 I recently received an email that came into our ticketing system which at first glance seemed to be a woman submitting a resume to WatchPoint. The email was simple and introduced Charlotte Roye, who had a “Quick Question” about interning with WatchPoint. With a little scrutiny, I was able to quickly determine that this was a malicious email, and any links or attachments in the email should not be opened. This email never made it to HR, but I’m going to tell you why I think it might get through in your organization.The main reason I believe this email will reach HR and be opened by an employee is simple. I’ve recently written a blog article titled “How Many of Your Employees Will Get Phished Today?" that discussed a new study by Security Affairs. The data for the study was collected in 144 countries, and 19,000 people were surveyed. The results of the study are staggering. 97% of those surveyed failed to identify phishing emails from random samples. I highly recommend you read both articles to fully understand how badly employees fared and to see some quick tips that you should share with your employees today to help identify phishing attempts, as they come into your organization at the rate of hundreds or even thousands per day.
I recently received an email that came into our ticketing system which at first glance seemed to be a woman submitting a resume to WatchPoint. The email was simple and introduced Charlotte Roye, who had a “Quick Question” about interning with WatchPoint. With a little scrutiny, I was able to quickly determine that this was a malicious email, and any links or attachments in the email should not be opened. This email never made it to HR, but I’m going to tell you why I think it might get through in your organization.The main reason I believe this email will reach HR and be opened by an employee is simple. I’ve recently written a blog article titled “How Many of Your Employees Will Get Phished Today?" that discussed a new study by Security Affairs. The data for the study was collected in 144 countries, and 19,000 people were surveyed. The results of the study are staggering. 97% of those surveyed failed to identify phishing emails from random samples. I highly recommend you read both articles to fully understand how badly employees fared and to see some quick tips that you should share with your employees today to help identify phishing attempts, as they come into your organization at the rate of hundreds or even thousands per day.
- Only 3% surveyed identified all 10 emails successfully
- 80% surveyed got at least one wrong answer
- The worldwide average was 65.4% missing 1 out of 4 phishing attempts
Breakdown of Attack against WatchPoint
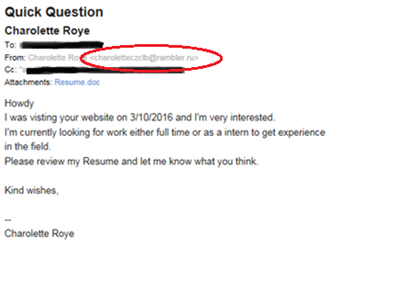 Here is a screenshot of the email as I received it. When looking at the email, there are only a couple real hints that the email is malicious. The email is nicely written with good grammar which is not typical. Most phishing attempts come from cybercriminals living overseas who have a very bad understanding of English grammar and spelling. The only item in the body of the email that really got my attention was the word “Howdy”. The word itself felt out of place in a resume introduction since it’s typically used quite casually. It’s not something I’m used to seeing in a professional resume. Since I was not expecting this email, I suspected something wasn’t right and decided to inspect it a little further. I then noticed that the email address looked suspicious. The address contains the sender’s first name but then follows it with four random characters. In addition, I’m not familiar with the top and second level domain of rambler.ru.
Here is a screenshot of the email as I received it. When looking at the email, there are only a couple real hints that the email is malicious. The email is nicely written with good grammar which is not typical. Most phishing attempts come from cybercriminals living overseas who have a very bad understanding of English grammar and spelling. The only item in the body of the email that really got my attention was the word “Howdy”. The word itself felt out of place in a resume introduction since it’s typically used quite casually. It’s not something I’m used to seeing in a professional resume. Since I was not expecting this email, I suspected something wasn’t right and decided to inspect it a little further. I then noticed that the email address looked suspicious. The address contains the sender’s first name but then follows it with four random characters. In addition, I’m not familiar with the top and second level domain of rambler.ru.
Inspect! Inspect! Inspect!
There are a number of tools available on the web that I use when inspecting emails. I’ll use a WHOIS lookup first to get some information on Rambler.ru. What I find is that Rambler.ru is registered to Rambler Internet Holdings, LLC and the IP address originates from Moscow. It appears they have been in business since 1996, so I’m not really concerned with Rambler Internet Holdings, LLC but I am very concerned about the sender because it’s safe to assume they reside in Russia and Russia happens to be one country that is constantly bombarding the United States with cyber-attacks. 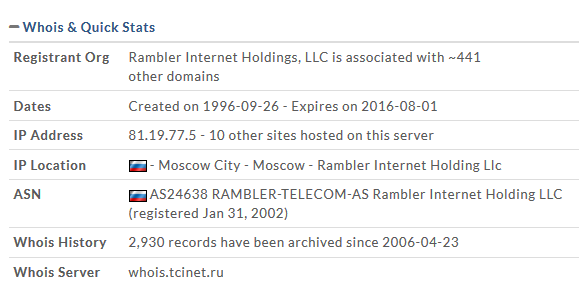
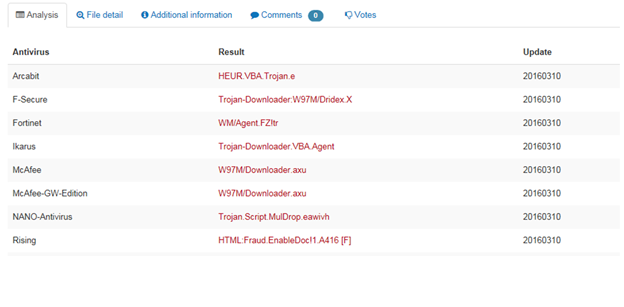
Next, I need to inspect the attachment called Resume.doc to see if there are any threats. I ran the file through virustotal.com and got some hits telling me it was definitely not a good idea to open this document.
The Rise of Banking Trojans
Very recently I wrote a couple of articles discussing the rise and fall of a very nasty banking Trojan called Dyre. You can read both of those articles here.
New Banking Trojans Emerge with the Death of the Dyre Virus
A Simple Introduction to the Dyre (Dyreza) Banking Trojan
As it turns out, this resume contained macros that would execute and download a banking Trojan called Dridex. As previously predicted; with the fall of the Dyre Virus, Dridex is in a great position to be one of the dominant banking Trojans for 2016. Banking Trojans are nasty things designed only to help cybercriminals steal YOUR money from YOUR bank account. Without a proper cyber liability policy and cyber defensive mechanisms, we are finding banks and insurance companies have no obligation to insure or refund your losses.
"2016 will be the year of online extortion." Trend Micro
The Odds are Against You
At WatchPoint, I really enjoy inspecting spam emails for malicious content and then running them in my sandbox to see what they can do. I have 15 years experience in IT and have a good understanding of what to look for when examining emails for suspicious content. I’ll all but guarantee that those in your HR department do not share those qualities. They are experts in Human Resources; not Information Technology. Your employees are the weakest link and employee education against all the possible cyber threats of the 21st century is not very strong in most organizations. I hope you are asking yourself now “Would my HR team open a phishing email?” There is a very good chance that the answer to that question is yes. The odds are against you unless you fight back with 21st Century technology like CryptoStopper. Never head of CryptoStopper? Inquire today and I’ll show you how CryptoStopper discovers ransomware that your antivirus and firewall miss.
Watch CryptoStopper Stop a Ransomware Attack

