March was a month where a lot of small ransomware variants appeared but never came to fruition. There was, however, an update on CryptoLocker making its return, Cerber added a couple of new features, and Android ransomware appears to be here to stay. We also have a list of decryptors that were released, enabling you to recover your files without paying the ransom.
CryptoLocker Making a Return
CryptoLocker was one of the first well-known ransomware variants that appeared back in 2014. Towards the middle of 2015, the ransomware slowly started dying off to the point where it was barely distributed anymore. Fast forward to the beginning of February 2017; we are now seeing CryptoLocker make a strong comeback. The chart below shows the spike in CryptoLocker activity in February and March.
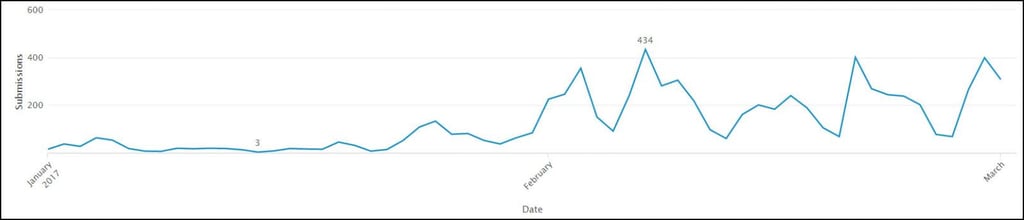
This form of CryptoLocker appears to be targeting European countries. The ransomware is being distributed via SPAM emails masquerading as invoices. We have seen this delivery method over and over, but it appears that it’s still working. The invoices trick users into opening the attachment to see what they owe. However, opening the file sends the ransomware into action, installing the malware and encrypting your files.
Unfortunately, there is no decryptor available for CryptoLocker.
Cerber Updates
Since Cerber Ransomware was first released in March of 2016, it seems like the developers have been making updates to the malware almost every month. The ransomware would not only encrypt your files, but it would annoyingly encrypt the file names as well, making it difficult for users and administrators to determine which files were actually encrypted.
The Cerber update for this month is the ransomware no longer encrypts the file name and only appends a random extension to the end of encrypted files. Cerber’s ransom is currently set at 1 Bitcoin (about $1,180) but increases to 2 Bitcoins if the ransom isn’t paid within five days.
Ransomware-as-a-Service
You heard it here first: 2017 is the ‘Year of Ransomware-as-a-Service.’ Ransomware-as-a-Service (RaaS) allows cybercriminals of all abilities to access the framework and a complete guide on how to distribute ransomware. March saw two new forms of RaaS appear, File Fozr and Karmen as well as an interesting statistic on how big Spora has become.
File Frozr is a new form of RaaS that is currently being sold for .009 Bitcoins or approximately $100. The RaaS has a pretty compelling sales pitch:
‘File Frozr is a great security tool that encrypts most of your files in several minutes. Fast, stable, and affordable crypto-locker. Auto-buy, low price, undetectable load while working, TOR support, 250+ extensions, unmatched support, multithreaded, online builder, server side obfuscation. Bypass BitDefender and Malwarebytes Anti-Ransomware. Encrypts user data using safe implemented AES-256 and RSA-4096, each file encrypts with its own unique key.’
The File Frozr homepage is shown below.
Karmen appeared on March 17th and seems to be targeting English and German users. The RaaS is much like the newest variants in that it allows the distributor to customize their own version. Providers of the RaaS however, seem to charge one of the largest cuts from attacks, demanding 20% of all profits made from ransoms paid.
Karmen runs an executable that is disguised as a program named ‘Helper’ with the description ‘Microsoft Helper.’ Of course, Karmen does not help in any way rather it starts the installation and encryption process. The ransomware targets several files including images, videos, and documents of various types; appending .grt to the end of encrypted files. As we said before, Karmen targets English and German users as the ‘Karmen Decryptor’ page is available in both languages.
Speaking of Ransomware-as-a-Service, we have some statistics on Spora. Spora made waves in the cybersecurity scene when it appeared in January 2017. Nearly three months later, the RaaS has encrypted over 48 MILLION files. That’s right, Spora is encrypting at least 16 million files per month, 4 million files per week, or over 550,000 files a day.
Spora RaaS is popular among cybercriminals as it provides a simple distribution method, top-notch encryption, and a one-of-a-kind payment site that gives victims several options they can purchase. Click here to read our full analysis on Spora RaaS.
Android Ransomware
Android has been getting rocked by ransomware and other forms of malware for quite some time. March has been no different for the Google operating system that has nearly 80% of the mobile market share.
On March 10th, two undisclosed companies discovered that 38 devices used by their employees had been compromised somewhere along the supply chain. The devices were infected with Loki adware/infostealer and Slocker mobile ransomware. Loki is an extremely powerful malware that can gain root privileges and infect Android’s operating system core processes. Loki is mostly used as an infostealer to gather data from infected devices which can be very problematic for these companies who have been breached. Slocker, on the other hand, is a ransomware that locks devices using AES encryption and talks to its Command & Control servers to transmit data.
At this time, it is unsure whether these two companies were specifically targeted or if it was a random act of cybercrime.
An unnamed form of Android ransomware that targets Russian users was discovered on March 31st. The ransomware can evade detection on all mobile antivirus programs and lacks basic decryption functions. Meaning, users infected with the ransomware cannot unlock their phones even after paying the ransom.
The crooks behind this threat are using third-party stores to spread the ransomware. When users install the application, it waits four hours before bombarding the user with popups asking for administrator rights. While you could usually close popups, these are un-dismissable and pop up repeatedly until the application gets what it wants. Once administrator rights are granted, the ransomware locks the user’s screen and demands 500 Russian rubles ($8-$10). To convince the victims to pay, the ransom note threatens to send a text message to all their contacts, telling their friends the victim was caught watching illegal adult materials.
Decryptors
The following decryptors were released in March:
- Dharma Ransomware
- CryptON Ransomware
- Damage Ransomware
- Hermes Ransomware
To access these decryptors and the largest list of decryptors on the web, visit WatchPoint.

