2016 was an extremely busy year for cybercriminals. Between all of the data breaches that occurred, there were nearly 2 billion accounts compromised. In this article, we will review the ‘Top 5 Data Breaches’ throughout the last 12 months. Furthermore, we will discuss how all of these cyberattacks were preventable and how WatchPoint can protect your company from becoming the next big headline in cybersecurity news.

Top 5 Data Breaches
Hospitals Targeted in Ransomware Attacks
Several hospitals made headlines throughout the year as they became victims of ransomware attacks several times. In early February, Hollywood Presbyterian Medical Center became the first major hospital to become a victim in 2016. The attack caused the hospital to cease normal day-to-day operations, and the staff had to turn to manual documentation. Fax and telephone lines were jammed, and the use of computers was strictly prohibited. Hackers took the medical center’s system hostage and demanded 9,000 in Bitcoins or $3.6 million to decrypt the system and hospital’s files. In the end, the hospital ended up paying about $17,000 to recover their data but the time lost and the damage to their reputation goes way beyond the money.

A little over a month later, Methodist Hospital in Henderson, Kentucky issued an ‘internal state of emergency’ when they were infected by Locky ransomware. As soon as the IT staff at the hospital caught the attack, desktop computers and Web-based systems were shut down in an effort to stop the ransomware from spreading. The hackers responsible for this attack demanded four Bitcoins, or about $1,600. We believe Methodist Hospital was infected through a phishing campaign, as opposed to a targeted campaign since the ransom demanded was so low.
Kansas Heart Hospital in Wichita, Kansas was hit by a ransomware attack in late May. While the amount of ransom requested is unknown, the hospital paid the ransom only to be left high and dry as the hackers did not decrypt their files. Instead, they asked for a second ransom to be paid, which the hospital refused to do.
In early October, Marin Healthcare District became the third large healthcare provider to fall victim to a ransomware attack. Marin Medical Practices, the company that provides the Greenbrae, California-based district with business and healthcare system services, paid the ransom for an undisclosed amount. However, a failed backup system caused the company to lose clinical information collected in a two-week window at the district’s nine medical centers. The lost data includes vital signs, limited clinical history, documentation of physical exams, and communication records between patients and providers for over 5,000 individuals.
Social Media Data Breaches
LinkedIn, Myspace, and Tumblr all made headlines for massive data breaches in 2016.

In May, a Russian hacker who goes by the name of ‘Peace’ announced that he was selling 167 million email and passwords stolen from LinkedIn. The rate for the data was for five Bitcoins or about $2,300 at the time. The data breach is believed to have occurred in 2012, and it’s recommended that anyone who had an account at the time or has created one since reset their passwords immediately.
The Myspace account that you created in the early 2000s may have come back to haunt you in 2016. It appears that ‘Peace’ was extremely busy this year as he has claimed responsibility for stealing over 360 million user records of Myspace. Records include email addresses, Myspace usernames, and Myspace passwords for accounts created prior to June 11, 2013, when the data breach occurred. At the time, the Myspace breach was the largest data breach in history.
We’re going to do it. We are mentioning ‘Peace’ again as he claimed responsibility for the Tumblr data breach as well. On May 12th, Tumblr revealed that it had just discovered a 2013 data breach of user email addresses and passwords for over 65 million users. Tumblr currently hosts over 217 million separate blogs with 420 million users and was purchased in 2013 by Yahoo for $1.1 billion.
Distributed Denial of Service Attack – Mirai Botnet
Twitter, Reddit, Spotify, Etsy and an endless list of websites were down for an extended amount of time on Friday, October 21st due to a Distributed Denial of Service (DDoS) attack on Dyn. The cybercriminals who attacked Dyn used the Mirai botnet, a malware that scours the Web for Internet of Things (IoT) devices protected by little more than factory-default usernames and passwords. It then enlists the devices in attacks that hurl junk traffic at an online target until it can no longer accommodate legitimate visitors and users.
In this specific attack, Mirai compromised DVRs and IP cameras made by a Chinese hi-tech company called XiongMai Technologies. The components that XiongMai make are sold downstream to vendors who then use it in their own products. Basically, an entire company’s product line was turned into a botnet and attacked the United States. Below is a heat map of affected areas from the Dyn DDoS attack.
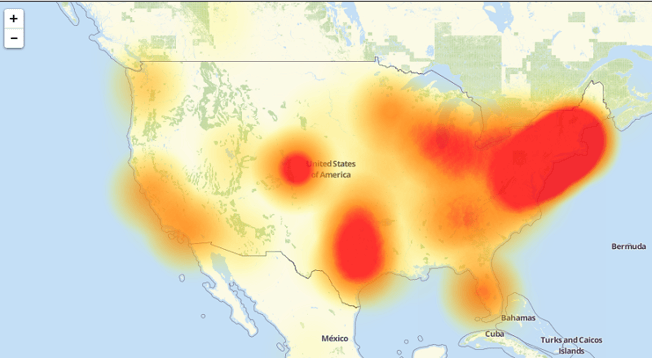
The power of IoT botnets and the damage that can be done are scary thoughts. While the only damage that came from the Dyn attack was several websites being down for a significant time, we believe this attack was just a test run for a future and potentially much more damaging attack.
Adult Friend Finder Breach
In 2015, nearly 37 million cheating men and women were exposed in a data breach on Ashley Madison. You would think from the lawsuits and fallout from that breach that these kind of sites would increase their cybersecurity measures. Well, on November 13th, it was revealed that hackers compromised the servers of Adult Friend Finder, Penthouse.com, and Stripshow.com. In the breach, the Adult Friend Finder server was hit the hardest with over 339 million accounts stolen. Add in Penthouse.com and Stripshow.com and the breach exposed over 412 million accounts. The scale of this data breach is second only to the Yahoo breach.
The individuals affected by the data breach are mainly the users who have signed up for the websites. The data stolen included names, email addresses, as well as login credentials. While, as with most data breaches, we worry most about the login credentials being stolen, this breach is different. It’s expected that the names and email addresses of the individuals on the websites will be sold on the dark web and released for the public to see. This could be extremely damaging to some personal relationships, and unfortunately, there’s nothing anyone can do about the information once it’s released
Yahoo Data Breach
In September, Yahoo announced that the personal data of 500 million accounts was stolen in 2013. At the time, this data breach was the largest to-date. However, on December 15th, Yahoo announced that it suffered an even larger data breach. Officials from Yahoo said that more than 1 BILLION accounts were compromised in August of 2013. Now, Yahoo is responsible for the two largest data breaches ever to occur. The stolen user account information included names, email addresses, telephone numbers, dates of birth, passwords, and even encrypted or decrypted security questions and answers.

Chances are if you have a Yahoo account, your personally identifiable information was stolen and could potentially be used to gather other data about you, such as your banking information. To see whether you have been affected by the Yahoo hack, read our article here.
Don’t Become the Next Headline
2016 was also an extremely busy year here at WatchPoint. Throughout all of the cyberattacks that occurred over the last two years, we have noticed one thing: they are all PREVENTABLE. All of these attacks were preventable through patching, user education, a competent security team, and endpoint detection and response. WatchPoint has the tools to ensure your company doesn’t become the next big headline in cybersecurity news.
In May, we released a malware intrusion technology called CryptoStopper. After seeing cyberattacks such as ransomware cripple businesses across the country, WatchPoint’s innovation team created a solution that could detect and stop ransomware. Using deception technology in the form of watcher files placed in your important network shares, CryptoStopper continuously monitors these files for signs of encryption. The program will immediately isolate and shutdown the workstation to prevent the ransomware from spreading. Lastly, CrypoStopper will send you an email notification informing you of the ransomware attack and that it has been successfully contained.
Cybersecurity should no longer be an afterthought for your business; let WatchPoint help you make it a priority.


