
Snake ransomware is the latest example of ransomware variants being used for targeting enterprises. Snake ransomware is being used to infiltrate business networks, gather administrative credentials, and encrypt the files of every computer on a network, using post-exploitation tools. Snake joins the likes of Ryuk, Bitpaymer, and other less notable ransomware variants that take part in enterprise targeting.
Snake Ransomware
Snake ransomware, or SNAKE, is written in Golang, an open-source programming language that provides cross-platform support. Once the ransomware is installed, it removes the machines Shadow Volume Copies and terminates various processes related to SCADA systems, virtual machines, industrial control systems, remote management tools, network management software, and more. During the encryption process, Snake ransomware skips all Windows and other system folders. Compared to other ransomware variants, Snake’s encryption process is slower, potentially allowing the network admins to control the damages of the attack. However, as this is a targeted ransomware attack, the slow encryption process may not be much of a problem as it’s probably activated after hours or over a weekend. The ransomware will append ‘EKANS’ or ‘SNAKE’ backwards to each encrypted file.
When the encryption process has concluded, the ransomware will create a ransom note in the C:\Users\Public\Desktop folder named Fix-Your-Files.txt. The ransom note contains instructions to contact a listed email address for payment directions. An example of a Snake ransom note is below.
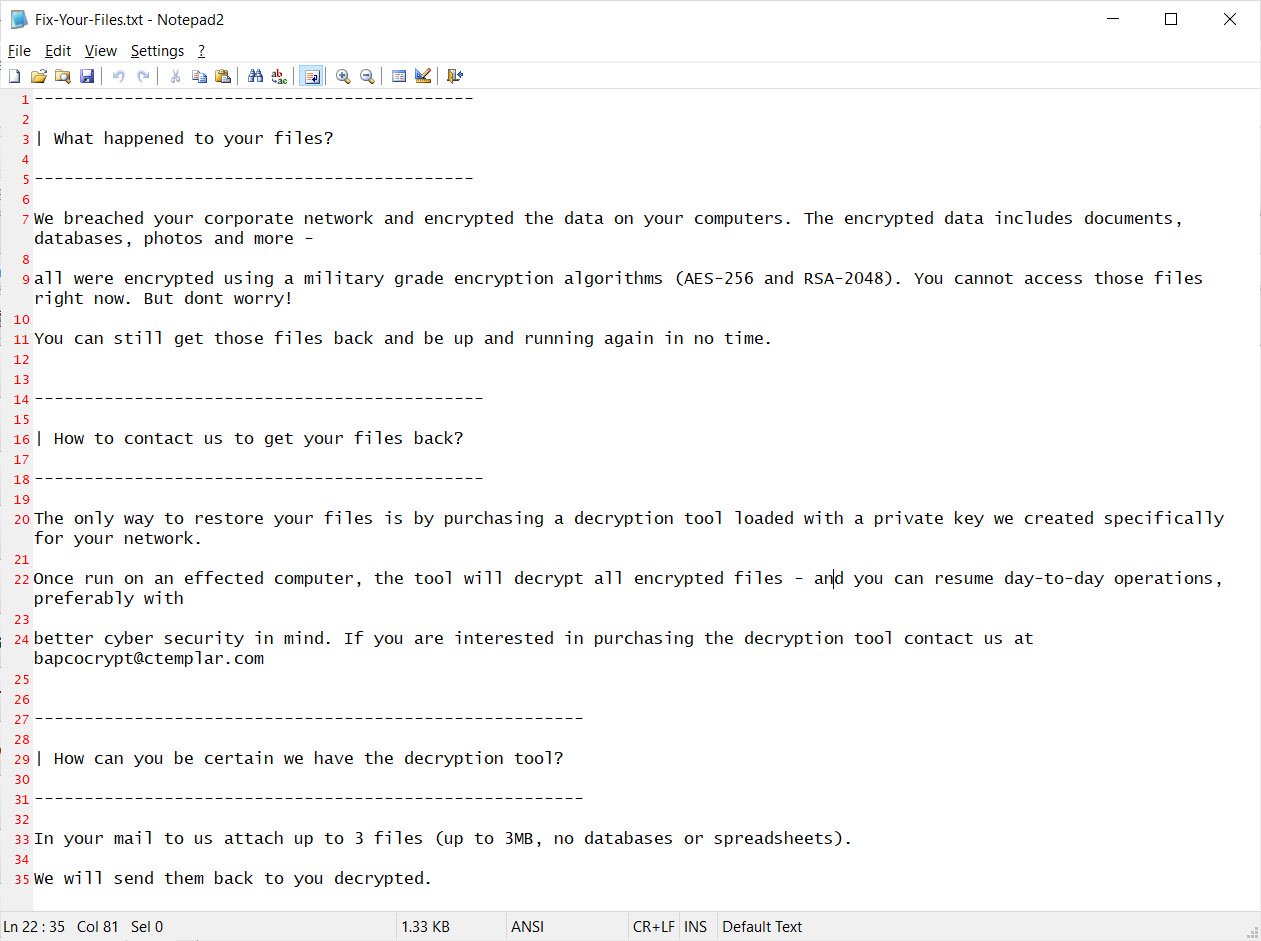
As seen in the ransom note, Snake ransomware specifically targets the entire network rather than individual machines. The decryptor that can be purchased will be for the entire network, not for individual machines.
Presently, there is no free decryption tool available, and the ransomware appears to be very secure.
CryptoStopper Protects Against Ransomware Attacks
CryptoStopper, developed by WatchPoint, can protect against Snake ransomware. CryptoStopper uses deception technology to detect ransomware. During the installation process, decoy files are strategically deployed. We call these Watcher Files. When ransomware begins the encryption process, CryptoStopper detects it in real-time and takes automated action to stop the attack in milliseconds and alerts you to the event.
Antivirus and firewalls no longer provide the protection you need to save your network from a ransomware attack.
Using deception technology and CryptoStopper is the only way to stop an actively running attack that has evaded your traditional defenses. Click here to learn more about CryptoStopper and how WatchPoint can help with your cybersecurity needs!
Photos courtesy of msspalert.com and Bleeping Computer

