Advanced Persistent Threats (APT) and ransomware have been the most dreaded types of malware over the last couple of years. While there are clear and distinct differences between APTs and ransomware, we are now seeing the two being paired together to create a type of hybrid malware.
Advanced Persistent Threats vs. Ransomware
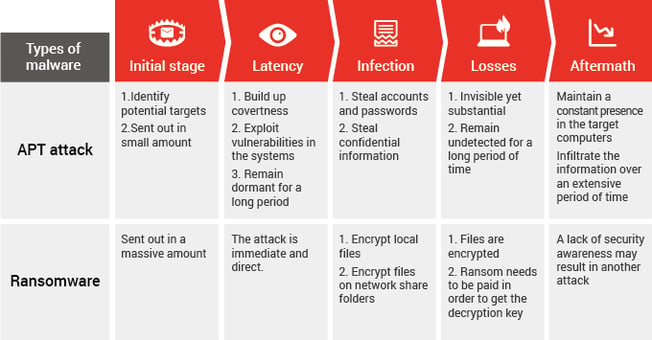
Advanced Persistent Threats are aimed at specific targets and are carried out over a long period of time. When an APT infiltrates a computer, it remains there undetected for a significant amount of time. By gaining access to the host computer (the target) and eventually full control over the computer, the APT waits for the right opportunity to launch its attack. When the opportunity arises, an APT steals valuable data from the host computer. A typical APT attack is aimed at stealing user accounts, passwords, and other personally identifiable information. When comparing an APT and a ransomware attack, an APT attack usually results in more substantial and unexpected damage. Affected organizations are often shocked by how long an APT attack lasts, which can sometimes be several years. Also, if a comprehensive security check of the network isn’t conducted after an APT is discovered, there a huge possibility that the APT will remain on the computer which could cause even more damage.
As far as ransomware is concerned, we all know what it does – blocks access to your computer system until a sum of money is paid. It’s important to note, however, the differences between APTs and ransomware. Whereas traditional APTs target specific users, ransomware is sent out en mass through a multitude of distribution methods. Unlike APT, ransomware wants the victim to know they have been infected and wants them to know as soon as possible - hence the ransom note that appears once the encryption process has finished. Additionally, ransomware typically doesn’t steal your data rather, it encrypts important files and doesn’t provide the decryption key until the ransom has been paid. The image below can help us further understand the differences between APTs and ransomware.
Advanced Persistent Threats Plus Ransomware
We recently released an article on DynA-Crypt, which is a first-of-its-kind malware that combines APTs with ransomware. DynA-Crypt is getting a ton of attention because it not only encrypts your files but steals your data as well. When the encryption process has finished, DynA-Crypt leaves files and processes running (the APT) on the computer. Basically, the malware leaves bits of code on the infected machine so the hacker can come back later and do more damage or, they can sit in your devices and collect more intel. Some APTs also run on a schedule meaning, if you have been infected with DynA-Crypt or another APT and you are using forensic tools to detect them, the APT may not be running and thus, may not be detected. The APT can then turn itself back on and become active again without you knowing.
DynA-Crypt is the first ransomware to pair with APTs. However, it’s certainly not going to be the last. Combining two of the most dreaded types of malware into one presents quite the headache for victims but also presents a dynamic cyberattack for hackers. With the sophistication of cyberattacks increasing, we must become even more diligent with our cyber security.

