 The security experts at WatchPoint are vigorously working to get ahead of ransomware. We constantly analyze new strains of ransomware, banking Trojans, and malware and have created a product called CryptoStopper.io and a suite of HackTraps to watch for internal and external cyber-attacks. In addition, we employ local field technicians and provide IT support to local companies. When TeslaCrypt struck a local company, we were contacted and asked to assist with their recovery. We will refer to them as Acme Insurance for privacy concerns. WatchPoint helped educate Acme Insurance employees about the breach and offered our new line of products for the customer to trial.
The security experts at WatchPoint are vigorously working to get ahead of ransomware. We constantly analyze new strains of ransomware, banking Trojans, and malware and have created a product called CryptoStopper.io and a suite of HackTraps to watch for internal and external cyber-attacks. In addition, we employ local field technicians and provide IT support to local companies. When TeslaCrypt struck a local company, we were contacted and asked to assist with their recovery. We will refer to them as Acme Insurance for privacy concerns. WatchPoint helped educate Acme Insurance employees about the breach and offered our new line of products for the customer to trial.
How TeslaCrypt Infected Acme Insurance
Investigation of the infected workstation concluded that the workstation itself was infected by a drive-by download where a malicious website exploits an unpatched browser or browser plug-in. Acme Insurance did not have an effective patch management plan in place, and most of the software on their workstations was out of date. Because of the lack of patches, the malware was easily able to exploit the browser. The drive-by download was most likely executed by the Angler exploit kit which has been used to distribute many variants of TeslaCrypt in the past.
Once the ransomware is on an infected workstation, it begins the process of encrypting all of the local files on the workstation. An executable with a randomly generated filename is placed in the user’s ‘Documents’ directory. WatchPoint discovered files with names like ilmjuhfxgces.exe and mlpqxlcamvdn.exe, which appear to be the ransomware itself. Once this file is executed, the ransomware begins the process of encrypting all of the local files on the workstation with a high level of encryption. The ransomware goes through each directory on the workstation looking for important files based on the file extension. It operates like other ransomware by encrypting files numerically and then alphabetically per directory. Once all of the target files on the workstation have been infected, it then proceeds to encrypt data on mapped network drives. Unfortunately for Acme Insurance, the infected user had access to a vast majority of the company file shares. The infection started at approximately 9 am and had encrypted the local workstation and 300GBs of data on the server before the client started to notice something was wrong.
Upon investigation, the TeslaCrypt variant was determined to be a hybrid between version 3.0 and 4.0, which was something WatchPoint had not encountered previously. TeslaCrypt 4.0 is characterized by its RSA 4096 bit encryption, and interestingly this variant does not rename the file extensions on encrypted files. In the following screenshot, you can see the characteristic black background of the 4.0 variant.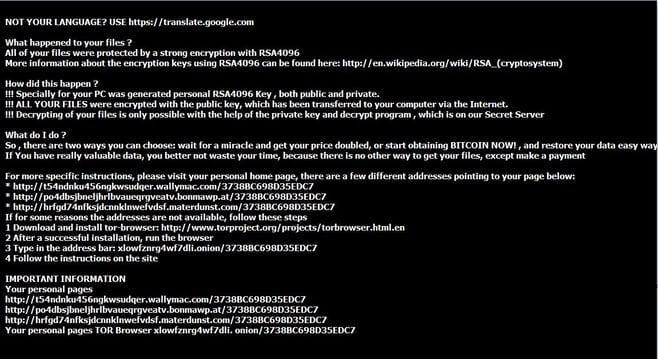
TeslaCrypt 3.0 is known to rename file extensions on files it encrypts, however, its ransom note is named “_H_e_l_p_RECOVER_INSTRUCTIONS[3 random characters].”
The variant encountered in this scenario used RSA 4096 bit encryption however its ransom notes are named “_ReCoVeRy_+[5 random characters].html or png, and txt.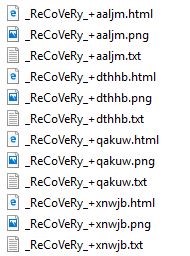
TeslaCrypt 3.0 renames all of the file extensions to “.mp3”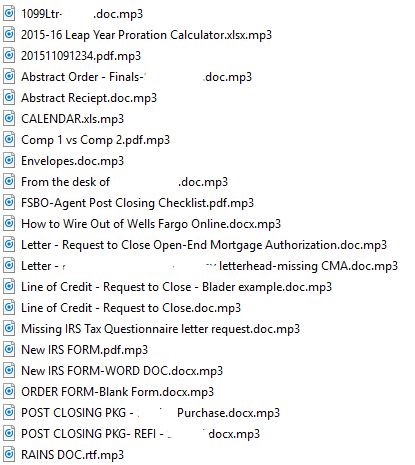
Registry Entry Created by TeslaCrypt
“HKCU\Software\Microsoft\Windows\CurrentVersion\Run\_[random] C:\Windows\SYSTEM32\CMD.EXE /C START %UserProfile%\Documents\[random].exe”
This specific entry is a characteristic of TeslaCrypt 4.0, furthering the evidence of a 3.0 and 4.0 variant hybrid.
Backups Are Critical In a Ransomware Attack
Fortunately, Acme Insurance had been backing up all of their files offsite so all of the data could be restored to the previous day. The ransomware infection cost Acme Insurance over 24 hours of downtime, and a loss of reputation as customers found they couldn’t have their accounts serviced. Acme Insurance’s data had to be restored as well as the infected workstation wiped and rebuilt. Acme Insurance is rather lucky that they had all of their data backed up offsite, and they caught the infection before it encrypted all of the data on the file shares. Other businesses have suffered much longer periods of downtime and suffered much more financially.
How CryptoStopper.io Stops Ransomware Attacks

One of the first questions that Acme Insurance asked was why didn’t the anti-virus software catch this ransomware? The reality is that anti-virus is signature based and can no longer keep up with current malware trends.
CryptoStopper.io was created to help businesses appropriately deal with the threat of ransomware. CryptoStopper.io is installed on the server where it creates ‘watcher’ files that it continuously monitors. If these files are modified or opened, CrytoStopper.io disconnects the network shares to the infected workstation and an alert is then sent to an administrator. This alert helps identify the infected user account and workstation.
Learn more and download a fully functional 14-day test drive. The trial allows you to simulate a Ransomware attack on your network and see the isolation process in action.
Want some one-on-one time with a WatchPoint expert? Schedule a time to talk.
Other Articles For Your Enjoyment:
Cedar Rapids-Based WatchPoint Launches New Cybersecurity Product, CryptoStopper.io
Ransomware Destroying Buisnesses; How Do You Stop It?
FBI Releases Article on Ransomware
Sextortion and the Consequences of Getting Caught With Your Pants Down


