Twitter, Reddit, Spotify, Etsy and what seems like an endless list of websites were down for an extended amount of time on Friday (Oct. 21) due to a Distributed Denial of Service (DDoS) attack on Dyn. According to their website, Dyn is a cloud-based Internet Performance Management (IPM) company that provides unrivaled visibility and control into the cloud and public Internet resources. Dyn’s platform monitors, controls and optimizes applications and infrastructure through data, analytics, and traffic steering, ensuring traffic gets delivered faster, safer and more reliably than ever.
The attack that crippled servers across the United States was the result of a sophisticated, highly distributed assault that involved tens of millions of IP addresses and malicious software. While the investigation is still on-going, Dyn confirmed that one source of the traffic for the attacks were devices infected by the Mirai botnet.
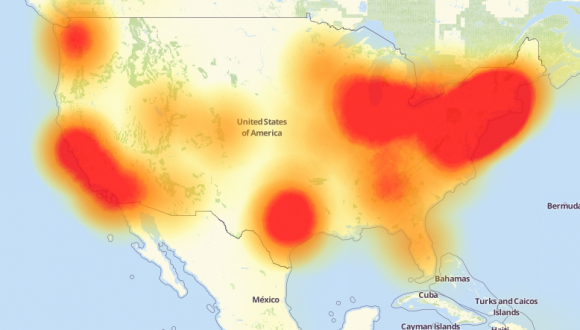
Below is a heat map displaying the areas most affected by the DDoS attack on Friday, Oct. 21st.
Mirai Botnet
The Mirai botnet is a malware designed to take control of the BusyBox systems that are commonly used in Internet of Things (IoT) devices. BusyBox software is a lightweight executable capable of running several Unix tools in a variety of POSIX environments that have limited resources, making it an ideal candidate for IoT devices. Basically, Mirai scours the web for IoT devices protected by little more than factory-default usernames and passwords, and then enlists the devices in attacks that hurl junk traffic at an online target until it can no longer accommodate legitimate visitors and users.
In the attack against Dyn, Mirai compromised digital video recorders (DVRs) and IP cameras made by a Chinese hi-tech company called XiongMai Technologies. The components that XiongMai make are sold downstream to vendors who then use it in their own products.
“It’s remarkable that virtually an entire company’s product line has just been turned into a botnet that is now attacking the United States,” said Allison Nixon, director of research at security firm Flashpoint. “At least one Mirai (control server) issued an attack command to hit Dyn.”
Longterm Outlook
The Mirai botnet has given us the first real glimpse into the power of an IoT botnet and the damage that can be done. With patching being unfeasible for most devices, there is no easy fix in sight. It is believed that, because there was no real damage done, this DDoS attack was just a test run for a future and potentially much more damaging attack.

