With the daily emergence of new hacking tools such as cryptowall, ransomware and phishing attacks, it looks like hackers are hoping you forgot about a common mistake some may make daily; typing errors. We first reported about typosquatting back in 2014 but nearly two years later, it looks like a new form has come to fruition.
What is Typosquatting?
Typosquatting, also known as URL hijacking or fake URL, is a form of cybersquatting, and possibly brandjacking, which relies on mistakes such as typographical errors made by Internet users when inputting a website address into a web browser. Should a user accidently enter an incorrect website address, they may be led to an alternative website owned by a “cybersquatter.” Hackers often create fake websites that imitate the look and feel of your intended destination so you may not realize you’re actually at a different site. Sometimes these sites exist to sell products and services that are in direct competition with those sold on the website you had intended to visit, but most often they are intended to steal your personally identifiable information (PII), including credit cards or passwords.
These sites are also dangerous because they could download malicious software to your device simply by visiting the site. You don’t even need to click on a link or accept a download code to install it on your computer, smartphone or tablet. This is called a drive-by download, and many typosquatters employ this as a way to spread malicious software whose purpose is to steal your PII.

.om Typosquatting
Endgame, a cybersecurity company, recently discovered that a group of hackers has developed a new kind of typosquatting campaign that targets popular sites like Netflix, Amazon, Gmail and hundreds of others. .om typosquatting malware relies on a user’s typographical errors, specifically that the user forgets the “C” in .com. The traditional form of typosquatting relied on the user to misspell a common website, such as Google in the image above.
.om typosquatting was actually discovered by an Endgame employee who, like millions of other individuals, was thrilled by the release of House of Cards Season 4 on Netflix. By mistyping the domain www.netflix.com as netflix.om in his browser, he would expect to receive a DNS resolution error, indicating the domain typed doesn’t exist. However, due to the registration of “Netflix.om” by a malicious actor, the domain resolved successfully. His browser was redirected several times and eventually landed on a “Flash Player Updater.” Luckily, he recognized the danger and withdrew quickly to avoid harm.
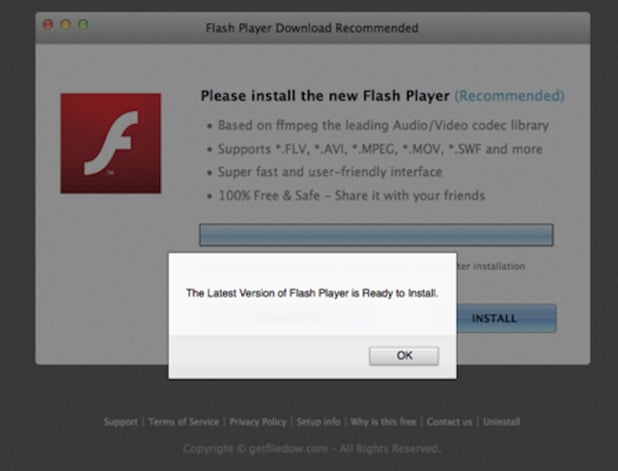
What would have happened if a typical, everyday Internet user would have moved forward with the update? Accessing one of these .om sites typically leads the user to a few different web pages in a very short time, with the final destination being one with content that may not even be relevant to the original site. Regardless of the relevance of the original site, the final destination will almost always be one with advertisements, surveys to complete for free electronics or scareware tactics to entice users to download and execute anti-virus software. The goal of these pages is to simply generate as much advertising revenue for the cybercriminals as possible. While this may seem like it would be an easy thing to ignore, researchers dug a little deeper into the malware.
Mac OS X .om Typosquatting
Cybersecurity experts at Endgame use a Windows operating system (OS) whereas the Endgame employee uses a Mac OS X at home, resulting in the different experience each had with the .om typosquatting. Through examining the .om domains on a Mac, researchers found a whole different problem. When the “Flash Player Updater” appeared and “download” or “install” was clicked, they found that a common OS X malware, adware variant called Adware Genieo was installed. Genieo is a form of adware that changes your web browser’s home page to display a personalized page, gathering information that it thinks you would be interested in. While this isn’t an issue and will not harm your computer, cybercriminals are using this as a way to generate revenue through advertisements. Each time you click on an advertisement and end up purchasing something on the page, the cybercriminal will end up making a percentage of that revenue.
As with most cybersecurity issues, typosquatting relies on the ignorance of users. Becoming educated about the ever prevalent dangers of using the Internet or even browsing emails is becoming as important as learning how to drive these days.

