Ransomware has been the most prevalent form of cyber attacks in 2016. Between the end of 2015 and the first half of 2016, ransomware saw an 800% increase in ransom paid to cyber criminals. Cyber security expert, Aleks Gostev explains why ransomware has become the most preferred weapon of choice for cyber criminals.
“One of the reasons why ransomware has become so popular lies in the simplicity of the business model used by cyber criminals,” says Gostev, Chief Security Expert of the Global Research and Analysis Team (GReAT) at Kaspersky Lab. “Once the ransomware gets into the users’ system there is almost no chance of getting rid of it without losing personal data. Also, the demand to pay the ransom in bitcoins makes the payment process anonymous and almost untraceable which is very attractive to fraudsters.”
Cerber, Zepto Virus, TeslaCrypt and CryptXXX were the most popular forms of ransomware in the first half of 2016. CrypMIC, which resemble CryptXXX, is the latest variant causing damage globally.
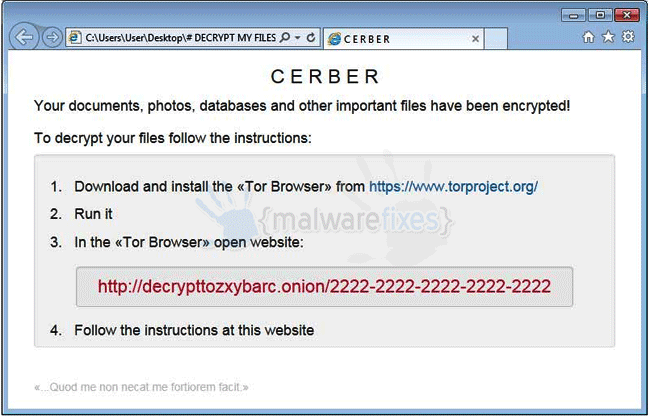
Cerber
Cerber Ransomware encrypts its victims’ files and adds the extension CERBER to every file that has been affected. As Cerber encrypts the files, it creates TXT, HTML, and VBS files named ‘DECRYPT MY FILES’ with instructions on how to pay the ransom. The only way to recover the files is by using the ‘Cerber Decryptor’ provided by the cybercriminals responsible for the ransomware. Victims must pay 1.24 BitCoin ($500-$800); if they haven’t done so within a week, the amount is doubled.
In the last couple of weeks, Cerber has released Cerber v2, which is not decryptable with any of the decryption tools that are on the market. According to Softpedia, the Cerber V2 variant targets 456 different types of files, making it the broadest ransomware attack on the market.
Zepto Virus
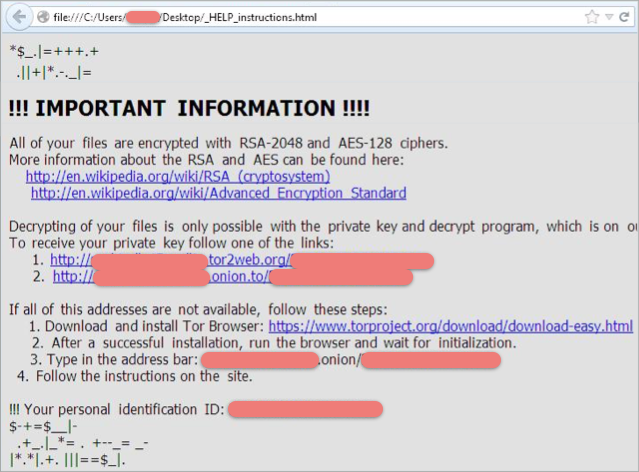
Zepto is the predecessor of one of the most popular forms of ransomware to date, Locky. However, instead of adding ‘.locky’ to the end of encrypted files, it adds ‘.zepto.’ Zepto arrives in one of two ways: in emails with an attached ZIP file or in emails with an attached DOCM (document with macros) file. Once Zepto encrypts the victim’s files, a ransom note appears informing the user of the actions that have taken place and provides instructions on how the victim can receive the decryption key.
TeslaCrypt
At the end of 2015, TeslaCrypt was tabbed as the most dangerous form of malware in circulation. Like most forms of ransomware, TeslaCrypt encrypted victims’ files through spam emails using a wide range of social engineering techniques to lure the recipient into opening them. The ransomware came to prominence because of all the refined versions and tactics used by the creators. While other forms of ransomware shut down or creators come up with a modification once the current form has been exposed by antivirus software; the creators of TeslaCrypt kept making a better version.
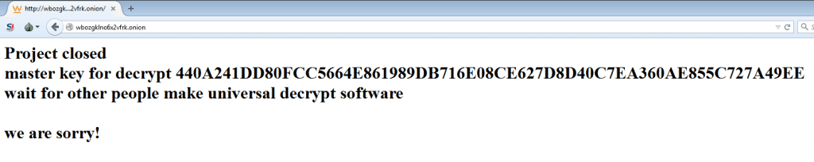
For reasons unknown to the public, the creators of TeslaCrypt slowly closed their doors and released a decryption key to their ransomware in May of 2016. Their previous distributors then switched over to distributing a new ransomware dubbed CryptXXX.
At WatchPoint, we recently released a demo on how our new product, CryptoStopper.io performs against a malware attack by TeslaCrypt. In the demonstration, we illustrate how quickly a server running CryptoStopper.io can isolate and shut down a workstation after the workstation has been infected with TeslaCrypt. Check out the video below to see how you can save your work from being completely infected and potentially destroyed with ransomware.

