Ransomware attacks continue to evolve in sophistication, and one of the latest variants is tearing through Europe with lightning speed. GandCrab ransomware has affected over 50,000 users in less than one month. The infection has spread worldwide although the large majority of victims are in Europe. GandCrab is distributed through a number of fronts including through RIG and GrandSoft exploit kits, via Necurs malicious spam and via the EITest campaign that distributes the ransomware via compromised websites.
GandCrab is a Trojan horse that encrypts files on the compromised computer and demands a cryptocurrency payment to decrypt them. So far, the infections seem to be limited to Windows systems and no infections have been discovered on Mac or Linux operating systems.
GandCrab is spread by malicious advertisements on compromised websites or through email attachments with the malware disguised as an invoice. GandCrab encrypts files and appends a .GDCB extension on the end of the encrypted files and then leaves a ransomware note demanding $300 -$500 for the decryption key. The demand is unique in that it doesn’t ask for Bitcoin payment; rather it asks for DASH virtual currency as opposed to the popular Bitcoin or Monero cryptocurrencies.
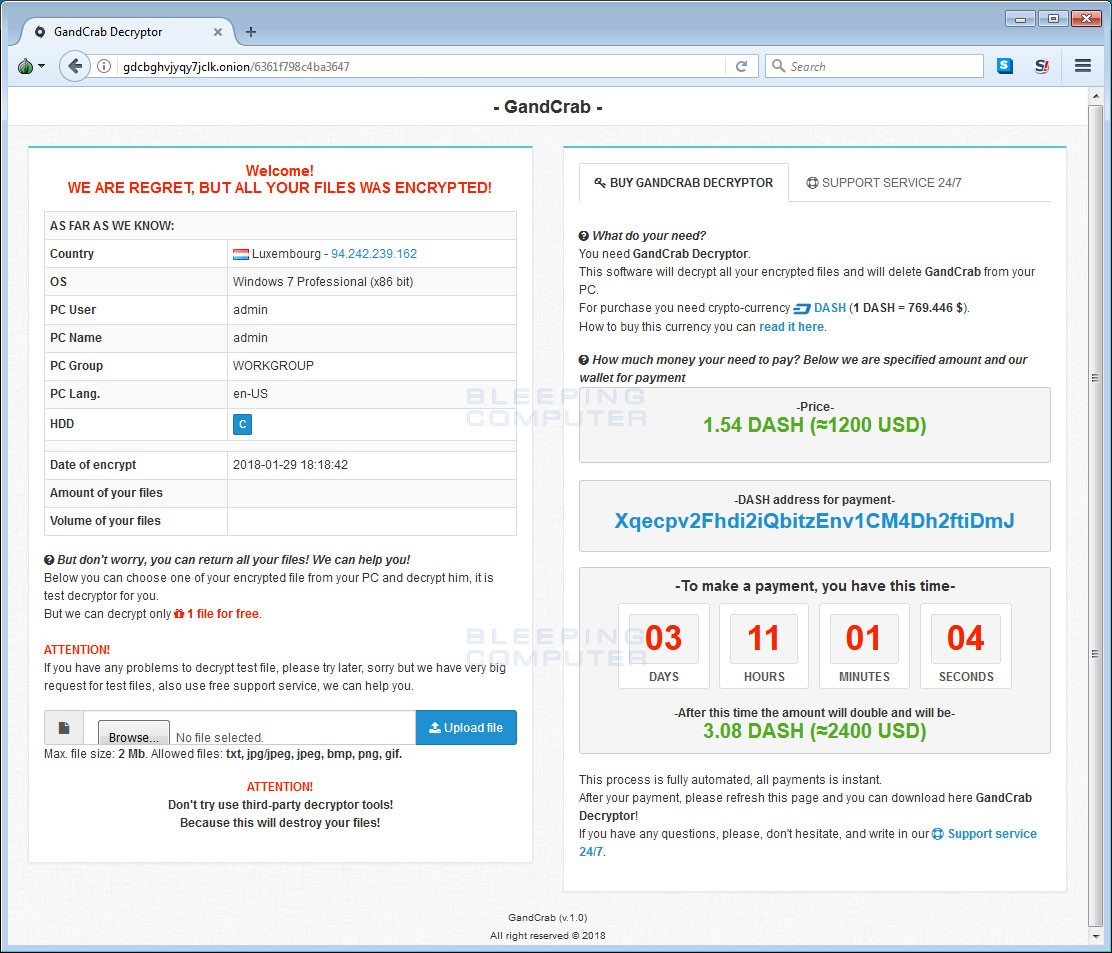 Ransomware Note for GandCrab /Bleeping Computer
Ransomware Note for GandCrab /Bleeping Computer
Developers of GandCrab ransomware have made it available as ransomware-as-a-service (RaaS). RaaS developers host their ransomware on a portal on the dark web where “affiliates” can deploy it from a user-friendly dashboard.
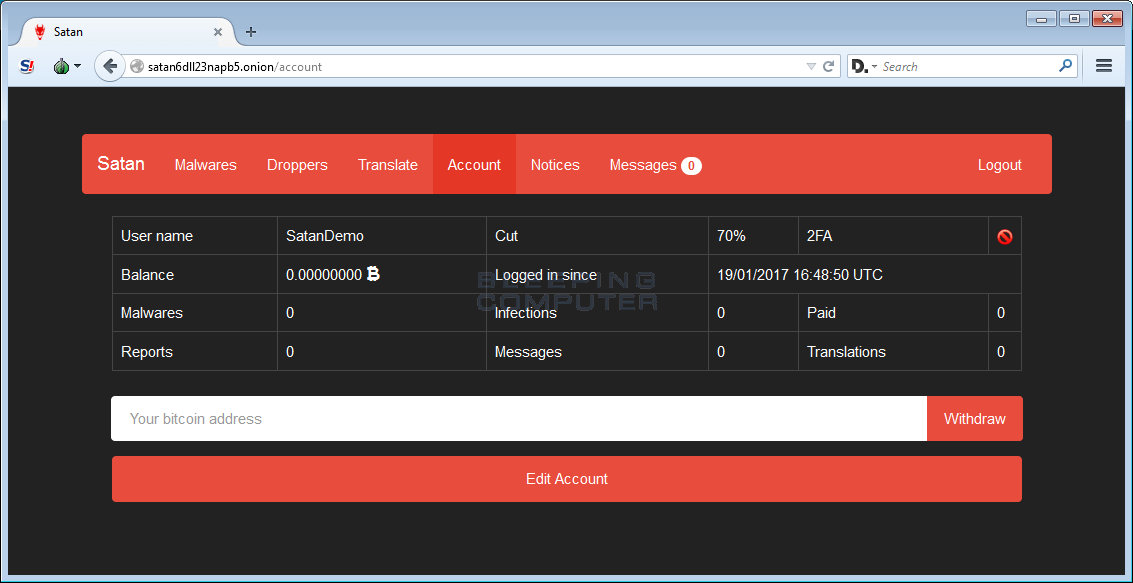 Dashboard for Satan ransomware-as-a-service. / Bleeping Computer
Dashboard for Satan ransomware-as-a-service. / Bleeping Computer
How Ransomware-as-a-service Works
Examples of Ransomware-as-a-service
GandCrab Version 1 Decryptor Available
A decryptor for GandCrab version 1 is available from NoMoreRansom. The decryptor creation was actually a collaborative effort between the Romanian authorities, Bitdefender and Europol. After the trio gained access to GandCrab Ransomware’s Command & Control servers, Bitdefender was able to recover some of the victim’s decryption keys. Bitdefender was then able to release a decryption tool that could “decrypt some victims files.”
GandCrab Version 2 Released!
MalwareHunterTeam discovered GandCrab ransomware version 2 on March 5th, 2018 after the ransomware developers vowed to continue their campaign with a second release of GandCrab that utilized a more secure command & control server. Version 2 was released with a new .Crab extension, new ransomware note, new TOR Payment Page and a few surprises even I didn’t expect…
“In the backend, the biggest change are the hostnames for the ransomware's Command & Control servers. The new hostnames are politiaromana.bit, in honor of the Romanian Police who assisted in recovering decryption keys from the original version, malwarehunterteam.bit, in honor of security researcher MalwareHunterTeam, and finally gdcb.bit” - BleepingComputer
How to Prevent GandCrab Infections
To prevent getting infected from GandCrab, users should avoid visiting untrusted sites or use a tool like virustotal.com to scan the URL for malicious content before visiting the site. You should also avoid opening attachments in email unless you are absolutely sure you know the sender and that the attachment can be trusted. One can also scan email attachments by uploading them to the virustotal file scanner.
Since ransomware commonly deletes restore points and shadow recovery backups, it’s extremely important to make sure you have a good backup and test those backups frequently. WatchPoint suggests offsite backups or completely detaching your backup drive after backups have finished. Ransomware can encrypt your backups, too so don’t leave them connected and mapped to your server or workstations when not in use. Lastly, and most importantly, it’s time to reinforce your defenses by adding a solution that detects and stops ransomware that gets past your traditional defenses. CryptoStopper can detect and stop all ransomware variants that bypass your traditional defenses like, spam filters, firewall, and anti-virus. With an average time to detection of only 5 seconds, CryptoStopper can greatly mitigate the damages of any ransomware attack.

