A new ransomware family has recently been discovered that incorporates a combination of fileless attack and code-injection. Dubbed Sorebrect, the fileless ransomware is targeting enterprises, instead of individual users.
How Does Sorebrect Work?
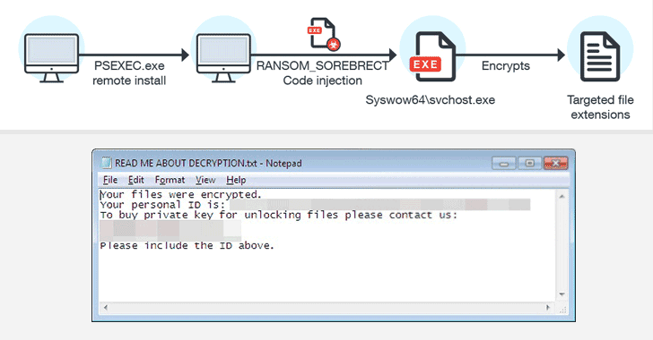
As we mentioned before, Sorebrect uses a combination of fileless attacks and code-injection to infect targeted machines. The fileless aspect of Sorebrect and other fileless malware and ransomware allows it to avoid antivirus. This is what makes fileless malware different from traditional malware; nothing ever touches your disk, which is what your antivirus is scanning.
Sorebrect injects code into a legitimate system process, svchost.exe, on a targeted system and then self-destructs to further avoid detection. Furthermore, the ransomware goes to extraordinary lengths to delete the affected system’s event logs in an attempt to obstruct forensic analysis and prevent researchers from tracking the threat’s activities.
The fileless ransomware also has worm-like characteristics as Sorebrect is designed to target company’s servers and endpoints. The injected code first initiates the file encryption process of traditional ransomware on the infected machine and then spreads to local network shares. Basically, once one machine on a network has been compromised, any machine on the company’s network is at risk of being infected as well.
Sorebrect’s Reach
It’s uncertain how many individuals or companies have been infected, however; it is known that Sorebrect is targeting systems from industries including manufacturing, technology, and telecommunications. While the fileless ransomware was initially found in the Middle East, over the last month, the threat has hit companies in Canada, China, Croatia, Italy, Japan, Mexico, Russia, Taiwan, and the United States.
Protect Your Business From Fileless Ransomware
It’s no secret that professional and amateur hackers alike are becoming more sophisticated and stealthy with their attacks each passing day. In an article we posted back in May, we discussed how fileless ransomware is becoming more popular. In fact, the distribution of fileless malware increased by 33% in the final quarter of 2016. In 2017 alone, three key fileless ransomware campaigns have hit major industries in over 40 countries.
With the emergence of fileless malware, traditional measures such as antivirus certainly aren’t enough to protect your business from becoming infected. As we have previously stated, the purpose of fileless malware is to completely bypass antivirus and other malware-scanning programs.
At WatchPoint, we have developed a product to stop attacks in their tracks; CryptoStopper. CryptoStopper uses deception technology in the form of Watcher Files placed on your network. The program continuously monitors the Watcher Files for the encryption process of ransomware to begin. The program will immediately identify the attack, isolate the infected machine from the network, and shut down the workstation. Upon isolating the attack, the program will send you an email notification informing you that a ransomware attack has been discovered and contained. On average, CryptoStopper isolates a ransomware attack in 9 seconds, preventing all your targeted files from being encrypted. Furthermore, with fileless ransomware attacks like Sorebrect, CryptoStopper will prevent the malware from spreading to other machines on your network.
Contact WatchPoint today to learn how we can help your business from becoming part of the more than 52% of businesses infected with ransomware. If you're simply wanting to learn more, feel free to read our blog.

