 Hacking-As-A-Service and downloadable exploit kits have given rise to offensive hacking. These services allow less savvy hackers, known as script-kiddies, to carry out sophisticated attacks that would have otherwise been well beyond their technical reach. With these services, the work of a single malware developer can be shared amongst thousands of his/her minions and carried out on millions of vulnerable systems.
Hacking-As-A-Service and downloadable exploit kits have given rise to offensive hacking. These services allow less savvy hackers, known as script-kiddies, to carry out sophisticated attacks that would have otherwise been well beyond their technical reach. With these services, the work of a single malware developer can be shared amongst thousands of his/her minions and carried out on millions of vulnerable systems.
This rise in offensive attack power has brought about a resurgence in Deception
Technology. Deception Technology deals with what happens after an intruder has entered the network. Once a hacker has gotten past your defenses and is inside the network, then what do you do? That’s where Deception Technology comes into play. It provides an additional layer of security that isn’t covered by traditional prevention-based solutions. Even though you won’t find Deception Technology on your audit sheet, it should still be part of your overall security strategy.
In this article, we’ll explore HackTraps, which is WatchPoint’s deception platform for businesses.
Why use Deception?
Deception is as old as time, from the Garden of Eden to Sun Tzu, and even in WWII where the United States military used dummy tanks to deceive Hitler and his army. Deception has been used over and over again because it’s a tried and true method against an attack.
What are HackTraps?
HackTraps address what happens after an intruder has gained access to your network. Once a hacker has gotten past your defenses and is on the inside, you need a way to detect their presence and shut them down. The HackTraps provide the simple detection-to-notification bridge for those situations when intruders are pilfering the network, and searching for sensitive information.
The HackTraps are a series of decoys, designed to entice the hacker and alert you to their presence. It builds on the idea of hiding-in-plain-site, which is one of the main strengths of using the HackTrap system. The HackTraps go right alongside your regular data. No additional hardware or software is required. You generate the HackTraps from our online portal, and then you deploy them throughout your entire network. In fact, you can get a free DocTrap just for registering a free account on our HackTraps server.
The HackTraps themselves can take many forms, including the most common forms of data that you’d find on almost every network. It’s probably easier to see the HackTraps than have me explain them to you. A full list and description of the available HackTraps can be viewed in the illustration below.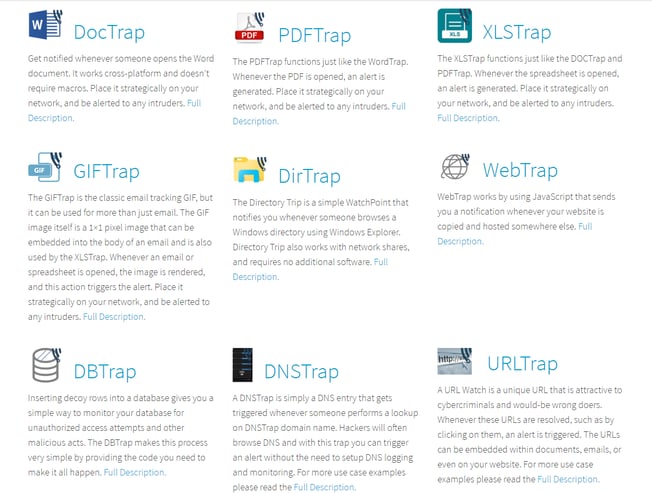
How Does It Work?
The process is pretty simple. This isn’t meant to be a comprehensive how-to-guide, but rather it’s an introduction to the HackTraps control panel and how the HackTraps can be used.
- First, register for a free account at https://hacktraps.watchpointdata.com.
- You’ll then be presented with the HackTraps generator page.
- Enter an email address and a description for the HackTraps, for example ‘san-francisco-domain-controller’ or maybe just ‘server.'
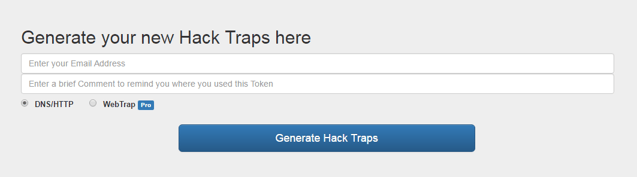
- Once you click generate, you’re presented with the list of available HackTraps:
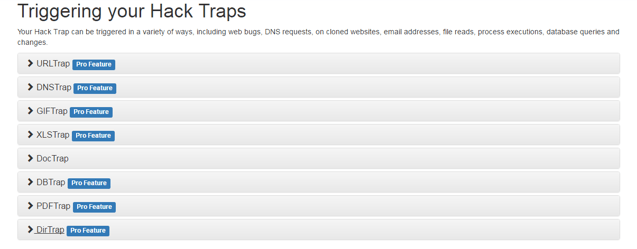
- To help you get started, each HackTrap comes with a description and possible use cases. Let’s look at a few examples below.
Examples:
Sensitive Files Alert
The HackTraps are all scenario based, so you get to be creative about how you deploy them! In this scenario, we have a sensitive folder called banking. This folder will definitely be targeted by a hacker, so we’ll deploy a bait file for them to access. Again, the idea is to hide-in-plain site, so along with our actual banking documents, we’re going to place a HackTrap there as well.
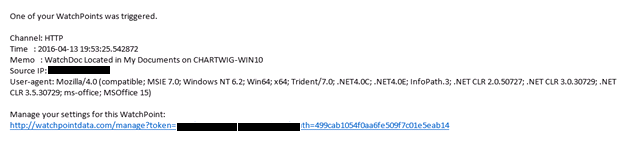
In this example, The DocTrap will provide us with the bait file we need, because whenever this file is read, we’ll get an alert.
- The following document sits in the My Documents Folder
- As soon as this document is read, an alert is received in my inbox. No macros are used, and the alert is triggered no matter where the document is opened.
Directory Browse Alert
For the last example, we’ll set up an alert for any time that directory is browsed. To do this, simply download the DirTrap that you generated from the portal and save it anywhere you’d like. In this example, I saved it to my desktop and renamed the folder to ‘Banking.'
Once the ‘Banking’ folder is opened I immediately get the following alert:

Conclusion
While Hacking-As-A-Service and downloadable exploit kits have allowed hackers to reach more targets, the average time to detection for a data breach is still over six months for most businesses. This is in part due to the fact that hackers can advance their position on the network, without tripping any sensors or alarms. More often than not a workstation is compromised first, and then the hacker pivots to the more critical areas of a network, like servers and databases. The HackTraps provide an additional line of defense, by providing the necessary sensors and alarms, that alert you to a hacker’s presence.


