Security researchers have found a new ransomware-as-a-service (RaaS) using JavaScript (JS) framework called NW.js. The new RaaS, tabbed as Ransom32, is different from other RaaS attacks as it is written in NW.js which is cross-platform in nature. NW.js, previously known as node-WebKit, allows you to call all Node.js modules directly from document object model (DOM) and enables a new way of writing applications with all Web technologies.
What is Ransomware-as-a-Service?
RaaS is a form of ransomware designed to be user-friendly; so much so that it can be deployed by someone with the smallest amount of cyber know-how. The user simply downloads the virus for free or a small fee, sets a ransom and payment deadline, and attempts to trick someone into infecting their computer. If the victim ends up paying the ransom, the original author gets a cut (usually between 5% and 20%), and the rest goes to the user who deployed the attack.
Ransom32
Ransom32 is a RaaS located on an underground TOR site available to anyone to download and distribute as long as they have a bitcoin address. The developers offering this service take a 25% cut of all ransoms paid while the distributors take home the rest. What makes Ransom32 different from other RaaS programs is that it is cross-operating system compatible. By using JS framework NW.js to infect users, Ransom32 can infect operating systems such as Linux, Mac OS-X, and Windows.
While JS programs usually can’t touch the underlying operating system, programmers have built numerous frameworks to try to give more control and interactivity to Web-based routines, such as NW.js. “NW.js allows for much more control and interacting with the underlying operating system, enabling JavaScript to do almost everything ‘normal’ program languages can do,” Emsisoft’s security expert Fabian Wosar explained.
When your computer is infected by Ransom32, the screen below shows up. It gives you four days before the ransom is raised and seven days before your personal files will be completely destroyed. As of right now, the infection comes via spam emails that trick victims into installing the RaaS.
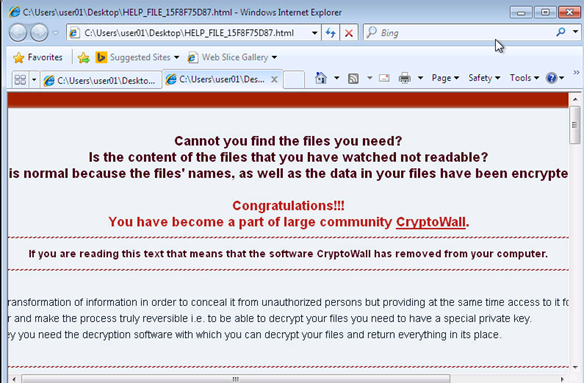
With the rise of ransomware, RaaS programs, and cyberattacks in general, we advise that you start to regularly backup your data. To take your cybersecurity to another level, look to WatchPoint to secure your network devices.

