New variants of ransomware appear all the time. 2017 however, is spitting out new variants with characteristics the likes we have never seen before. In January, we saw Spora which has top-notch encryption as well as a payment site like never seen before, and Satan which is a ransomware-as-a-service that allows distributors to customize their own version of the ransomware. Now February officially has its first new variant of ransomware that we have never seen before, DynA-Crypt.
DynA-Crypt Ransomware
DynA-Crypt is the newest form of ransomware that not only encrypts your files but also tries to steal information from the infected computer. The ransomware is composed of numerous standalone executables and PowerShell scripts that encrypt your files while stealing your passwords and contacts, as well as deleting files without backing them up anywhere. DynA-Crypt is leaving cyber security researchers scratching their heads as it’s unknown why the creators of the ransomware would want to delete files, let alone without backing them up.
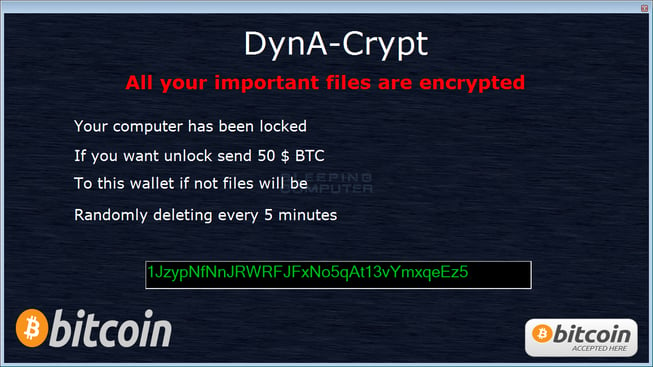
The ransomware portion of DynA-Crypt uses a PowerShell script that uses Advanced Encryption Standard (AES) to encrypt a victim’s data. The script will scan the computer for files and then append the .crypt extension to the end of encrypted files. The ransomware will also delete the Shadow Volume Copies so that you are unable to use it to recover files. When the encryption process has finished, the DynA-Crypt ransom note, as seen below, will appear. The ransom is currently set at $50 which is to be paid in Bitcoins.
While the ransomware portion is certainly a pain, as with any form of ransomware, the real problem is the data that is being stolen or deleted. While DynA-Crypt is running, the malware will take screenshots of your active desktop, record system sounds from your computer, log commands you type on the keyboard, and steal data from numerous installed programs. The programs and data that DynA-Crypt steals include: screenshots, Skype, Steam, Chrome, Thunderbird, Minecraft, TeamSpeak, Firefox, and recordings of system audio.
Once the data has been stolen, it will be delivered to the cybercriminal in a zipped folder. To make matters worse, the stolen data is then deleted for no apparent reason. The real icing on the cake is that DynA-Crypt deletes everything that was stored on your desktop, even though the malware doesn’t steal any data from there. Thanks, guys!
Outlook
Like we said before, new and more sophisticated variants of ransomware are appearing every single day. I saw a comment on an article I read the other day that really caught my attention.
“Is there any sort of preemptive actions that can be taken? I’m guessing no, having dealt with other flavors of encryption malware…”
The answer is, yes, there certainly are preemptive actions that can be taken as numerous companies have antivirus (AV) software available that are meant to prevent ransomware from infiltrating your computer. Unfortunately, because AV relies heavily upon signatures to identify malware, the software just isn’t working anymore. Cybercriminals are always finding new ways to bypass the walls put up by these AV programs. At WatchPoint, we identified this problem and developed a program called CryptoStopper.
CryptoStopper by WatchPoint
CryptoStopper is the only way to stop ransomware that doesn’t require constant administration to ensure protection and doesn’t rely on signatures like antivirus. CryptoStopper uses deception technology in the form of watcher files placed on your important network shares. The program continuously monitors the watcher files for the encryption process to start and will immediately identify the ransomware attack in seconds. CryptoStopper instantly isolates the infected workstation from the network, then shuts down the workstation. Lastly, it will send you an email notification informing you that a ransomware attack has been discovered and contained.
We host webinars on a regular basis where we show you exactly how CryptoStopper works. On average, CryptoStopper isolates and shuts down an infected workstation in less than 17 seconds. Our next webinar will be on Wednesday, February 15th. Join us to see how we can prevent your company’s network from falling victim to ransomware.
