
Photo courtesy of waterfordbankna.com
Business Email Compromise (BEC) attacks saw an 80% increase in the second quarter of 2018. Mimecast, a company specializing in email protection, conducted an assessment analyzing 142 million emails which revealed 203,000 malicious links in over 10 million emails that were deemed safe by other security systems. Between 2014 and 2018, U.S. victims of BEC attacks have collectively lost $2.9 billion, while global losses are estimated at four times that amount.
What are BEC Attacks?
BEC attacks, also known as ‘CEO fraud,’ are social engineering scams aimed at tricking email recipients into sending money directly to the attackers. Asaf Cidon, Vice President of Content Security Services at Barracuda Networks, describes BEC attacks perfectly.
“Criminals use business email compromise attacks to obtain access to a business email account and imitate the owner’s identity, in order to defraud the company and its employees, customers, or partners,” Cidon stated. “In most cases, scammers focus efforts on employees with access to company finances or payroll data and other personally identifiable information.”
To provide a sense of urgency in the emails, attackers will often pretend to be the CEO or another C-level executive, and send an email saying they need a wire transfer to be made immediately.
How Does a BEC Attack Work?
The first thing an attacker will do is his or her homework. The primary reason BEC attacks are so effective and lucrative for attackers is they pose as legitimate C-level executives. The attacker will create a spoof email address that looks extremely similar to the target company’s CEO and will even include the CEO’s own email signature. Next, the attacker will look through the company’s directory to find their target employee, who is most likely an accountant of some sort with the ability to transfer funds. The attacker will then send an extremely simple email, such as the one shown below, asking the targeted employee to wire money.
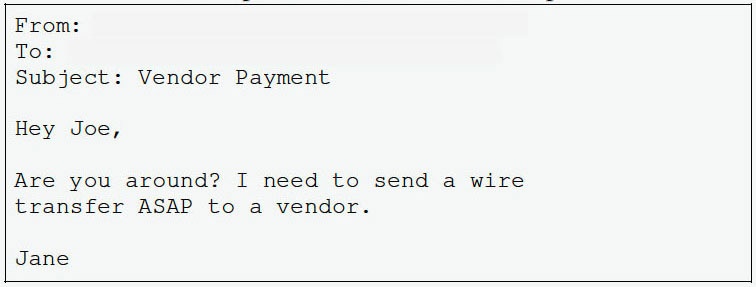
Other BEC attacks have also been conducted requesting that an invoice be paid which includes an attachment to a fake invoice to a fake company. Believing the email is legitimately from the CEO, the targeted employee will feel a sense of urgency to complete the wire or pay the fake invoice without asking any questions. Once the wire is sent, there is little to no chance the funds will ever be seen again.
The Success of BEC Attacks
Over the last four years, BEC attacks have become a billion-dollar industry. Between December 2016 and this past May, reports of BEC attacks have increased by 136 percent. However, it’s believed that only a fraction of these crimes are ever reported, meaning the problem is much more severe than it appears.
Why are these attacks for effective? First, as we mentioned before, the email appears to be coming from the CEO or a high-level executive. In the corporate world, receiving such an email is a big deal and doesn’t go unnoticed by someone at the managerial level or below. Often, when receiving an email with a request from the CEO, few people have the audacity to actually check with the high-level executive to ensure the email was actually sent from them. They will simply perform the task without asking any questions.
Next, headlines about cybersecurity have been diluted with article after article about malicious links or attachments. DON’T CLICK THE LINK OR OPEN THE ATTACHMENT. How many times have we read that? While these articles are there to educate the public about the most popular forms of cyberattacks and seriously, DON’T CLICK THE LINK OR OPEN THE ATTACHMENT, there are other types of very serious cyberattacks. Seventy-one percent of BEC attacks don’t include a link or an attachment; again, making the email look legitimate and safe from anything malicious.
Recently, attackers have also started to build rapport with targeted employees. The example email below shows us an email asking if Joe is around for something urgent.
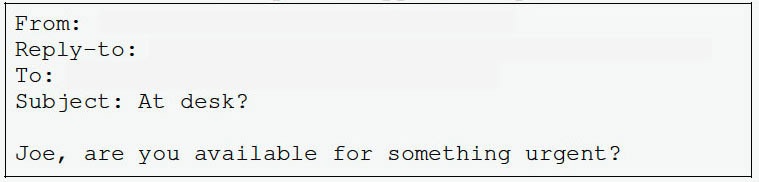
Eager to show his worth, Joe replies to the email. The CEO, who is actually the attacker, follows Joe’s email by asking him to pay an invoice and to let him or her know when the invoice has been paid.
How to Defend Against BEC Attacks
There are several ways to defend against BEC attacks; however, like all social engineering attacks, training employees is the most important. Show users what BEC attacks look like and regularly test them to ensure they are aware these attacks are happening.
Aside from training employees, verification of all wire transfers is a simple way to block attackers from ever receiving money. Always make a requested wire transfer follow a prescribed series of steps. Such steps include an in-person or telephone verification, and using only a pre-approved list of telephone numbers for contacts. Employees should never rely on contact information included in an email.
Last and certainly not least, is perhaps the most difficult way to defend against a BEC attack. As we mentioned before, the reason BEC attacks are so successful is because the emails are coming from a C-level executive and they have a sense of urgency. However, a good accountant is one that is always questioning things. Always assume that an email requesting a wire transfer has been compromised until proven otherwise. Send a separate email to the individual requesting the transfer AND make a phone call or go to their office to verify they actually want the wire to be processed. While this may seem like you are wasting your CEO’s time, a simple email, phone call, or visit to their office will be extremely appreciated that one time you are incurring a BEC attack.

