Throughout the last couple of weeks, several new phishing campaigns have been distributed via CloudFlare’s InterPlanetary File System (IPFS) Gateway and Microsoft Azure. Also, another phishing campaign has been dropping Ursnif into conversation threads.
Microsoft Azure
A new Microsoft Office 365 phishing attack utilizes a method of storing their phishing form hosted on Azure Blob Storage in order to be secured by a Microsoft SSL certificate. Azure Blob is a Microsoft storage solution that can be used to store unstructured data such as images, video, or text. An advantage of Azure Blob storage is that it is accessible through both HTTP and HTTPS, and when connecting via HTTPS, it will display a signed SSL certificate from Microsoft. By storing a phishing form in Azure Blob storage, the displayed form will be signed by an SSL certificate from Microsoft; making it an ideal method to create phishing forms aimed at Microsoft services.
How does this phishing attack work? Attackers are sending out spam emails with PDF attachments that appear to be coming from a law firm in Denver. The attachments, named “Scanned Document… Please Review.pdf” contain a button to download what appears to be a scanned PDF document. If a user clicks on the link, they will be brought to an HTML page disguised as an Office 365 login form that is stored on the Azure Blob storage solution. As this appears to be an Office 365 login and the site is secured using a Microsoft SSL certificate, many are convinced that this is a legitimate sign-in form.
Once a user submits their login credentials, the form will submit the content to a server operated by the attackers. After the form is submitted, the user will believe the page is getting the document ready to be downloaded. However, the user will ultimately be directed to a different Microsoft site. In the end, this leaves the attacker with the user’s login credentials.
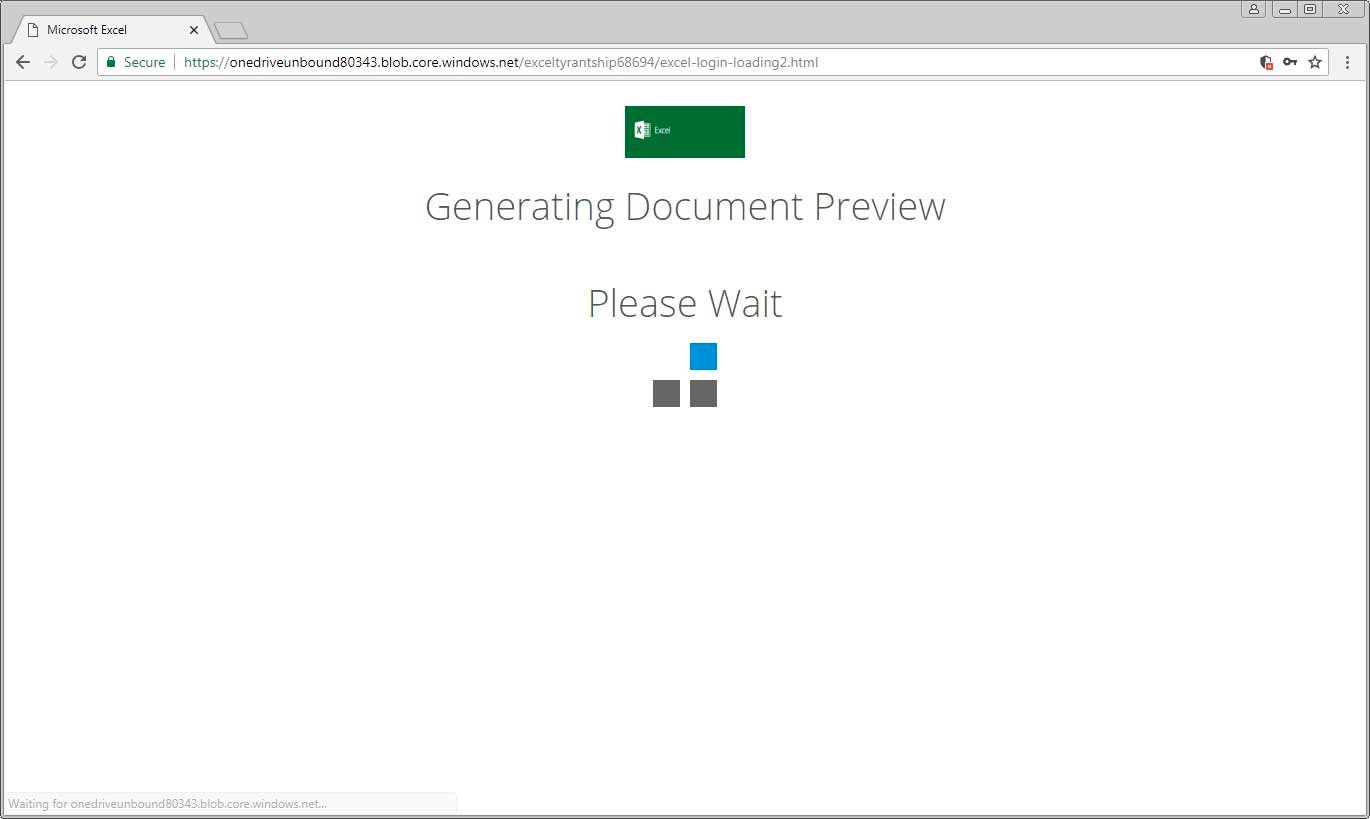
As we can see in the image above, a key to detecting and avoiding this campaign is recognizing the strange URL. To better protect users from these types of threats, companies should educate employees on how to recognize non-standard URLs.
CloudFlare’s IPFS Gateway
The Microsoft Azure and CloudFlare phishing campaigns appear to be from the same attackers as they have the exact same characteristics. In September, CloudFlare released an IPFS gateway that allows users to access content stored on the IPFS distributed file system through a web browser. Like Azure, all connections to the IPFS gateway are secured using SSL certificates issued by CloudFlare. By using an SSL certificate issued by a well-known company like CloudFlare, users believe the form is legitimate.
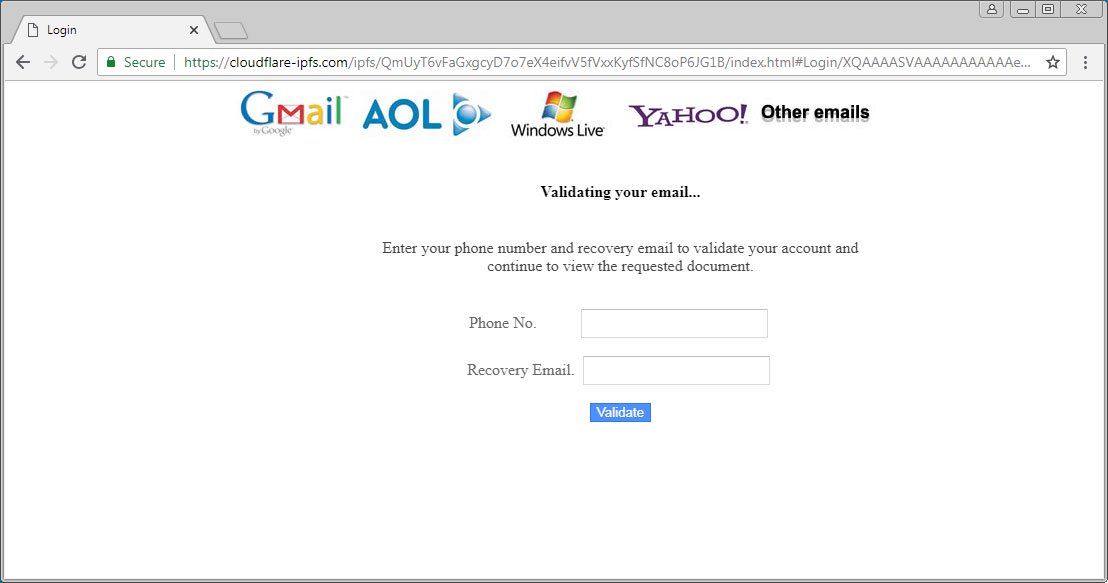
By using the form above, the attacker is requesting the user to enter a phone number and email address to validate their account. When the user submits the form, the information they entered will be submitted to a page operated by the attackers. The user will then be redirected to a random PDF document.
While nothing “malicious” really happens when the phishing attempt works, it’s likely the attackers are using the information for future attacks. With login credentials, phone numbers, and email addresses, attackers can attempt to use the information to compromise other accounts held by the users. On the other hand, the attackers could be planning further campaigns to distribute other forms of malicious content.
Ursnif
Another new phishing campaign that was spotted in September runs a banking trojan in email conversation threads. In this campaign, attackers take over email accounts and insert the malware through replies to existing discussions. This method is likely to gain a high rate of success as it relies on the familiar context the victim already trusts.
Like many phishing attacks, an email sent from the attackers contains an email attachment which, when opened, launches a routine for retrieving the latest version of Ursnif malware. Ursnif was first seen in 2017 and uses a multipurpose trojan designed to steal a wide variety of information, from banking and credit card credentials to other passwords and private information via keylogging and screenshots.
While the reply comes from someone known to the victim, there are red flags that should alert the potential victim: a sudden change of language, a generic email that doesn’t fit the wording of the sender, or an odd-looking signature at the end of the message.
As seen in the example below, the original conversation is in French while the reply with the malicious attachment is in English. Furthermore, the message is extremely simple and doesn’t have an explanation as to what the attachment includes.
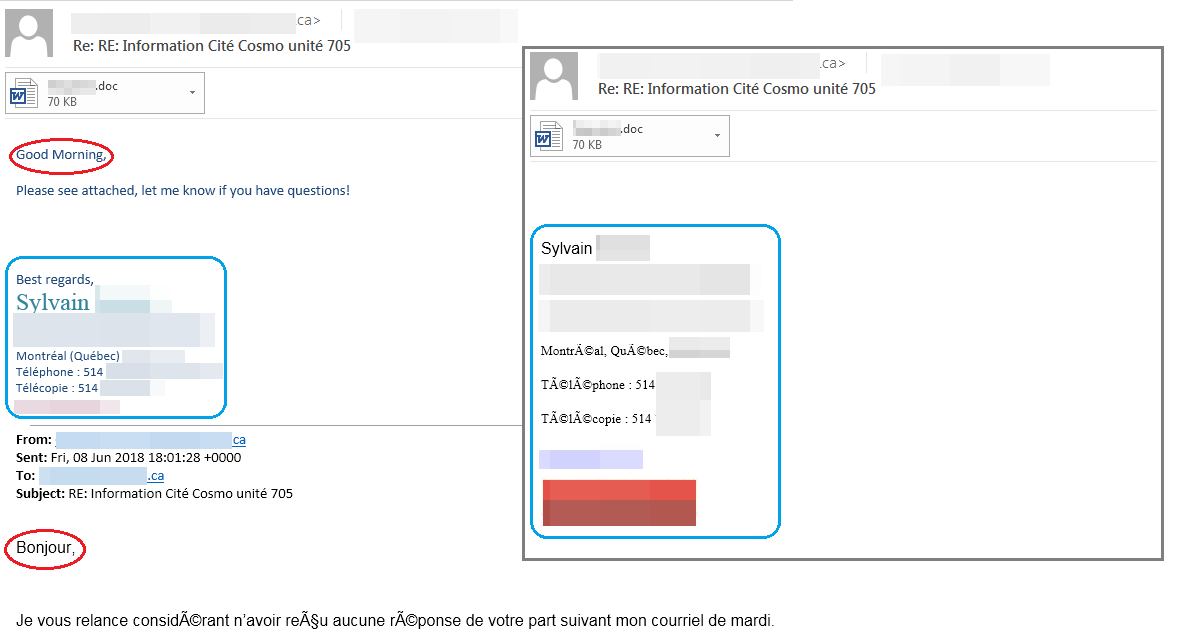
“What we can assume from the headers is that the attacker has somehow gotten hold of an authentic account and is using this account for BEC (Business Email Compromise)-like scams,” Trend Micro writes in a report.
As we mentioned before, this phishing campaign may have a high rate of success as it is very difficult to detect as it injects itself into a conversation thread. Typically, we see a new email thread started from the attackers. Again, educating your employees about these types of campaigns is key. An individual receiving this email should be alerted by the sudden change of language and should check with the sender to ensure the attachment is legitimate.

