A new ransomware that appends .wallet to the end of encrypted files has appeared over the last couple of weeks. After further research, it has been determined that this is a newer variant of CrySiS ransomware called Dharma.
CrySiS and Dharma Ransomware
In November 2016, the master decryption keys for CrySiS were released. When master decryption keys are released, the specific ransomware variant is essentially dead. However, very few cybercriminals are just going to stop producing ransomware variants. Enter, Dharma. Dharma is a variant of the CrySiS family, which is a high-risk ransomware virus.
Following successful infiltration, Dharma uses asymmetric cryptography to encrypt stored files. Asymmetric cryptography, in simple terms, uses public and private keys to encrypt and decrypt data. The keys are large numbers that have been paired together but are not identical, hence asymmetric. This type of encryption converts data into a format that is unreadable for unauthorized users, allowing it to be transmitted without anyone decoding it back into a readable format, thus encrypting the data.
Like the vast majority of ransomware variants, the malware appends an extension the end of encrypted files. The first two forms of Dharma either appended .dharma or .onion to the end of encrypted files. The newest version of Dharma appends .wallet to the end of encrypted files. Once the files have been successfully encrypted, a text file named README.txt will be placed into each folder that contains compromised files.
Compared to the newer ransomware variants that we have seen in 2017, Dharma looks like it’s from the Stone Age. As we can see from the text file and ransom note below, the developers of Dharma didn’t care to make this a sophisticated and victim-friendly ransomware.
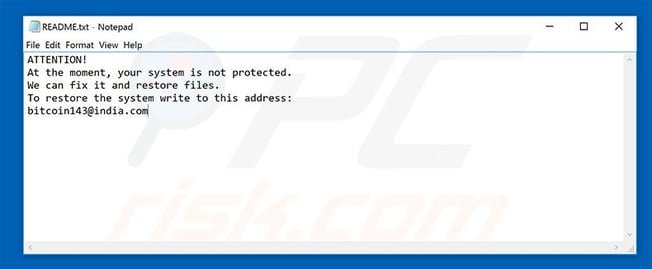
README.txt file placed in folders with encrypted files.
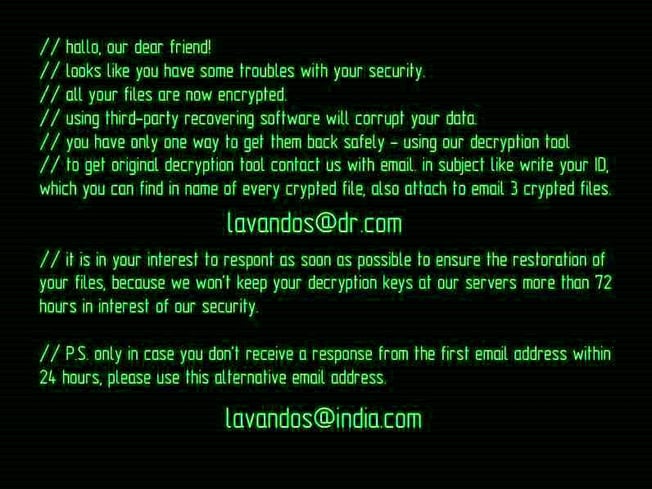
Dharma ransom note.
To gain access to the decryption key, a victim must send an email to the address provided along with three encrypted files. The developers will then send instructions on how to pay the ransom, which is currently anywhere between $500 and $1,000. Upon payment, victims will be provided with the decryption key to recover their encrypted files.
We must caution victims if they have been infected with a ransomware such as Dharma. Often the developers behind ransomware variants that don’t have a proper payment site will scam victims into paying and not provide the decryption key. Unfortunately, there is no way to decrypt files without attempting to pay the ransom or completely restoring your system from a recent backup that you (hopefully!) have. Remember though, even if you didn’t have to pay the ransom this time and were able to restore your stolen data, cybercriminals were still able to get into your systems and access your data. So even if you were lucky enough to escape the financial ramifications of a ransomware attack, the damage to your reputation could prove equally costly.
CryptoStopper by WatchPoint
At WatchPoint, we have a solution to ransomware by stopping an attack in its tracks; CryptoStopper. CryptoStopper uses deception technology in the form of Watcher Files placed on your network. The program continuously monitors the Watcher Files for the encryption process to start and will immediately identify the ransomware attack in seconds. CryptoStopper instantly isolates the infected workstation from the network, then shuts down the workstation. Upon isolating the attack, the program will send you an email notification information you that a ransomware attack has been discovered and contained. On average, CryptoStopper isolates a ransomware attack in 17 seconds, preventing all your targeted files from being encrypted and minimizing the damage done.
Contact WatchPoint today to prevent your business from becoming the next victim of a ransomware attack.

