
When the average end user discovers an injection on their system it’s more or less treated as a minor annoyance. They’ll receive a prompt - “Your Antivirus has detected (bad stuff)” and was successfully removed. And life continues on. However, a recently discovered variant has turned out to be more than just a minor annoyance. The thief of $4 million is no small feat.
A new variant of the Gozi ISFB and Hymanim malwares, known as the GozNym Trojan, was uncovered on April 14, 16 by IBM X-Force Research. The new variant is a hybrid between the two and together creates a powerful Trojan that is currently being used to infiltrate 24 U.S. and Canadian banks. The two malwares work in conjunction by relying on each other to carry out internal operations as a check and balance. As it turns out this dynamic dual has turned out to be quite the adversary. For a deeper look into the dubious malware checkout IBM’s Security Intelligence blog.
The vast majority of the targets thus far have been North American banks, credit unions, and ecommerce platforms.
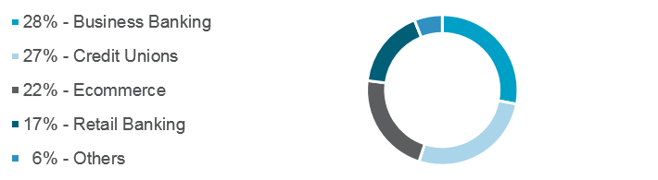
Source www.securityintelligence.com
This Trojan itself is actually targeting individuals with bank access as opposed to targeting the banks directly. The infection will usually arrive in the form of an attachment and will silently install without end user interaction. The information captured includes taking screenshots and recording keystrokes as most Trojans do. With it the user’s credentials will be captured and passed back to the malware creator. Once the creator has the compromised credential it’s just a matter of time until the funds are accessed and transferred away from the end user’s account.
The typical rules apply for keeping yourself safe from attacks of this kind. Since the infections are most commonly delivered through email, don't open links or attachments from untrusted sources. If you do know the source stop and ask yourself a simple question – am I excepting this email?

