SamSam Ransomware is ramping up attacks on hospitals and health systems in the early part of 2018. SamSam isn’t a new ransomware strain. It’s a customized version of ransomware first seen targeting hospitals in 2016. Security experts began seeing increasing numbers of attacks in late December of 2017, and have noticed a significant ramp-up in attacks during the first part of 2018.
SamSam Attack Method Doesn’t Involve the Typical Phishing Email
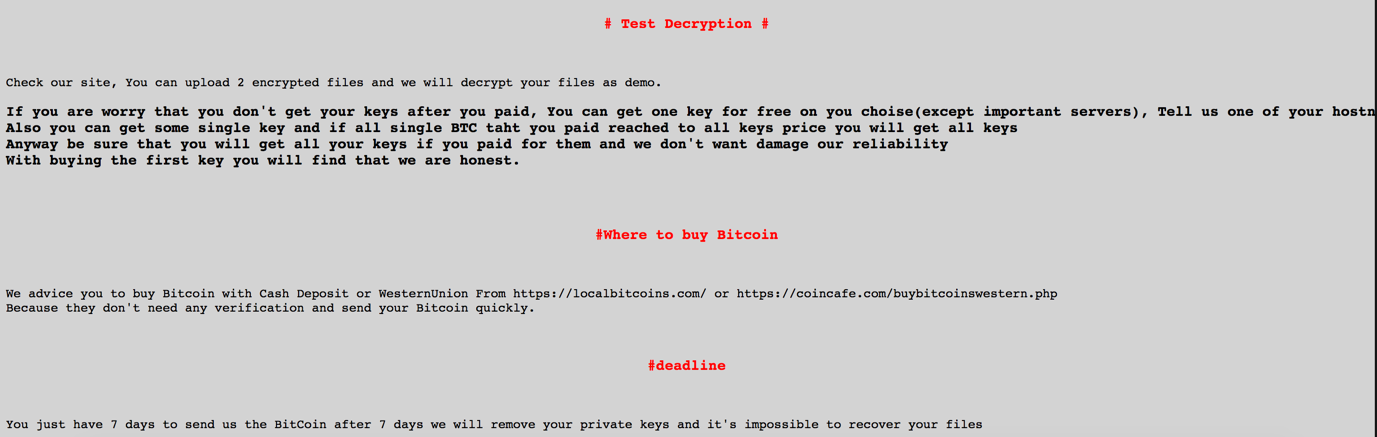
SamSam Roughs up Hospitals in Latest High Profile Attacks

Recent SamSam attacks have struck the Municipality of Farmington in New Mexico, but little was affected. Hancock Health in Greenfield, Indiana paid a $55,000 ransom after cybercriminals compromised a vendor password, leading to the exploitation and full encryption of their electronic medical records (EMR) system. Hancock Health President and CEO Steve Long had this to say about the attack. “… the attack on Hancock Health was not random; it was a pre-planned event that used the hacked login ID and password of an outside vendor to gain entrance into the system. The fact that this was a premeditated attack specifically targeted on a health care facility makes the attack indefensible in my estimation." Adams Health Network was struck by SamSam Thursday, January 11th. Hospital functions were affected, but it is not clear at this time if any patient data was compromised. Allscripts is thought to be the first Electronic Health Records (EHR) vendor infected with ransomware. An Allscripts employee tipped off a reporter at HIStalk which reported the attack shut down applications hosted on two data centers in North Carolina. The EHR platform and some e-prescribing systems were negatively affected. Allscripts acknowledged the shutdown of important systems. In a message posted to Allscript’s e-prescribe portal, the company noted it was working to restore Electronic Prescribing of Controlled Substances (EPCS) functionality. Allscripts has continued to struggle to restore systems for days. HealthcareITNews reported Allscripts was still fighting to restore all services four days after the ransomware attack. There is currently no information posted on the Allscripts website or social media platforms about the outage or how long it will be before they fully recover. There are no reports as to the number of providers impacted by the outage. It is expected to be substantial, considering Allscripts supports over 180,000 physicians, 100,000 electronic prescribing physicians, and about 40,000 in-home clinics.
How to Protect your Network from SamSam Ransomware
It’s important to tune your defenses to prevent attacks like SamSam ransomware. Since most SamSam attacks come via brute force and are known to exploit weak user passwords, the first step to protection starts with turning off RDP access if it isn’t necessary and enforcing a strict password policy that restricts the use of commonly used weak passwords. You should keep your systems patched and up to date to prevent vulnerabilities that can be exploited and a patch management system should be incorporated. Installing antivirus software on servers is just as important as having it on your desktops. Cybercriminals are less concerned about your desktops; rather they want to get to your critical servers that contain the organization’s data records. Lastly, it’s time to consider a solution to detect and stop all ransomware attacks that bypass your traditional defenses. WatchPoint created CryptoStopper to detect and stop all ransomware including known and zero-day variants. CryptoStopper does not rely on signatures that only detect and stop known threats. CryptoStopper zeros in on ransomware behavior and stops ransomware attacks that bypass your traditional security measures in seconds. You can download a free trial here and protect your network from ransomware attacks in minutes.
Further Reading:
· What to do if you're attacked by Ransomware
· NIST 800-63b Password Guidelines Surprises
· Hospital Paid the Ransom, but the Criminals Didn’t Decrypt the Files
· Using Patch Management to Keep on Top of Software Vulnerabilities

