Contrary to popular belief, Black Friday is not the busiest shopping day of the year. In fact, it is the third busiest, ranking behind Super Saturday and the day after Christmas. Super Saturday is the Saturday before Christmas and this year, it is Christmas Eve. The majority of people shopping on Christmas Eve or Super Saturday are probably guys who are getting last-minute gifts for their significant others. The day after Christmas is reserved for women looking to cash in on some of the biggest deals of the year (I can say this because my fiancée hasn’t bought a single thing for our wedding since everything will be at least 50% off on Dec. 26th).
All joking aside, with the significant increase in the volume of shopping, cybercriminals are hoping to see a major payday through several attack vectors. Below, we describe cybersecurity threats to look out for to ensure you aren’t giving cybercriminals their Christmas presents this year.
Ded Crypto – The Christmas Ransomware
In late November, we released an article on Ded Crypto Ransomware, which has been dubbed as the Christmas ransomware due to its ransom note which includes an evil-looking Santa. Ded Crypto is a ransomware variant that targets both Russian and English-speaking victims. Once installed, the user’s desktop will show the ransom note below. The ransom for Ded Crypto is two bitcoins which equates to roughly $1,500; quite the payday for cybercriminals.

Cerber Ransomware
The group behind the Cerber Ransomware has launched a spamming campaign targeted at holiday shoppers. Using fake credit card reports, the cybercriminals trick users into opening a Word file that will download and install the deadly Cerber Ransomware. Below is an email used in the spam campaign, which pretends to be pending payments for MasterCard credit cards.
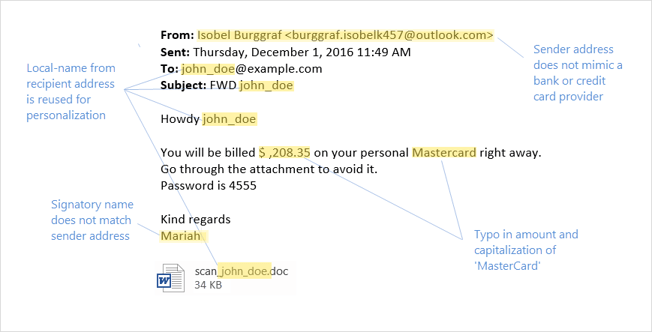
The email’s clever design plays on everyone’s fear of getting billed for something they didn’t purchase. Using a sense of urgency by saying the user’s card will be billed right away, the email tricks victims into opening a password-protected Word document that contains instructions on how to cancel the charge. The usage of a password-protected file really takes this ransomware campaign to another level. First, most banks now send customers password-protected files, which makes the emails look even more legitimate. Second, email scanning systems and anti-malware products can’t open the email’s attachment to scan it for malware.
Upon opening the Word document, users will see instructions made to look like a Microsoft tech support page, instructing the user to Enable Editing, which allows the macros embedded in the file to execute. Once users allow the macro script to execute; the macro runs a PowerShell script that downloads and installs the Cerber Ransomware, which immediately encrypts the victim’s files.
Point of Sale Threats During the Shopping Season
Point of Sale (PoS) malware is designed to steal customer data from payment cards and has rapidly evolved since its inception. While PoS malware is hard to detect during normal shopping days, it’s particularly difficult to detect when the volume of sales increases exponentially during the holiday season. The most common methods of distributing PoS malware is through inside jobs, phishing, social engineering, and vulnerability exploitation. Key PoS threats are described below:
- PoS RAM Scraper – This PoS threat is exactly what it sounds like. PoS RAM scrapers steal payment data such as credit card track one and track two data from the RAM of PoS systems. The payment card industry has a set of data security standards known as PCI-DSS. These standards require end-to-end encryption of sensitive payment data when it is transmitted, received, or stored. This payment data is encrypted in the PoS’s RAM for processing, and the RAM is where the scraper Using regular expression searches, they harvest the clear-text payment data and send that information to the cybercriminal’s servers.
- PoS Skimmers – This technique involves placing a device called a ‘skimmer’ into a retailer’s card payment system to steal data. PoS skimmers mainly get into distribution through insider threats. Retailers unknowingly buy compromised PoS systems that are pre-installed with skimmers, which results in customer data theft each time a transaction is made. Updated skimmers are equipped with text notifications that send the data to cybercriminals each time a transaction is made on the compromised PoS system.
Unfortunately for customers, there’s essentially nothing you can do to protect yourself from becoming a victim of PoS malware. It’s up to the companies using PoS systems to protect their systems from being infiltrated by cybercriminals.
As for the ransomware, there are several steps you can take to protect your network from these attacks. However, there is only one way to stop ransomware that doesn’t require constant administration of updating things like whitelists or software restriction policies and doesn’t rely on signatures like antivirus. The solution is CryptoStopper. Cryptostopper was developed by WatchPoint, and it uses deception technology in the form of watcher files placed in your important network shares. CryptoStopper continuously monitors the watcher files for the encryption process to start and will identify the ransomware attack in seconds. CryptoStopper will immediately isolate the infected workstation from the network and shut down the workstation immediately. Lastly, it will send you an email notification letting you know a ransomware attack has been discovered and contained.

