
Photo courtesy of sdcexec.com
It has been over a year since phishing attacks have made significant headlines. However, phishing attacks are back, on the rise, and more sophisticated than ever. A phishing attack involves an individual (hacker) attempting to obtain user credentials, financial data, or other sensitive information by emulating a legitimate email communication. Phishing emails can also be used to trick a user into clicking on a malicious attachment or link that is embedded into an email.
On the surface, a phishing attack seems like it would be extremely easy to spot, especially in this day and age, where companies should be putting cybersecurity at the forefront of their businesses. But just like most cybersecurity threats, phishing has become more sophisticated and harder to identify with the likes of imitation websites and spear phishing.
Gmail Phishing Scam
Earlier this year, a Gmail phishing scam targeted nearly 1 billion Gmail users. In this phishing attack, hackers created email addresses to disguise themselves as someone you may know. In the email, they include an attachment such as a PDF or Word file that looks completely legitimate. However, when you open the attachment, you are redirected to the screen below.
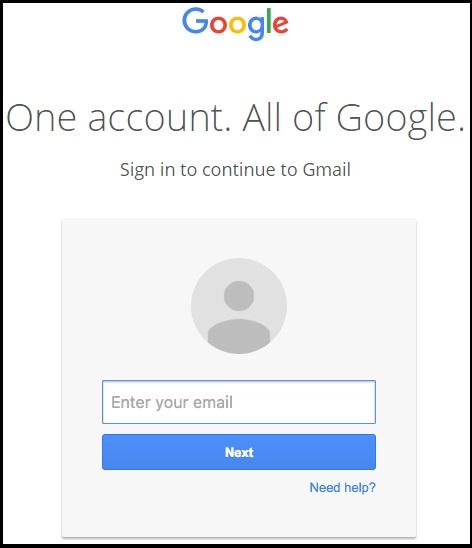
As you can see, this looks exactly like the Gmail login page; however, you can see that the URL is slightly changed. If you weren’t aware of this phishing scam, you would probably think something went wrong with the link, and you simply need to log back into your account. Here’s the thing; by entering in your login credentials, you are essentially giving the hacker access to everything included in your email or associated with your Google account.
Spear Phishing
The Gmail phishing scam is one example of a simple phishing attack. Spear phishing takes a phishing attack one step further. In this attack, the hacker really does their homework and targets a specific organization. For example, a hacker will research a company and create an email address very similar to that of the CEO or someone on the executive committee. What this does is creates a bit more urgency and increases the likelihood that an employee will click on the link. Imagine getting an email from who you think is your CEO that includes a document for an invoice that needs to be paid immediately. When you open the attachment, you are redirected to the same Gmail page above. The chances of you entering your login credentials to gain access to the document are extremely high since it “came from your CEO.”
Recent Phishing Attack
Earlier this week, Portland, Oregon-based Legacy Health began notifying 38,000 patients that a phishing attack may have breached their data. The organization hired a forensic firm to help with the investigation. It was determined that the hackers have had access into the organization since May when a hacker gained unauthorized access to several email accounts within the company. Aside from breached email addresses, hackers gained access to patient’s demographic information, dates of birth, health insurance data, billing details, medical data, Social Security numbers, and driver’s licenses.
Protecting Against Phishing Attacks
There is no tried-and-true way to prevent phishing attacks. Sure, the everyday email filter or antivirus can prevent some of the emails from ever entering a user’s inbox, but eventually, the hacker is going to get one to go through. One email is all it took for a hacker to gain access to 38,000 patient files at Legacy Health.
Fending off phishing attack essentially starts and ends with employee education. Educating your employees on the risks of opening attachments or clicking on links included in emails from someone they don’t know is the first step. Furthermore, many organizations have found success in phishing simulations where an employee from within the organization sends an email that includes a fake malicious link or attachment. Employees who click on the link are redirected to a page that explains everything that happened. After a specified period of time, the organization is made aware of the simulation. Based on the results of the simulation, the organization can determine the amount of training needed.

