WannaCry ransomware took the cybersecurity scene by storm last Friday (May 12th), becoming the fastest spreading ransomware to-date. Now that it is nearly a week later, we want to provide some takeaways on WannaCry. What happened, what did we learn, and what does the future look like?
What Is WannaCry Ransomware?
If you Google WannaCry, you will find endless articles about the attacks that occurred on May 12th. The ransomware being distributed is specifically known as WannaCry 2.0, but for clarity, it is also referenced to as WannaCrypt0r, WanaCry, Wanna Decryptor, and WCry.
The ransomware is just like any other form of ransomware as it is designed to encrypt your files so that you are unable to open them and then demands a ransom payment for the decryption key. When encrypting a victim’s files, the ransomware will append .WCRY and .WNCRY to the end of encrypted files. As with most ransomware variants, WannaCry will also place a ransom note in the folders that contain encrypted files. We can see this ransom note below.
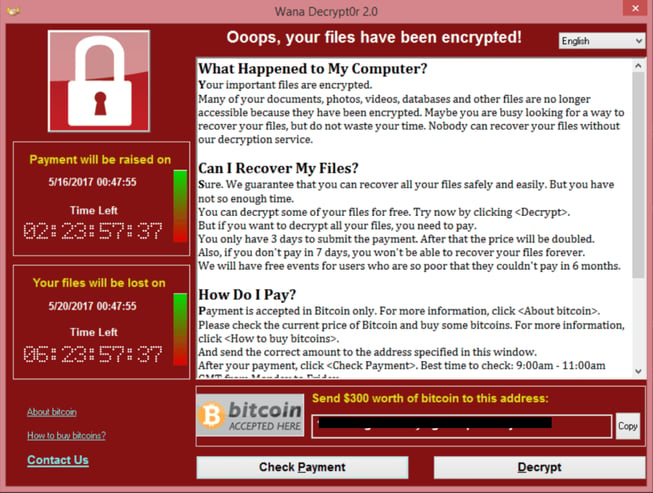
Why was WannaCry so Effective?
In an article we released titled: Top 7 Revelations of Vault 7, we discussed how the CIA and NSA lost control of its hacking arsenal including malware, viruses, trojans, and weaponized zero-day exploits. These weapons were released to an underground forum, and it was only a matter of time before a hacker figured out how to use them against the public.
That’s exactly what happened with the WannaCry attack. An unknown hacking group used an SMB exploit kit called ETERNALBLUE. ETERNALBLUE works by exploiting a vulnerability in the SMBv1 protocol to get a grip on vulnerable machines connected to the internet. In this attack, the vulnerable machines or victims were those who didn’t install the Microsoft patch MS17-010 which was released in March.
It was originally believed that ETERNALBLUE was the only exploit kit used, however, after further investigation on the attacks, researchers found that another exploit kit named DOUBLEPULSAR was used as well. DOUBLEPULSAR is also an NSA exploit kit that was released in the dump back in March. DOUBLEPULSAR is what’s called a malware loader, which uses a backdoor exploit to download and install other malware.
Using these exploit kits, WannaCry registered over 75,000 attacks in 99 countries in a matter of hours. It has been revealed that 3 out of 4 attacks occurred in Russia. The ransomware also had a major impact on the healthcare industry in the UK, causing at least 16 hospitals to shut down entire departments, turn away patients, and send staff members home.
What Have We Learned?
Since the outbreak of WannaCry, cybersecurity researchers have been trying to figure out who is responsible for these attacks. Almost a week later, signs are pointing towards North Korea. Security firms Kaspersky Lab, Symantec, and BAE Systems have put their full backing into the claims that they suspect a connection between North Korea’s Lazarus Group and the WannaCry ransomware. If that name sounds familiar, it’s because the Lazarus Group was linked to the Sony hack, the SWIFT bank attacks, and other hacks against financial institutions across the world.
According to the three companies, their claims are based on three areas:
- 2015 Contopee backdoor sample and February WannaCry sample use an identical random buffer generator function
- Contopee and WannaCry were written in C++ and compiled using Visual Studio 6.0
- The usage of leet speak inside the code
The Contopee backdoor sample was used by the Lazarus Group in many of their other hacks. However, it’s unclear whether these claims are legitimate as it’s somewhat common for other hacking groups to grab code from other malware samples when piecing together their own hacking tools.
What Does the Future Look Like?
As we’ve said before, it was only a matter of time before someone figured out how to use the NSA exploit kits against the public. Over 75,000 attacks and over 215,000 infected machines later, people are starting to believe it. It’s unclear how many weapons were released in the NSA dump. However, we can guarantee it’s more than the two that were used the WannaCry attack.
Inevitably, an attack similar to the magnitude of this is going to occur again – probably sooner than later. Hackers have now seen the damage that can be done in a very short amount of time. Whether it’s the same group of hackers or a different one, they are going to figure out how to use the other weapons to launch another massive attack.
You can protect your business and yourself from becoming a victim of the next big attack. WatchPoint has developed a tool to stop ransomware in its tracks; CryptoStopper. CryptoStopper uses deception technology in the form of Watcher Files placed on your network. The program continuously monitors the Watcher Files for the ransomware encryption process to start and will immediately identify the attack in seconds. CryptoStopper instantly isolates the infected machine from the network and shuts down the workstation. Upon isolating the attack, the program will send you an email notification informing you that a ransomware attack has been discovered and contained. On average, CryptoStopper isolates a ransomware attack in 9 seconds, preventing all of your targeted files from being encrypted and minimizing the damage done.
Contact WatchPoint today to learn how you can put your worries about ransomware attacks to rest. If you want further reading, check out our blog.


