their defenses, many banks have stuck their head in the sand and decided the best option is to pay the cybercriminals.
Why Paying the Ransom is a Terrible Idea
It is a terrible idea to pay the ransom although sometimes it may be necessary. If you don’t have good backups and your data is critical; you may have to pay the ransom. If lives are at stake, pay the ransom. Was your college thesis encrypted and you don’t have a copy? You will probably have to pay the ransom. The problem with paying the ransom is that it encourages the cybercriminals to continue running ransom schemes. The ransomware industry will continue to grow exponentially as ransoms continue to be paid. There are also a number of documented cases that prove when a ransom is paid the cyber criminals continue to run the attack against the same business over and over. Lastly, it’s quite possible that even if you do pay the ransom, you will not get a decryption key, or the decryption process may not work.
Ransomware is not going away. Cybercriminals can make millions with an investment of less than $50 purchasing an exploit kit. If one cyber criminal gets 1000 people to pay a $500 ransom, they just made $500,000. That’s a pretty good return for such a small investment and the little bit of effort in spamming a few thousand people. To properly defeat the cyber criminals you have to have good backups. You must educate your employees about the dangers of phishing emails and test them regularly. You can no longer rely on antivirus and your firewall to protect you. It’s time to upgrade your defenses to 21st-century technology using deception, traps, and anti-ransomware software.
Further Reading:

