2017 has arrived, and ransomware definitely isn’t going anywhere. In fact, ransomware attacks are expected to double compared to the numbers of 2016. While that doesn’t seem like a terrible increase, consider that ransomware attacks quadrupled in 2016. As for January, the biggest headlines for ransomware were two ransomware-as-a-service (RaaS) variants.

Ransomware-As-A-Service
Ransomware-as-a-Service allows hackers of all abilities to purchase and distribute different versions of ransomware. Creators of the ransomware receive anywhere between 5%-25% of the paid ransom while the distributors receive the remaining ransom. In January, Spora RaaS and Satan RaaS made the headlines for the newest and perhaps the most sophisticated versions of RaaS seen to-date.
Spora RaaS
Spora, the Russian word for ‘spore’ appeared on January 11th and is being compared to Locky and Cerber variants that were the most successful versions of ransomware in 2016. The most notable features of Spora are its solid encryption routine, the ability to work offline, and the most sophisticated payment site that has been seen from ransomware authors.
Spora RaaS is distributed via spam email campaigns that are disguised as invoices. As you can see from the email below, the emails come with attachments in the form of ZIP files that contain HTA (HTML Application) files. These files are embedded with malware and once opened, Spora will initiate the encryption process.
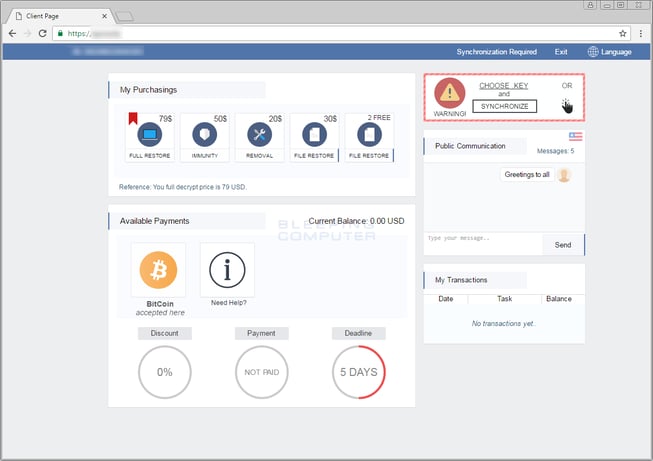
What’s unique about Spora are its top-notch encryption process and the payment site it uses. As far as the encryption process is concerned, the creators of Spora have basically added a second round of AES and RSA encryption as opposed to what other forms of ransomware have been doing up until now. As for the payment site, we can see from the screenshot below that Spora gives its victims several options for purchases they can make. These options are as follows:
- Full Restore ($79): This option will decrypt all of the encrypted files on the computer.
- Immunity ($50): Victims can purchase immunity from future Spora infections.
- Removal ($20): Remove all Spora-related files after the decryption process.
- File Restore ($30): Restore a single file.
- File Restore (2 FREE): Restore two encrypted files for free.
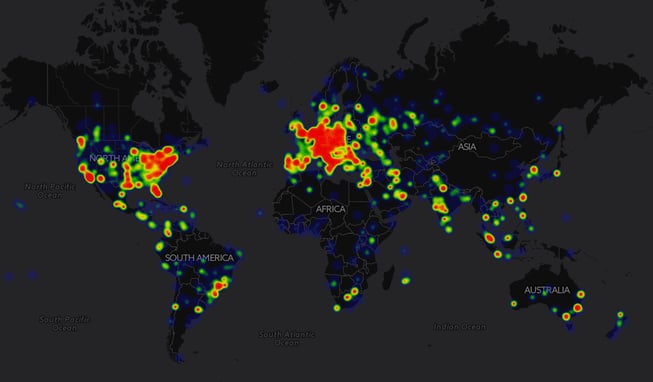
UPDATE: When Spora was first released, it was only targeting Russian users. However, as is illustrated in the heat map below, Spora has started spreading all throughout the world. The map shows where Spora had been distributed between January 17th and January 24th.
Satan RaaS
The second RaaS to appear in January was Satan. Satan RaaS allows hackers to customize their own version of the ransomware.
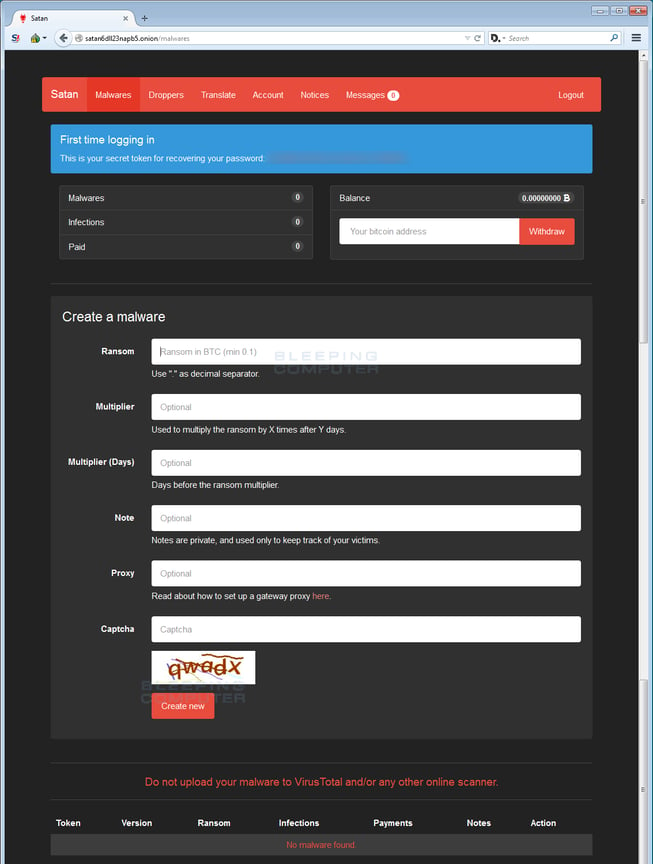
Hackers are allowed to customize the following features:
- Malware – Hackers are able to select various ways they would like to distribute the ransomware. In this tab, cybercriminals can also specify the ransom amount, how much the ransom goes up after a certain amount of days, and the number of days that the ransom payment should continue to increase.
- Droppers – Provides code that assists hackers in creating malicious Microsoft Word macros or CHM installers which can be used when distributing the ransomware through various means of the hacker’s choosing.
- Translate – Allows hackers to choose the language that the ransom note is in when distributed.
- Account – Where hackers can see the number of people infected, the amount paid, and other information.
- Notices – Displays messages that come directly from the developers of Satan RaaS.
- Messages – Used for customer service requests from the hackers to the developers.
Notable Attacks
MongoDB
According to their website, MongoDB is a free and open-source cross-platform document-oriented database program. MongoDB allows companies to build applications that weren’t possible before at one tenth of the cost compared to similar companies. On January 3rd, an attacker going by the name of Harak1r1 hijacked unprotected MongoDB databases, stealing and replacing their content, and then asked for a 0.2 Bitcoin ransom to return the data.
After finding out about the initial attack, MongoDB was able to recover the stolen files from a recent backup. However, on January 9th, it was discovered that the attacks persisted and went from about 10,000 databases stolen to over 28,000 databases. It was discovered that the databases that were attacked were those left accessible via the Internet and without a password on the administrator account. Apparently, after the initial attack was discovered, other hackers joined in on hijacking MongoDB databases. Ransom fees ranged anywhere from $150-$500 to return the stolen data, with the small fees aimed at encouraging victims to pay the ransom.
If your company has any data on the MongoDB servers, Andreas Nilsson, Director of Product Security at MongoDB, has published an updated guide on how to secure MongoDB servers. This guide is tabbed as a ‘must read’ for all database administrators.
Another Android Ransomware
Android had a rough go in December as far as cybersecurity is concerned. January looks to be no different, as a version of ransomware surfaced that locks Android phones and asks for credit card numbers. While the ransomware appears to only target Russian-speaking users, the ransom demanded is massive, asking for 545,000 Russian rubles (about $9,100). Instead of paying the ransom when infected, victims are choosing to simply purchase a new phone.
What’s different about this ransomware is that in order to pay the ransom, victims must enter their credit card information directly into the ransom screen. Typically, cybercriminals will provide instructions and a link where victims can make a Bitcoin account and pay the ransom in that form of currency. The ransomware also uses Google Cloud Messaging, which allows the hackers to send 20 different commands to the phone, including locking or unlocking the device, adding new contacts to the phone, stealing all contacts, sending text messages, or updating the malware’s code.
Just like most other forms of Android ransomware variants, this threat is likely hidden inside an application downloaded from third-party application stores. Since this ransomware gives hackers administrator rights, users have to reboot their devices in safe mode and remove the app from there.
Another form of ransomware, named Charger, was discovered in late January. This ransomware is embedded in an application named EnergyRescue which is designed as a battery-saving application. Charger secretly steals a victim’s text messages and contact list and then locks the device. Since the ransomware has been found, Google has removed the application from the Google Play Store.
Los Angeles Community College District Pays Huge Ransom
Last but certainly not least in the most notable ransomware attacks in January, is the ransomware attack on the Los Angeles Community College District (LACCD). According to LACCD officials, the ransomware attack occurred on December 30, 2016. While it’s unclear the type of ransomware that infected the network, it is clear how much was paid.
After infecting the LACCD network with ransomware, hackers gave them one week to pay. The school district decided to pay the ransom of $28,000 to quickly recover access to their systems and data, limiting the amount of damage and data lost from the attack. The $28,000 of ransom paid made this the most expensive ransomware attack to-date.
Decryption Keys
We want to make sure that anyone who has been infected with ransomware is aware of decryption keys that have been released. Decryption keys are the only way you can recover your files without paying a ransom or without completely wiping your computer clean and restoring it through a (hopefully) recent backup.
- Globe Ransomware (Version 3) – The decryption key for version 3 of Globe Ransomware has been released. Follow this link to download the decrypter and recover your encrypted files.
- Merry Christmas or Merry X-Mas – Christmas-themed ransomware variants were huge in the month of December. The decryption key for Merry Christmas or Merry X-Mas ransomware can be found here.
- Marlboro Decrypter – Marlboro ransomware was short-lived as cybersecurity researchers defeated and released the decryption key less than 24 hours after discovery.

