As the CEO of WatchPoint, I believe marketing our products is an extremely important part of the success of our business. We want our customers to be aware of the many ways we can protect their cybersecurity well-being.
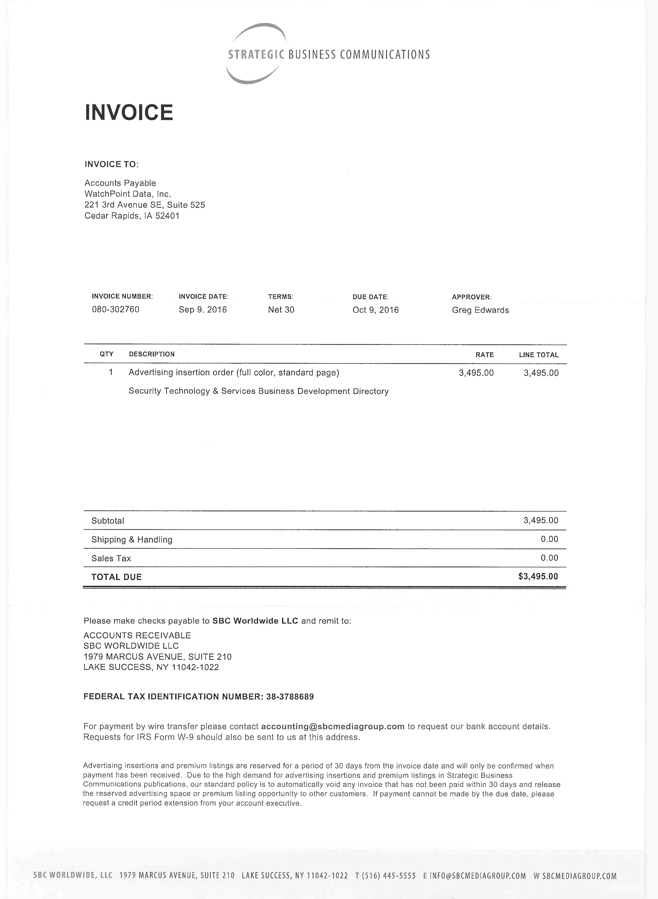
We recently embarked on a marketing campaign and received an invoice right around the time we released a press release. In the invoice below, Strategic Business Communications is asking for $3,495 for an advertising insertion order. Our accountant, who was aware of our advertising campaign, assumed we were using this company. We got so far as printing a check for my signature. However, before signing the check, I did a quick review and realized that we haven’t been using and have never used this company for our marketing.
All of the information on the invoice is publicly available, so I should not have been surprised. A quick Google search reveals this is definitely a scam.
This is a great lesson for CEOs and executives at all companies. We tend to be so vigilant with our digital lives now, but we can’t forget about the analog versions of social engineering.
What is Social Engineering?
Social engineering is a non-technical strategy that cybercriminals use that relies heavily on human interaction and often involves tricking people into breaking standard security practices. The success of social engineering techniques depends on the attackers’ ability to manipulate victims into performing certain actions or providing confidential information. Social engineering differs from traditional hacking in the sense that the attacks tend to be non-technical and don’t necessarily involve the compromise or exploitation of software or systems. When successful, many social engineering attacks enable hackers to gain legitimate, authorized access to confidential information.

Types of Social Engineering
Social engineering scams have been going on for years, and yet we still fall victim to them every single day. In an effort to spread awareness on this topic, below are the five most prevalent forms of social engineering.
- Phishing: As the leading form of social engineering attacks, phishing is typically delivered in the form of an email, chat, web ad or website and is designed to impersonate a real person or organization. These messages are crafted to deliver a sense of urgency with the end goal of capturing the user’s sensitive data. More sophisticated forms of phishing have surfaced throughout the last year, with hackers performing more research on their targets. The more sophisticated forms will include emails that appear to be from executives of the company the user is working for.
- Baiting: Similar to phishing, baiting involves offering something that is enticing to the user in exchange for login information or private data. The ‘bait’ comes in many forms, such as a music or movie download on a peer-to-peer site or in physical form like a corporate branded download such as an executive summary for the user’s company. Once the bait is downloaded, malicious software is delivered directly into the user’s system and the hacker can get to work.
- Quid Pro Quo: Like baiting, quid pro quo involves a cybercriminal requesting the exchange of critical data or login information in exchange for service. A common quid pro quo hack is when a user receives a phone call from a ‘technology expert’ who is offering free IT assistance or technology improvements in exchange for login credentials. If an offer sounds too good to be true, it’s probably quid pro quo.
- Pretexting: The human equivalent of phishing, pretexting involves a hacker creating a false sense of trust between themselves and the user by impersonating a coworker in an attempt to gain access to login information. An example of pretexting would be a user receiving an email from the IT department or a chat message from an investigator who claims to be performing an audit on the company.
- Piggybacking: Also called tailgating, occurs when an unauthorized person physically follows an authorized person into a restricted corporate area or system. Piggybacking occurs when a hacker calls out to an employee to hold the door because they forget their security card or asks to borrow an employee’s laptop for a few minutes, during which the criminal is able to quickly install malicious software.
For all employees to be aware of the various forms of social engineering is essential for ensuring corporate cybersecurity. If we all know the main characteristics of these attacks, it’s much more likely that we can avoid falling victim to them. Education and awareness is key to the cybersecurity well-being of your company.

