 The Internet of Things (IoT) is defined as the vast network of physical objects like cell phones, vehicles, doorbells, and entire buildings that are embedded with electronics, software sensors, and have network connectivity allowing direct integration of the physical world into computer-based systems. This integration improves efficiency, accuracy and provides economic benefits. By 2020, the IoT is projected to contain over 50 billion objects.
The Internet of Things (IoT) is defined as the vast network of physical objects like cell phones, vehicles, doorbells, and entire buildings that are embedded with electronics, software sensors, and have network connectivity allowing direct integration of the physical world into computer-based systems. This integration improves efficiency, accuracy and provides economic benefits. By 2020, the IoT is projected to contain over 50 billion objects.
All of this integration of devices into the Internet infrastructure is awesome because it provides access to all of our data wherever and whenever it’s needed. If you are at the grocery store, you can check the refrigerator to find out if you are low on milk. You can answer the doorbell to your home to accept deliveries even while you are at work. How about turning your house lights on to foil burglars while you are enjoying the Iowa Hawkeyes run into overtime at Kinnick Stadium. None of these things were possible when I was a child but the IoT has finally created the future I have dreamed about.
“The scariest search engine on the internet” - Emily Chang, Bloomberg
Risks of the IoT
The integration of devices into the Internet infrastructure does come with a lot of risks that we are just coming to terms with. If all of your devices are so easy to access for you, cybercriminals will also enjoy the ease of access when trying to exploit vulnerabilities in your devices. When you purchased your WiFi router, did you change the default IP address along with the username and password? Same question for your webcam. Did you know that if someone gained access to your network, simply inputting the default IP address of the device along with the default username and password will allow a cybercriminal administrative control of your router? Did you know that new smart refrigerator can be hacked giving cybercriminals direct access to your computer network? Any device with Wi-Fi that emits a wireless signal is beaming its information out to anyone with a little knowledge and ability to grab that data out of thin air. In this technological age, a cybercriminal can break into your home, steal your valuables and he/she doesn’t even have to step foot through your front door. The old technique of war driving still works. This is where someone drives around searching for a Wi-Fi signal and if one is found with weak or no encryption; they can park at the curb in front of that house and commence an attack. You could be cooking dinner for your children or watching your favorite episode of “The Big Bang Theory” and have no idea your data is being transmitted right before your very eyes, out your front door and into the hands of cybercriminals. Although war driving is a threat, the real threat comes from the simple fact that your devices are online, on the Internet, and a cybercriminal no longer needs to war drive to find you. One search engine that I want to share with you today is www.shodan.io.
“…I look at IP addresses, so I get the raw information from each software. I don’t necessarily care about the data that it provides, I care about the server or the device itself. So, I store information about where the device is located, what operating system does it run, what version of its software does it run. So, things about the device itself and not necessarily the data….” John Matherly, Shodan Founder and CEO
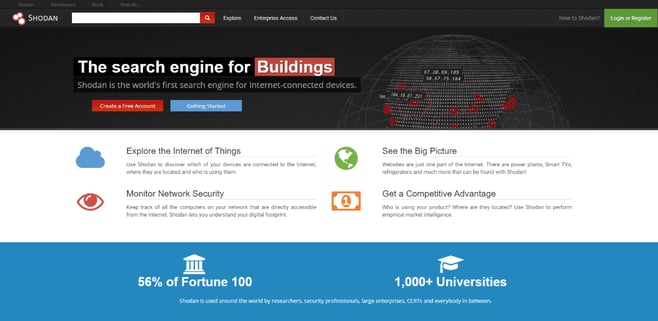
The Shodan Search Engine
Shodan is a search engine that allows you to find all kinds of devices that are connected to the internet. Even yours! In addition to the everyday electronics we take for granted, Shodan users are able to find and collect data on systems like traffic lights, security cameras, industrial control systems for water parks, gas stations, the power grid, water treatment plants, nuclear power plants and particle-accelerating cyclotrons to name just a few.
These systems typically have very light security and often times accept the default username and password that was supplied out of the box. This username and password were intended for one-time use and after logging into the device should have been changed to something more secure. Since so many devices are sold as plug and play, many people fail to understand that they have a responsibility to further secure the device before plugging it in and allowing the device to access the Internet.
Why Closing Unused Server Ports is Critical to Cyber Security
How Shodan Differs From a Typical Search Engine
In a recent interview, Bloomberg TV anchor Emily Chang described Shodan as “The scariest search engine on the Internet” and asked John Matherly, the Shodan Founder and CEO “How exactly does it work, and how are you different from what we all know; Google?” Matherly discussed the Shodan search engine and contrasted it with Google. He said that “…while Google looks at (a) subset of all the servers… (Google) only looks at websites. What I do is I look at everything else. There are a lot of different softwares that runs on Internet and Shodan looks at all of those.” Matherly continued to say “I look at IP addresses, so I get the raw information from each software. I don’t necessarily care about the data that it provides, I care about the server or the device itself. So I store information about where the device is located, what operating system does it run, what version of its software does it run. So, things about the device itself and not necessarily the data; which is something that Google provides for you.”
Matherly makes a very good distinction between Google and Shodan. Google search results provide data from web pages while Shodan gathers data on the underlying devices that make up the Internet infrastructure. That covers everything from your private home router, and Internet-enabled webcam, as well as major Industrial Control Systems and the protocols that run them.
What Can a Cybercriminal do with Shodan?
I’ve heard the question asked a lot. “What can a cybercriminal do with Shodan?” After just a few simple searches on Shodan, I was able to really understand the power of Shodan and how it could be used nefariously. The “Explore” page on the Shodan website is a great place to start discovering. There are Featured Categories of searches and queries that have been shared by the user community. In just a few clicks you can see Internet-connected webcams, 3D printers, databases and Industrial Control Systems. Here is one result from the webcam search that provides quite a visible fingerprint.
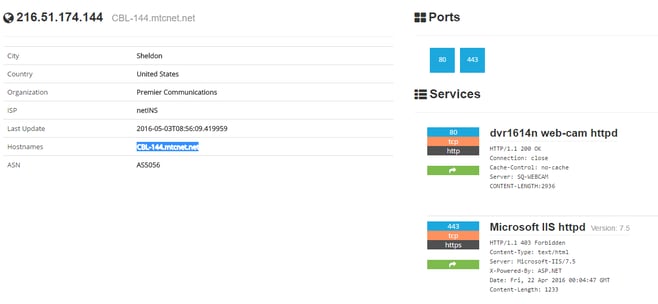
As you can see, there is a lot of information that can be used in an attack. The first thing a cybercriminal could do is throw the hostname and port into their browsers’ address bar. Once on the device’s home page, you could attempt to access the device using the default username and password.
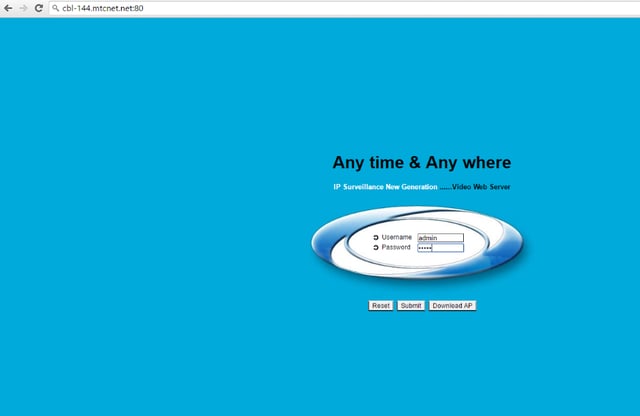
If the defaults don’t work there are a plethora of readily available hacking tools for sale on the darknet to either brute-force the password or at the least a cybercriminal could create a DoS event blocking even legitimate users from accessing and using the device.
In subsequent searches, I found unsecured routers and phone systems sending data unencrypted, which can allow for eavesdropping.
FTP port 21 is used for unencrypted file transfers. Many of these servers allowed anonymous logins which is a terrible idea. A cybercriminal could steal data anonymously from your FTP site or worse; they could upload malware to the system. Banking Trojans and Crypto Ransomware are a real problem and allowing anonymous logins and unencrypted file transfers are an open invitation to cybercriminals.
The most shocking aspect of Shodan is how easily it allows anyone access to Industrial Control Systems and their protocols. I found Netbios, Netbus, SCADA and SNMP protocols all accessible over the internet which should never happen and is extremely bad for network security. Modbus is one of the more common protocols used in Industrial Control Systems. Modbus is very easy to DoS due to the extremely small packet size. You can query these devices and send poll commands to the read and write registers which means you can configure the device or at least read the device information allowing attackers to, at a minimum, gather intelligence.
Should I be Afraid of Shodan?
Concern seems to be growing as Shodan gains visibility. The concern is valid, but a lot of the fear is very easy to alleviate. For starters, it is up to the device and software owners to secure their devices and block protocols from the Internet that shouldn’t have access. At one time, people didn’t wear seatbelts, and that was considered ok. Today we know how important seat belts are, and failure to use them can result in criminal negligence charges if an accident occurs. I think the same attention that was given to seatbelts needs to be given to network security. Experts have been warning about a major cyberattack on America’s electrical and nuclear infrastructure. Some say it could happen this year. If a concerted effort were made to secure these systems, these devices, and close vulnerabilities, the threat could easily be mitigated. We cannot allow the continued use of unsecured, unencrypted protocols nor can we allow the continued use of default IP addresses along with default usernames and passwords in our devices.
"The part that makes Shodan scary in many people’s eyes is not necessarily the search engine itself but the way that it exposes that many default configurations or many networks in general always operate under the assumption that if you don't put it on Google nobody will find it. In security terms that is known as security as obscurity and Shodan kinda blows the lid off that." John Matherly
I don’t think we should be afraid of Shodan. In my opinion, we should be thankful to John Matherly for creating Shodan and bringing visibility to the IoT. Without tools like Shodan, people will remain in the dark and will allow the problem to remain out of site and out of mind. Unfortunately, that can result in criminal negligence. If management allows systems that have critical infrastructure or national security interests to be completely accessible online without any authentication, they are as responsible for the attack as the attackers are themselves.
|
Banks Say “TOO BAD” when Hackers Steal MILLIONS from Business Accounts |
Banks and insurance companies agree. The insurance companies will scrutinize your cyberliability policy and will determine if inaccurate representations were made or if the agreed upon security practices were not followed. If it’s determined that the insured didn’t follow the security practices, the claim will likely be denied, putting the insured on the hook for the full damages of the security breach. If your bank account is robbed by a cybercriminal, don’t expect a refund from the bank. It isn’t their fault that you allowed a cybercriminal to install a Banking Trojan which initiated several wire transfers depleting your account while you were in a company meeting. The bank cannot differentiate between your legitimate transactions and those from cybercriminals when they are both initiated through the same channels. Last and worst of all, it will be a very bad day for any organization that was found to be negligent in preventing a cyberattack that caused death. An attack on as few as eight electrical substations in America could bring down the entire electrical infrastructure for weeks causing death, destruction, and chaos never before seen. I’m pretty sure once the dust settled we would see CEOs, CTOs, CIOs, network engineers, and maybe even a few politicians being sentenced to long prison terms.
Protect Your Systems Now!
Many of these systems could be secured  with a few simple firewall rules. Secure protocols could be swapped in and replace many of the unsecured, unencrypted protocols in use. Do not allow anonymous FTP access and close any unused server ports. Disconnect Internet-connected devices that you don’t want accessible on the internet and change any default IP addresses along with usernames and passwords.
with a few simple firewall rules. Secure protocols could be swapped in and replace many of the unsecured, unencrypted protocols in use. Do not allow anonymous FTP access and close any unused server ports. Disconnect Internet-connected devices that you don’t want accessible on the internet and change any default IP addresses along with usernames and passwords.
While even the best protections sometimes fail to stop zero-day threats or malware brought into the network by employees, WatchPoint does offer many solutions to help protect your network and ensure that if a cybercriminal does gain access; they will be stopped immediately. By utilizing WatchPoint tripwires and forensic collection through Carbon Black, we can detect and isolate advanced threats on your network. The forensic experts at WatchPoint work to stop any intrusion within the first hour of a cyberattack. This “Golden Hour” can make or break any forensic investigation, and it’s important to your cybersecurity and financial well-being to get it right the first time.
Contact us today to see how a partner like WatchPoint can secure and protect your network from the next generation of cybercriminals.
Here are a few more articles for your enjoyment.
How to Safely Download Software
Why you should worry about Application Security
Gone Phishing: Why Human Resources is Vulnerable to Crypto Ransomware Attacks
Why Didn't My AntiVirus Detect CryptoWall?


