A new ransomware called Mole has been found, and it appears to be a version of the CryptoMix family. Additionally, Mole has many similarities to the Revenge and CryptoShield variants which are also members of the CryptoMix strain.
Mole Ransomware Distribution
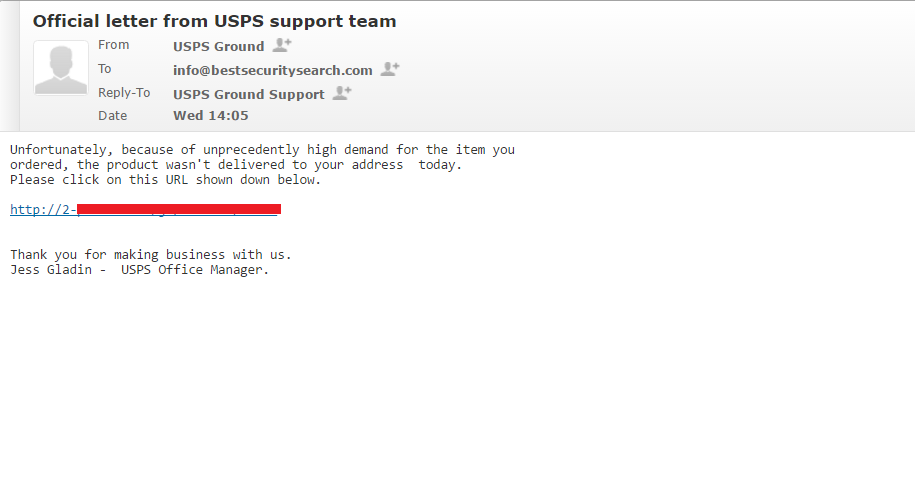
Like most ransomware variants today, Mole is being distributed through SPAM email campaigns. As we can see from the email below, this campaign poses as an email from the USPS Ground service notifying the recipient that their package cannot be delivered.
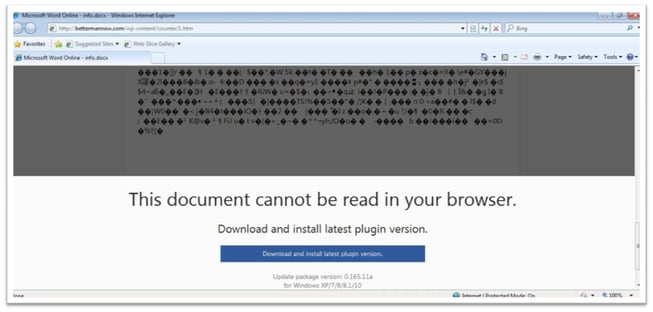
The process Mole goes through is unlike any other we have seen as it includes several steps for the malware to be installed. Furthermore, Mole goes through another process to gain administrative privileges on the victim’s computer. First, the user must click on the link provided in the email. Upon clicking on the link, the user will be directed to a fake Microsoft Word Online site that displays a supposedly unreadable document (see image below). The user will be prompted to download and install the latest version. Should the user click on the download button and execute the process, Mole ransomware will be installed.
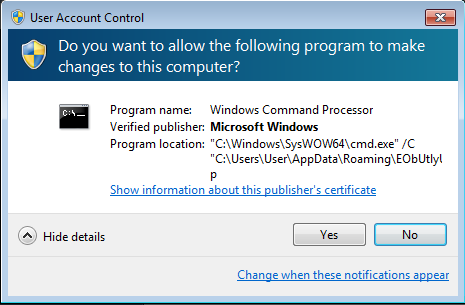
Typically, once installed, ransomware automatically starts the encryption process. However, Mole Ransomware displays a fake alert that access has been denied and the victim must click on ‘OK’ for the alert to disappear. Once the victim clicks ‘OK’ they will be presented with a User Account Control prompt, asking if they allow the command. We can see that prompt below, and if you have ever downloaded something onto your computer, this will be a very familiar process.
Once the victim clicks ‘Yes’, the ransomware will launch again with administrative privileges and generate a unique ID which is submitted to Mole’s Command & Control server. Mole Ransomware will then issue commands to disable the Windows startup recovery, which can sometimes be used to wipe a computer clean of ransomware. Mole also wipes out Volume Shadow copies, making a recovery without paying even more difficult.
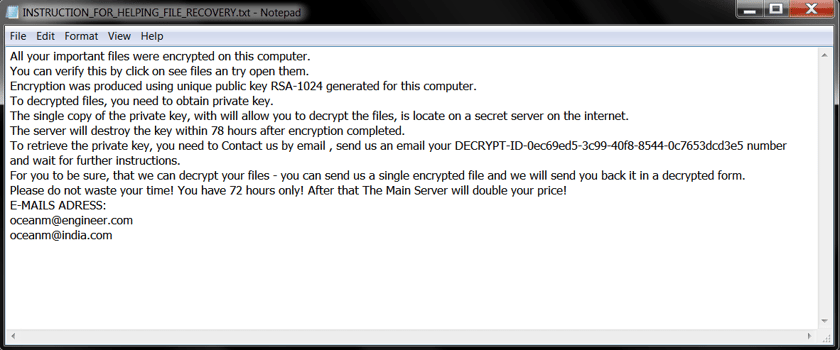
Once this process has concluded, Mole ransomware will scan the computer for targeted files and encrypt them. Upon encryption, the ransomware will append .MOLE to the end of encrypted files. In each folder that contains an encrypted file, a ransom note named INSTRUCTION_FOR_HELPING_FILE_RECOVERY.TXT will be placed that includes instructions on how to pay the ransom and recover your files. We can see this ransom note below which notifies the victim that their files have been encrypted, they have 72 hours to pay the ransom before it doubles, and two email addresses to contact for the decryption key.
Since Mole ransomware is very new to the cybersecurity scene, there is currently no way to decrypt your files without paying the ransom.

