You know things are getting serious when the Federal Bureau of Investigation (FBI) releases an article on a situation. On Friday (April 29th, 2016), the FBI released an article titled “Incidents of Ransomware on the Rise: Protect Yourself and Your Organization.”

While a significant portion of the article explains what ransomware is and how it infects your computer, it also explains how ransomware and the cybercriminals who are behind the attacks are becoming more sophisticated. Earlier versions of ransomware were delivered through spam e-mails, but because e-mail systems have become better at filtering out spam, cybercriminals turned to spear phishing e-mails targeting specific individuals.
Spear phishing is an e-mail spoofing fraud attempt that targets a specific organization seeking access to confidential data. Where regular phishing attacks use emails that appear to be from a large and well-known company, spear phishing uses emails that look like they are coming from an individual in a position of authority from within the recipient’s organization.
“These criminals have evolved over time and now bypass the need for an individual to click on a link,” FBI Cyber Division Assistant Direct James Trainor commented. “They do this by seeding legitimate websites with malicious code, taking advantage of unpatched software on the end-user’s computer.”
Recommendations:
Like WatchPoint, the FBI doesn’t support paying cybercriminals a ransom in response to a ransomware attack. “Paying a ransom doesn’t guarantee an organization that it will get its data back – we’ve seen cases where organizations never get a decryption key after having paid the ransom,” said Trainor. “Paying a ransom not only emboldens current cybercriminals to target more organizations, it also offers an incentive for other criminals to get involved in this type of illegal activity…”
What does the FBI recommend?
- Prevention Efforts – both in terms of awareness training for employees and robust technical prevention controls
- Make sure employees are aware of ransomware and of their roles in protecting the organization’s data
- Patch operating system, software, and firmware on digital devices
- Ensure antivirus and anti-malware solutions are set to automatically update and conduct regular scans
- Manage the use of privileged accounts
- Configure access controls, including file, directory, and network share permissions appropriately
- Disable macro scripts from office files transmitted over e-mail
- Implement software restriction policies or other controls to prevent programs from executing from common ransomware locations
- Business Continuity Efforts – the creation of a solid business continuity plan in the event of a ransomware attack
- Back up data regularly and verify the integrity of those backups frequently
- Secure your backups – make sure they aren’t connected to the computers and networks they are backing up.
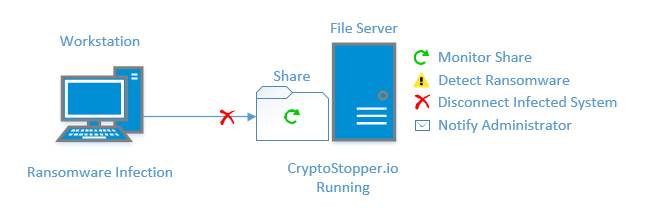
What do we at WatchPoint recommend? CryptoStopper.io; designed specifically to combat ransomware attacks.
WatchPoint has developed CryptoStopper.io to stop ransomware. CryptoStopper.io continuously monitors your system for ransomware activity. When ransomware is detected, it will isolate the offending user, notify you of the infection and prevent any damage from occurring.
Contact us today to learn how you can become protected from the ever prevalent threat of ransomware.