December was an extremely busy month for cybercriminals as several new versions of ransomware were released. The holiday season increases Internet traffic to 50% of the world’s population using the World Wide Web. It’s no surprise that cybercriminals looked to cash-in during this time with the massive influx of potential victims. For this month, we’ll discuss how cybercriminals took advantage of holiday shoppers with several noteworthy ransomware versions. There were also a couple of Cerber ransomware updates, and Android devices made the headlines more times than their manufacturers would have liked. Lastly, decryption keys that were released this month will also be included.
New Ransomware Variations
Locky Ransomware Changes Extension
The developers of Locky ransomware have changed the extension left on encrypted files. Encrypted files are now appended with .osiris, based off Egyptian mythology. As you can see from the email below, this version of Locky is being distributed via fake Excel invoices.
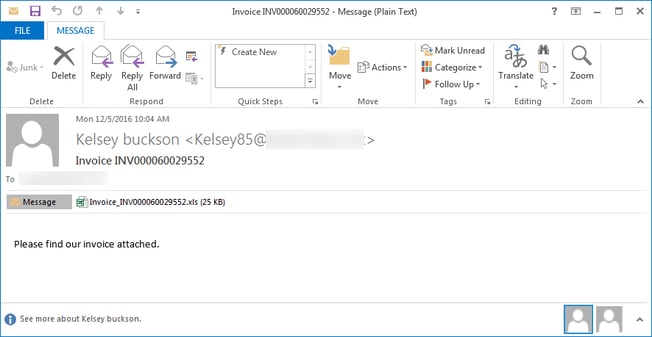
When the user opens the Excel file, they will be prompted to enable macros. Once the macros are enabled, a legitimate Windows program called Rundll32.exe will run, and Locky will be installed on the computer. Once Locky has been installed, the malware will scan the computer for certain files, encrypt them, and a typical ransom note will appear. Unfortunately, there is still no way to decrypt files infected by Locky without paying the ransom.
Koolova Ransomware
In the middle of December, ‘Popcorn Time’ added a strange twist to ransomware by giving victims the option of paying the ransom or spreading the ransomware to two other users to gain access to the decryption key.
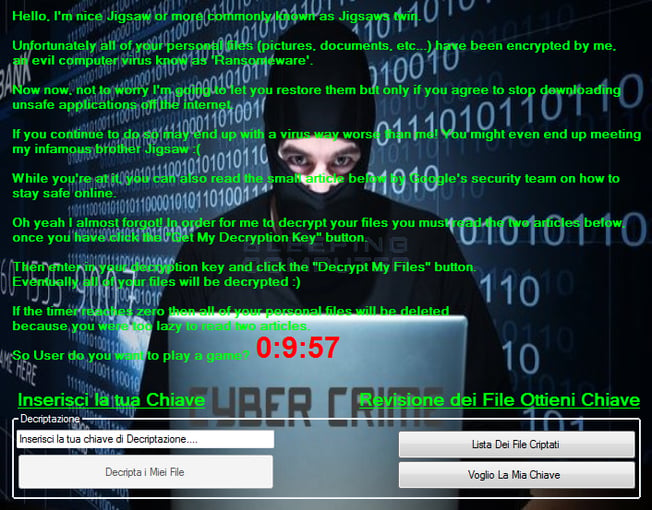
Koolova adds to the weird versions of ransomware coming out by giving victims the decryption key for free if you read two articles on ransomware. As the ransom note below shows, if the victim is too lazy to read the articles before the countdown gets to zero, Koolova will delete your encrypted files. The articles that Koolova wants you to read are a Google Security Blog called ‘Stay Safe While Browsing’ and Bleeping Computer’s ‘Jigsaw Ransomware Decrypted: Will delete your files until you pay the ransom.’ Once both the articles are read, the Decrypt My Files button becomes available.
Ransomware Released by 13-Year-Old
Free-Freedom is a new ransomware supposedly created and released by a 13-year-old boy. Rather than encrypting your files, it just messes up file permissions. While this version of ransomware already has an unlock code, it demonstrates what we have been telling you; ransomware can be distributed by cybercriminals of all technical abilities.
Cerber Ransomware Updates
Cerber has been one of the most active ransomware over the last year and December proved to be no different. Below are all the updates to Cerber throughout the month of December.
Cerber doesn’t delete shadow volume copies anymore and now prioritizes certain Microsoft Office documents. Shadow copy is a technology included in Microsoft Windows that allows taking manual or automatic backup copies or snapshots of computer files or volumes, even when they are in use. This opens the door for recovering at least a small number of files using special disk recovery software. Instead, Cerber prioritizes certain folders including Excel, Office, OneNote, Outlook, PowerPoint, and Word files.
The group behind Cerber launched a spamming campaign targeted at holiday shoppers. Using fake credit card reports, the cybercriminals trick users into opening a Word file that will download and install Cerber. The campaign was aimed at victims becoming worried about being billed for purchases they didn’t make. Read our full article about this campaign here.
Lastly, the Cerber gang decided to get into the Christmas spirit by using domains with christmaas in them. Two of the three domains have been suspended while the third is still active. While this doesn’t have much of an effect on users, the Cerber group was extremely busy during the holidays.
Android Devices Make Headlines Twice in December
Cybercriminals were busy infecting Android devices in the month of December. First, FakeToken and Tordow 2.0 banking Trojans are now equipped with ransomware. FakeToken generates fake login screens for more than 2,000 financial applications to steal users’ login credentials. It is now equipped with ransomware which encrypts files stored on the phone’s SD card. Once the relevant command is received, the Trojan compiles a list of files located on the device and encrypts them.
Tordow 2.0 can make phone calls, control text messages, download and install programs, steal login credentials, access contacts, visit web pages, manipulate banking data, remove security software, reboot devices, rename files, encrypt files, and act as ransomware. Tordow 2.0 infected 16,000 devices in 27 countries.
Second, Cyber Police ransomware has turned to infecting LG Smart TVs which are powered by Android. Cyber Police came onto the cybersecurity scene back in April and infected millions of Android devices with ransomware. Cyber Police infects LG Smart TVs through third-party applications that are downloaded onto the TVs. Upon infecting the TV, Cyber Police displays a ransom note demanding $500 in payment. While these infections are largely on older, outdated LG TVs, researchers conducted a test and installed ransomware on newer versions and found it extremely difficult to remove the malware from the infected TV; even saying it would be nearly impossible for regular users to do so. LG support currently sends you a bill for about $340 for them to remotely reset your Smart TV. Our advice, if your older TV is infected with the ransomware, is to purchase an upgraded version and only download applications in the Google Play store.
The good news about ransomware infecting Android devices is that you don’t have to pay the ransom if you know what to do. With the Android phones, you simply need to reset your device, connect it to your computer, and download the files from the cloud where you stored your data. Meaning, you should regularly backup the data on your phone in the cloud. I’m not sure about Android devices, but my iPhone lets me know every day that I haven’t backed up my phone for a week. As annoying as it may be, it will come in handy if cybercriminals figure out how to infect Apple devices.
Decryption Keys
Nemucod Decryption Tool Released
Emsisoft released a decryption tool for Nemucod. Nemucod is a JavaScript downloader malware used by TeslaCrypt for distributing their various versions of ransomware. To use the decryption tool, you will be required to provide an encrypted file of at least 4096 bytes in size as well as its unencrypted version. To learn how to use the decryption tool, click here.
Locked-In Ransomware Free Decryption
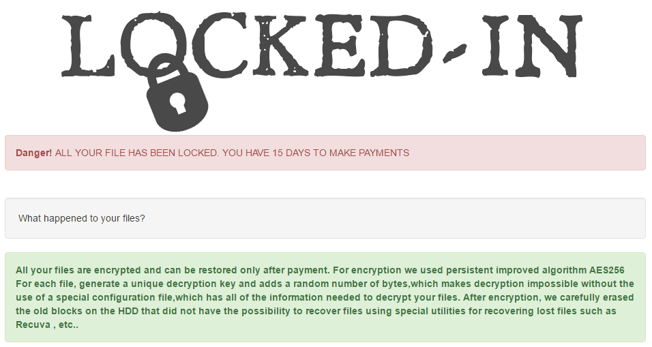
Locked-In ransomware was first spotted in early December. The Locked-In ransomware encrypts victim’s files with AES and appends a random extension to each file. The ransom note left behind is titled ‘RESTORE_CORUPTED_FILES.HTML’ or ‘RESTORE_NOVALID_FILES.HTML’ and looks like the image below.
Just over a week later, a free decryption tool was released. To gain access to the decryption tool if you have been infected with Locked-in ransomware, click here.
GlobeImposter Decryption Tool
GlobeImposter is a ransomware that imitates ransom notes and file extensions found in Globe ransomware. Files that have been encrypted are appended with ‘.crypt’ and a ransom note named ‘HOW_OPEN_FILES.hta’ can be found in all folders with encrypted documents. Like the Nemucod decryption tool, you will need an encrypted and unencrypted version of the file for the decryption tool to work. Click here to download the decryption tool.
Outlook
We recently released an article on 2017 Cybersecurity Predictions. December was a crazy month for ransomware and we fully expect 2017 to be the same or even worse. Don't be the company who wishes they would have done something to prevent ransomware from infiltrating their network. WatchPoint has the tools available to ensure your cybersecurity well-being.
CryptoStopper, developed by WatchPoint, uses deception technology in the form of watcher files placed in your important network shares. CryptoStopper continuously monitors the watcher files for the encrpytion process to start and will identify the ransomware attack in seconds. CryptoStopper will immediately isolate the infected workstation from the network and then shut down the workstation. Lastly, it will send you an email notification letting you know a ransomware attack has been discovered and contained.

