
As users become more and more aware of malspam (malware spam), or phishing emails, hackers are finding different ways to distribute ransomware. DLL CryptoMix is the latest example of ransomware variants that are distributing its ransomware through compromised remote desktop services.
Ransomware Distributed Via Compromised Remote Desktop Protocol
While Remote Desktop Protocol (RDP) attack vectors aren’t necessarily “new,” they are gaining traction as users are becoming more educated on cybersecurity practices. In this campaign, hackers scan for machines that have their RDP ports open and exposed to the Internet. Once a vulnerable system is located, a brute-force attack is launched against the login credentials used for remote access. If the attack is successful, the ransomware will be distributed and executed on the compromised computer.
Here’s a typical scenario as illustrated by Malwarebytes Lab. Once hackers get a hold of login credentials for a remote desktop, they can deploy specialized tools to:
- Elevate their privileges
- Leave backdoors open for future use
- Gain control over wider parts of the infiltrated network
- Deploy ransomware and leave payment instructions
DLL CryptoMix Ransomware
While DLL CryptoMix is the latest ransomware variant to be distributed via compromised RDPs; it’s certainly not the first. Back in April 2018, two variants of the Matrix ransomware family were found to be using this attack vector.
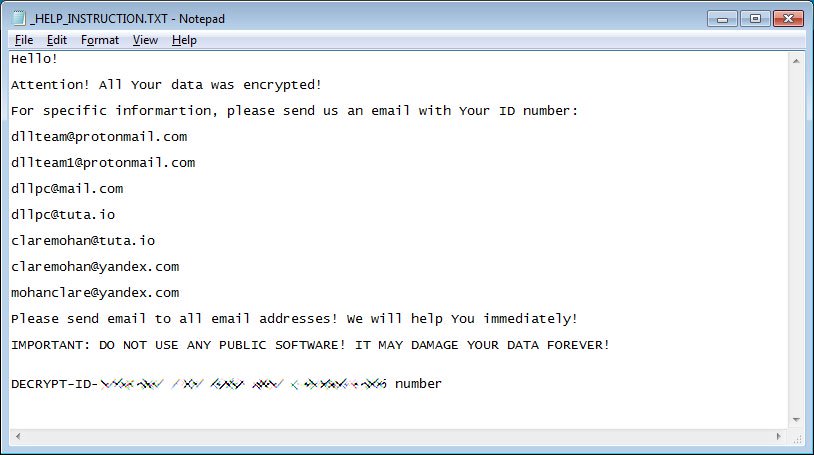
With the DLL CryptoMix ransomware, victims were infected by attackers hacking into their publicly exposed remote desktop services. According to several victims, the ransomware had also enabled the default administrator account and changed its password. With this version, when a file is encrypted, the ransomware will modify the file name and append the .DLL extension to the encrypted file. Furthermore, a ransom note named _HELP_INSTRUCTIONS_.TXT will be placed in folders containing encrypted files. As you can see in the ransom note below, several email addresses are provided for infected users to contact should they need help paying the ransom. Unfortunately, the CrpytoMix ransomware is still not decryptable for free.
How to Protect Against RDP Attacks
There are three very simple ways to protect against ransomware variants that use RDPs as an attack vector.
- Lock Down RDP
- To make it harder for a brute force attack to succeed, strong passwords are a must.
- Do not disable Network Level Authentication (NLA), as it offers an additional authentication level.
- Change the RDP port or use a Remote Desktop Gateway Server. By changing the RDP port, port-scanners looking for open RDP ports will not find yours. Using a Remote Desktop Gateway servers allows additional security benefits such as two-factor authentication.
- Limit access to specific IP addresses if possible.
- Patch
- There are several possibilities to elevate user privileges on Windows computers, but all of the known methods have been patched. As always, ensure your systems are up-to-date with the latest patches to prevent privilege elevation.
- Only allow remote access to those who need it
- First, remove the “Administrators” group from the “Allow log on through Remote Desktop Services” policy and do not grant access to any account with the username “Administrator.” The Administrator login is the account hackers are looking for as they can escalate privileges through this account and gain access to whatever they please.
- Once the Administrator account is taken care of, add the users you specifically want to have remote access and ensure they only have the rights they need – nothing more.
- Secure your network
- Secure your network from both the inside and outside. We should assume that you have your business network secured from the outside. However, in the context of RDP attacks, it’s important that you apply internal safety measures. Use restrictive policies to keep possible damage at bay that any user, not just remote, can do.
While ransomware attacks via RDP aren’t revolutionary, they are gaining traction. As more and more individuals become aware of cybersecurity threats, hackers are going to become more sophisticated in their attacks. Ransomware attacks using RDPs as attack vectors could be the next vulnerability hackers are looking for to compromise your systems.
Ransom note photo courtesy of BleepingComputer
Headline photo courtesy of SC Magazine

