It’s no secret that 2016 was the ‘Year of Ransomware.’ While we don’t know for certain what 2017 holds, could it be the ‘Year of Ransomware-As-A-Service?’ Over the last two weeks, two ransomware-as-a-service (RaaS) variants have made waves in the cybersecurity world. Spora, a RaaS that currently only infects Russian users was the first to be discovered. Now, Satan RaaS is the newest variant that allows cybercriminals of all abilities to infect users.
Satan Ransomware-As-A-Service
Satan RaaS, like other variants, allows hackers of all abilities to distribute ransomware. However, Satan allows these hackers to customize their own version of the ransomware. Once the ransomware is created, it’s up to the cybercriminal to decide how they want to distribute the malware although the RaaS will handle the ransom payments and the addition of new features.
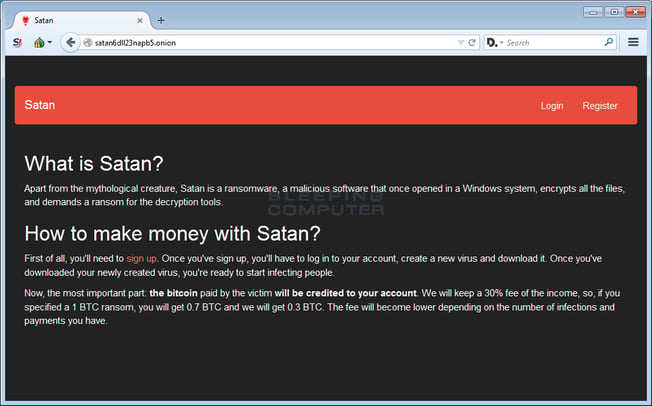
When a cybercriminal “wannabe” visits the Satan RaaS site, they will see the screen below. The site describes what Satan is and how hackers can make money from the ransomware.
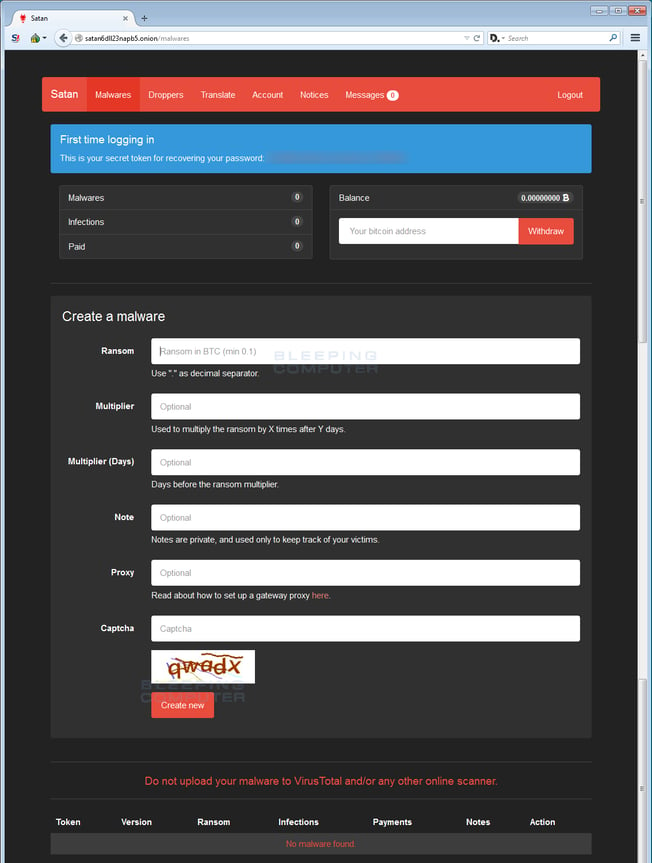
After registering for an account, hackers will see various pages that they can use to help them distribute the ransomware. The most notable tab on the dashboard is the ‘Malwares’ selection. After clicking on the ‘Malwares’ tab, hackers can select the various ways they would like to distribute the Satan ransomware. As far as customization is concerned, the hackers can specify the ransom amount, how much the ransom goes up after a certain amount of days, and the number of days that the ransom payment should increase.
Other tabs that are available for customization include:
- Droppers – Provides code that assists hackers in creating malicious Microsoft Word macros or CHM installers which can be used when distributing the ransomware through various means of the hacker’s choosing.
- Translate – Allows hackers to choose the language that the ransom note is in when distributed.
- Account – Where hackers can see the number of people infected, the amount paid, and other information.
- Notices – Displays messages that come directly from the developers of Satan RaaS.
- Messages – Used for customer service requests from the hacker to the developers.
This is the first time a RaaS that can be customized has been seen. Furthermore, Satan is also the first RaaS to provide such thorough tips and help from the creators of the ransomware when it comes to distribution methods. Usually, aspiring hackers will purchase a RaaS with specific distribution methods and means.
Satan Ransomware
As for the ransomware itself, once installed, Satan will check to see if it’s running on a virtual machine and if it is, will terminate. If the malware isn’t running on a virtual machine, the encryption process will begin and will append .stn, short for Satan, to the end of encrypted files. Once the encryption process has finished, the customized ransom note will appear, providing information on how much ransom is demanded and how to gain access to the decryption key. Also included in the ransom note is a custom victim ID and a URL to a TOR payment site.
Once the victim clicks on the URL, they will be directed to Satan’s payment site where they get instructions on how to create a bitcoin wallet, how much bitcoins are needed for payment, and where to send the payment.
Since Satan RaaS is so new to the scene, there is currently no way to decrypt the files for free. It’s also uncertain how many victims have been infected and what countries are currently being heavily targeted. However, we believe that Satan could become extremely popular with cybercriminals of all abilities with all of the customization features. With these features, it also seems like the ransomware will have no barriers to spread anywhere in the world.
CryptoStopper by WatchPoint
The threat of ransomware is not going away. New versions and more sophisticated variants are appearing every single day. There is only one way to stop ransomware that doesn’t require constant administration to ensure protection and doesn’t rely on signatures like antivirus. CryptoStopper, developed by WatchPoint, uses deception technology in the form of watcher files placed on your important network shares. CryptoStopper continuously monitors the watcher files for the encryption process to start and will immediately identify the ransomware attack in seconds. CryptoStopper will instantly isolate the infected workstation from the network, then shut down the workstation. Lastly, it will send you an email notification informing you that a ransomware attack has been discovered and contained.

