Spora, the Russian word for ‘spore’ is a new family of ransomware that appeared yesterday (Jan. 11). Spora is being compared to Locky and Cerber variants that were the most successful versions of ransomware in 2016. The most notable features of Spora are its solid encryption routine, ability to work offline, and the most sophisticated payment site that has been seen from ransomware authors to-date.
Spora Distribution
Spora is currently being distributed via spam email campaigns that are disguised as invoices. This is nothing new to ransomware as spam emails, especially those masquerading as invoices, are one of the most common ways for ransomware to be distributed. As you can see from the email below, the emails come with attachments in the form of ZIP files that contain HTA (HTML Application) files.
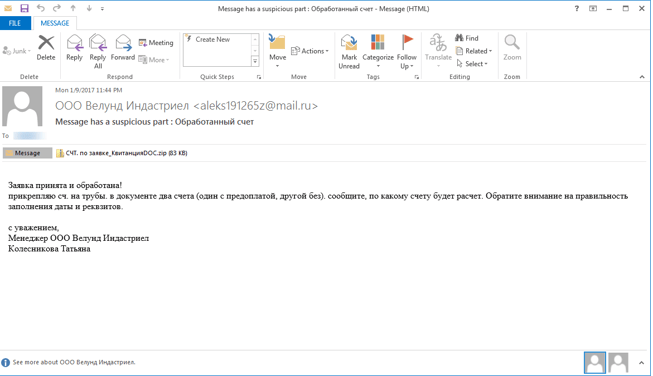
The malicious files contain double extensions such as PDF.HTA or DOC.HTA however, on Windows computers where the file extension is hidden, users will only see the first extension and might be tricked into opening the file. Launching any of the files in the attachment will start the Spora ransomware process.
Spora’s Top-Notch Encryption
As of now, Spora does not appear to have any weaknesses in its encryption process and looks to be very complicated. Traditional ransomware programs generate AES (Advanced Encryption Standard) keys for every encrypted file and then encrypt these keys with an RSA public key generated by a command and control (CnC) server. Most ransomware programs contact a CnC server after they’re installed on a computer and request the generation of an RSA key pair. The public key is downloaded to the computer, but the private key never leaves the server and remains in the attackers’ possession. This is the key the victims pay for to get access to their encrypted files.
The problem with reaching out to a server on the Internet after the installation of ransomware is that it creates a weak link for attackers. If the server is known by security companies and is blocked by a firewall, the encryption process won’t start.
Creators of Spora have found a way around this problem. While the malware does contain a hard-coded RSA public key, it is used to encrypt a unique AES key that is locally generated for every victim. This AES key is then used to encrypt the private key from a public-private RSA key pair that’s also locally generated and unique for every victim. Finally, the victim’s public RSA key is used to encrypt the AES keys that are use to encrypt individual files.
Simply put, the creators of Spora have added a second round of AES and RSA encryption as opposed to what other ransomware have been doing up until now.
Spora’s Payment Site
Once the encryption process is finished, the ransom note below will appear on the victim’s computer. However, unlike almost all other ransomware variants, Spora does not append a file extension at the end of encrypted files. Furthermore, to avoid damaging computers to the point that they are inaccessible to the victims, Spora only encrypts the following types of files:
- .xls, .doc, .xlsx, .docx, .rts, .odt, .pdf, .psd, .dwg, .cdr, .cd, .mdb, .lcd, .dbf, .sqlite, .accdb, .jpg, .jpe, .jpeg, .tiff, .zip, .rar, .7z, .backup
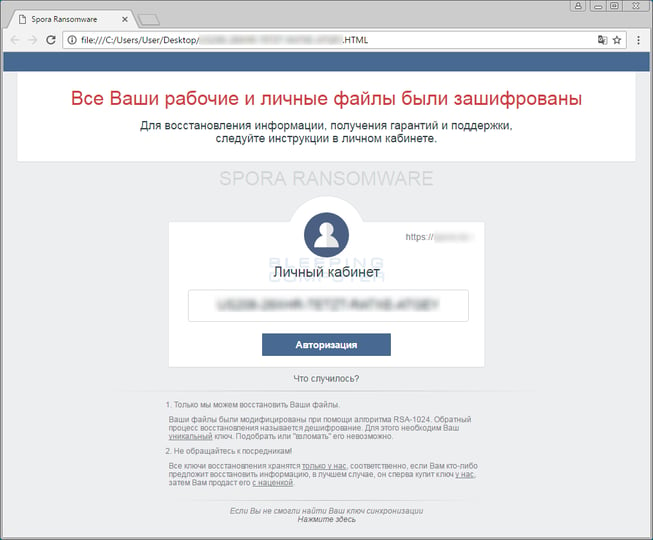
The ransom note above leads victims to Spora’s decryption portal, where users enter the infection ID presented in their ransom note. Spora’s decryption service is extremely unique and much more professional compared to other ransomware variants that we have seen. First, before using the site, users must synchronize their computer with the decryption portal by uploading the .KEY file. The .KEY file is placed on the user’s desktop along with the ransom note once the encryption process has finished.
Once the .KEY file has been synchronized, information specific to the encryption of the user’s computer is uploaded to the payment site and associated with the infection ID found in the ransom note. Victims will then be directed to the payment site, shown below.
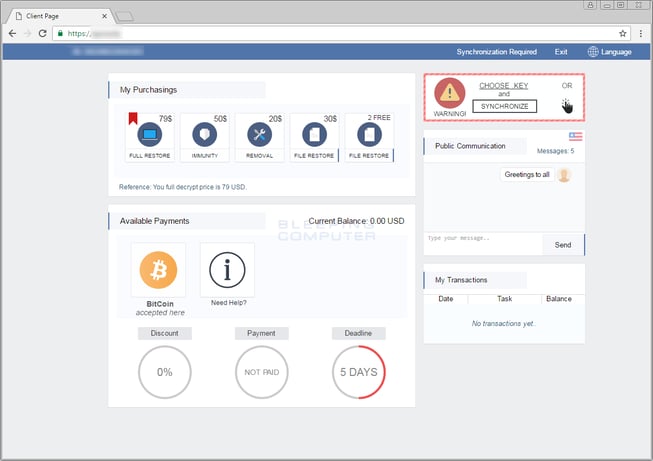
This aspect of Spora is also extremely unique as it gives victims several options to purchases they can make. These options are as follows:
- Full Restore ($79): This option will decrypt all of the encrypted files on the computer.
- Immunity ($50): Victims can buy immunity from future Spora infections
- Removal ($20): Remove all Spora-related files after all the decryption process.
- File Restore ($30): Restore a single file.
- File Restore (2 FREE): Restore two encrypted files for free.
Like most ransomware, Spora payments are made with Bitcoins. Users must upload Bitcoins into their Spora account, which can then be used to purchase any of the options above. Lastly, the decryption portal allows victims to send up to five messages to a staffed support service group within Spora’s entourage. The messaging service has allowed victims to confirm that they will receive the decryption key once the ransom is paid.
Outlook
As of now, Spora appears only to be targeting Russian users, as we can see with the email, ransom notes, and decryption portal using the Russian language. In 2016, Locky and Cerber ransomware dominated the ransomware scene. Spora appears to be as advanced and well-run as the two, and we expect the ransomware to expand to countries all over the world. We know that ransomware will continue to be a huge player in cybersecurity for 2017, and it appears that Spora is the early favorite for the ‘Ransomware of the Year’ award.

