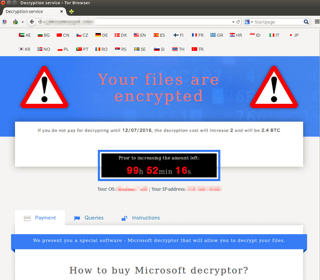
 Over the last two months, CrypMIC ransomware has emerged as a copycat of the extremely successful CryptXXX ransomware. While the most likely scenario is that the makers of CryptXXX are looking to cash in by making improvements to CrypMIC, some believe there may be a different group of hackers responsible for the variant.
Over the last two months, CrypMIC ransomware has emerged as a copycat of the extremely successful CryptXXX ransomware. While the most likely scenario is that the makers of CryptXXX are looking to cash in by making improvements to CrypMIC, some believe there may be a different group of hackers responsible for the variant.
“On the face of it, this would seem to indicate it’s a separate group that is building off of CryptXXX and improving on it,” said Christopher Budd, Trend Micro’s global threats communications manager. There are certainly several similarities between the two ransomwares, however CrypMIC has some tricks up its sleeve, too.”
CryptXXX
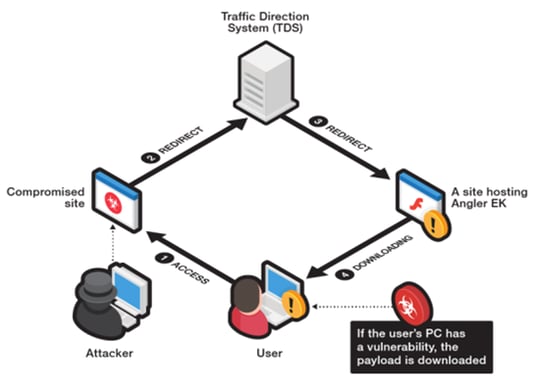
CryptXXX emerged as the most prevalent form of ransomware after the decryption key to TeslaCrypt was released earlier this year. In its early stages, CryptXXX was spread via compromised websites and malvertising hosting Angler exploit kits. Once a user visits the compromised website or clicks on a malicious ad, CrpytXXX first checks to see if it’s running in a virtual environment. If it detects this, it terminates itself. CryptXXX is extremely difficult to stop as it runs alongside a watchdog program, which means that it runs two routines simultaneously; one that decrypts and one that detects abnormal system behavior. Should the program detect abnormal behavior, the encryption process is halted and then restarted.
While CryptXXX may seem like any other form of ransomware, it also locks the desktop of the infected user. However, users can still access the pay site through the links provided in the ransom note.
The most recent form of CryptXXX, version 3.100, switched its distribution from the Angler Exploit Kit to the Neutrino Exploit Kit. The Neutrino Exploit Kit is characterized by targeting the Java Runtime Environment including Java 7 Update 11 and lower. Employing a user-friendly approach, Neutrino allows hackers to monitor and gather statistics that can be used to carry out future attacks. The exploit kit is also more affordable than its competitors, worrying many malware researchers as attacks involving Neutrino can be part of a larger and more organized attack.
CrypMIC
CrypMIC and CryptXXX share many similarities, mainly being that both are spread by the Neutrino Exploit Kit. However, the ransomwares differ in source codes and capabilities. CrypMIC does not attach an extension name to files it encrypts, making it more difficult to determine which files have been held for ransom. CrypMIC also checks for virtual machine environments and sends that information to its command-and-control server.
“Right now, CrypMIC is showing some techniques that are more sophisticated like stronger encryption, and more challenging obfuscation techniques,” said Budd.
One of the main differences between the two ransomwares is what CryptXXX became famous for; downloading and executing an information-stealing module on its process memory; meaning that CrypMIC doesn’t steal credentials and related information from the infected machine.
Here is a link to a table that represents the similarities and differences between CrypMIC and CryptXXX.
CryptoStopper.io
At WatchPoint, we have a solution to protect you from the prevelant threat of ransomware. CryptoStopper.io monitors your shared files and detects and isolates the attack the moment ransomware hits your netowrk. An alert is sent to the administrator, and the host is disconneted from the server, minimizing any damage before encryption takes place.
While it is important to put as many barries in place to prevent malware from hitting your network, there is nothing that can keep you 100% safe. Prevention is key, but protection is a must. Check out CryptoStopper.io to see how WatchPoint can protect your business from ransomware.

