 A new form of ransomware has emerged called “Cerber” that not only encrypts your files but will also use a text-to-speech function to read the ransom demand out loud to you. The ransomware is thought to have originated from Russian underground forums. The program is so effective that there is currently no way to decrypt compromised files without paying the ransom.
A new form of ransomware has emerged called “Cerber” that not only encrypts your files but will also use a text-to-speech function to read the ransom demand out loud to you. The ransomware is thought to have originated from Russian underground forums. The program is so effective that there is currently no way to decrypt compromised files without paying the ransom.
I suspect Cerber is being sold as ‘Ransomware-as-a-Service” (RaaS) where someone has created the malicious package and sells it on the darknet to other cybercriminals who actually run the ransom. This RaaS model has proven to be quite a lucrative business model. The coder even gets a percentage of the ransom fee if the victim pays.
Decryption of Data Impossible without Paying Ransom
“… at this point there is no known way to decrypt a victim's encrypted files for free," Lawrence Abrams, Bleeping Computer.
"When infected, a victim's data files will be encrypted using AES encryption, and they will be told they need to pay a ransom of 1.24 bitcoins or $500 to get their files back. Unfortunately, at this point there is no known way to decrypt a victim's encrypted files for free," explained Lawrence Abrams, a malware expert at BleepingComputer who has analyzed the Cerber source code.
Former U.S.S.R. Gets a Pass
An interesting caveat of this new form of ransomware is who it doesn’t infect. When Cerber first infects a computer, it checks to see what country the victim is from. It appears that the ransomware avoids infecting computers that are in the 12 former Soviet countries like Georgia, Russia and Uzbekistan. After the location check, Cerber displays a fake reboot alert and will begin the massive encryption process after the reboot. Cerber will create three different ransom notes, each containing information explaining how victims can decrypt their data. The files link to a Tor-based decryption service that charges users a fee to regain access to their files.
A Spoken Ransom
Cerber sets itself apart from all other crypto ransomware with its ability to vocalize the ransom to the victim. I recently wrote an article about a company that has been hit with crypto ransomware three times. The third time the company was hit with ransomware I heard the ransom message as it was playing on the victim’s computer. Even before gaining remote access to the machine to visually see the infection; I heard the ransom and confirmed the crypto ransomware infection.
"One of the ransom notes that Cerber creates is a bit more 'special' than the others. The #DECRYPTMYFILES.vbs file contains VBScript, which will cause the victim's computer to speak to them," explained Abrams.
As you can see in the screenshot below; the ransom note contains a link to a Tor-based 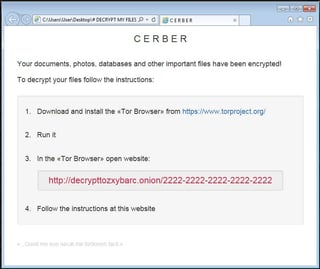 website called “Cerber Decryptor” which provides step by step instructions on how to pay the ransom with Bitcoins. If the ransom isn’t paid, the ransom amount will double the following week. Notice the quote at the bottom. Talk about adding insult to injury.
website called “Cerber Decryptor” which provides step by step instructions on how to pay the ransom with Bitcoins. If the ransom isn’t paid, the ransom amount will double the following week. Notice the quote at the bottom. Talk about adding insult to injury.
“…Quod me non necat me fortiorem facit.”
"That which does not kill me makes me stronger." - Friedrich Nietzsche
As previously mentioned, there is no free option to decrypt your files. If you get hit with Cerber you will have to pay the ransom unless you have a good backup that you can use to restore your data. I highly recommend you examine your current backups to make sure they are working properly or getting hit with Cerber is going to set you back. Now is a good time to look at other no-cost ways to secure your network as well.
How WatchPoints Detect Ransomware
WatchPoint uses a unique tripwire system placing small, discreet sensors (Watchpoints), on your network to detect when an attacker or rogue user is somewhere they shouldn’t be. It is like having a home security system with window, door and motion sensors everywhere. Those sensors are backed up by a recording system that records every move made on the network. When a sensor is tripped, you simply use the recording system to play back exactly what happened and determine the root cause in a matter of seconds.
Contact Us to see how a simple WatchPoint sensor disguised as a Microsoft Word file works. When someone opens the Microsoft Word document you create, you will get an email alert.
Further Reading…
CryptoJoker – Ransomware You Can Negotiate With
Defenseless Against Cryptowall…Or Are We?
Why Didn’t My AntiVirus Detect Cryptowall….again!?
Gone Phishing: Why Human Resources is Vulnerable to Crypto Ransomware Attacks
How Many of Your Employees Will Get Phished Today?


