Although February was a short month, there certainly wasn’t a shortage of new ransomware variants. While there were several variants that will probably never make it into circulation, there was some notable ransomwares that we should all be aware of. We will review the most notable ransomware variants throughout the month as well as provide an update on new versions that infect Android devices. Unfortunately, there weren’t any decryption keys that were released over the last 28 days.
Notable Ransomware Variants
CryptoShield 1.0
CryptoShield 1.0 (CryptoShield), a variant of the CryptoMax family, was found being distributed via EITest and the RIG exploit kit. EITest is a JavaScript attack code that is injected into sites so that it will be executed by visitors. CryptoShield is being distributed through sites that have been compromised so that when a user goes to the site, they will encounter the EITest attack chain. Once the EITest has been downloaded, the program will load the RIG exploit kit that will install the CryptoShield malware.
Exploit kits like RIG use vulnerabilities in installed programs to infect a computer, so it is extremely important to ensure that all of your programs have the most current updates installed. This is especially important for programs such as Adobe, Java, and Windows as these programs interact with online documents or sites.
While CryptoShield sounds like every other variant of ransomware, its danger comes from the number of files the malware targets. CryptoShield targets over 350 files during the encryption process and will append .CRYPTOSHIELD to an encrypted file. In each folder where encrypted files are located, a ransom note named #RESTORING FILES will appear. The ransom note, as seen below, provides information on what happened to your files, a personal identification, and three email addresses that can be used to contact the ransomware developer for payment instructions.
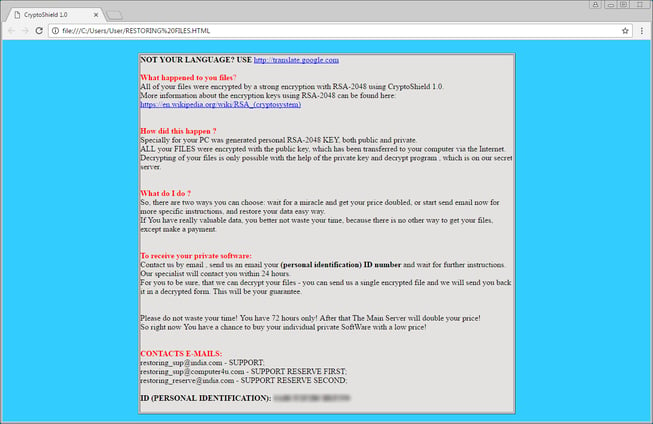
Unfortunately, there is currently no way to decrypt your files without paying the ransom.
Serpent Ransomware
Serpent ransomware is a notable variant as it appears to be a member of the Wildfire family which was taken down by the National High Tech Crime Unit of the Dutch Police. Like other very successful ransomware variants, Serpent is distributed via SPAM emails masquerading as outstanding invoices. While the email is in Danish, the ransomware is still intended to infect users from countries except for Armenia, Azerbaijan, Belarus, Georgia, Kyrgyzstan, Kazakhstan, Moldova, Russia, Turkmenistan, or Tajikistan. It’s unclear why these countries are left out of the target market, however, if the user’s IP address is from one of the countries above, the ransomware will shut itself down and not encrypt your computer. When the ransomware determines that the user has a suitable IP address, Serpent will begin its encryption process, appending a .serpent extension to the end of encrypted files.
A typical ransom note will appear once the encryption process has finished. Within the ransom note, a link to instructions on how to pay the ransom is provided. The going rate for recovering your files from Serpent is .75 bitcoins ($730) however if the ransom isn’t paid within seven days, the rate goes up to 2.25 bitcoins ($2,200). Serpent’s website also includes what we are seeing more and more with ransomware, sophistication. The majority of previous ransomware variants provided little support to victims. Serpent provides tabs for instructions on how to pay, a FAQ section, and support where you can send a message to the distributors.
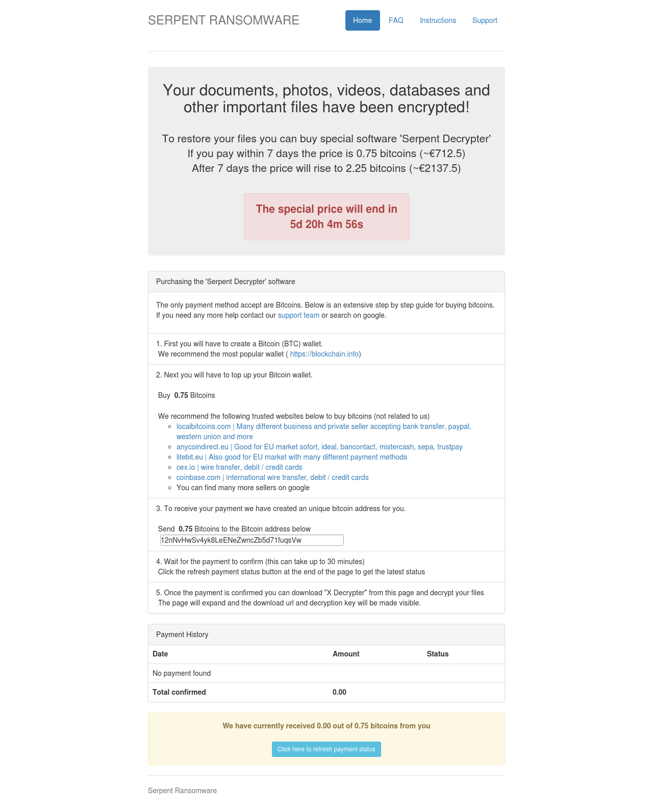
At this time, there is no way to decrypt your files without paying the ransom.
DynA-Crypt
We covered DynA-Crypt in an article in the middle of February. It’s the only ransomware from this month that has characteristics that we have never seen before. DynA-Crypt not only encrypts your files but also steals information from the infected computer. The ransomware is composed of numerous standalone executables and PowerShell scripts that encrypt your files while stealing passwords and contacts. Once the data has been stolen, it will be delivered to the cybercriminal for him or her to do as they please. If that wasn’t enough, the ransomware deletes files without backing them up anywhere, for no apparent reason.
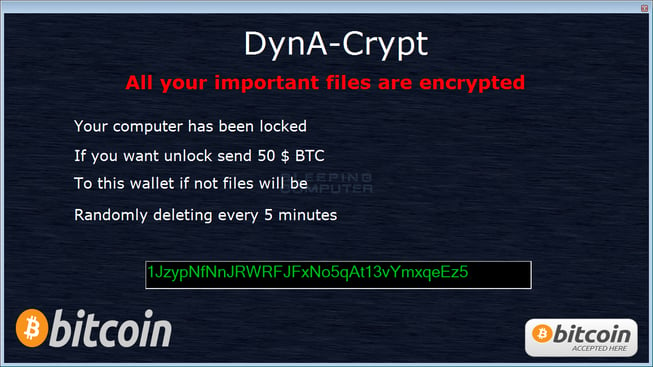
Android Updates
Android Banking Trojan
An Android banking trojan that was leaked online in December of 2016 is now being seen in attacks on a regular basis. Meaning, the source code for this banking trojan is available to anyone who wants to use it. In February, there were three active campaigns. The first campaign only targeted customers of several Russian banks. The second and third campaigns infected two applications within the Google Play store. The latter two campaigns are worrisome as most malware that infects Android devices are from applications downloaded from third-party vendors. The campaigns, that infected two legitimate Android weather applications, embedded the banking trojan in its source code, repackaged the application, and successfully uploaded the application in the Play store. So that you are aware, the applications that have been compromised are Good Weather and Weather.
In total, the banking trojans targeted nearly 100 mobile banking applications from the US, UK, Austria, Germany, and Turkey. Banking trojans allow cybercriminals to gain login credentials, lock the user’s device via a ransomware-like behavior, and intercept text messages for the ability to bypass two-factor authentication.
Lockdroid Android Ransomware
Lockdroid is one of the oldest families of ransomware on the Android market. Past versions had the classic route of displaying an email address in the ransom note which they should contact in order to pay the ransom to unlock their phone. The latest version, which appeared in late February, is experimenting with the 2D barcode system as well as a text-to-speech function.
First, a 2D barcode appears on the Android when the device has been infected with ransomware. The victim must scan the barcode in order to receive a URL where they can pay the ransom. As a single device user (I only have a cell phone), this part doesn’t really make sense as it’s assuming everyone infected has a tablet of some sort. It appears that this was only an experiment as the text-to-speech function quickly replaced the 2D barcode system. After Lockdroid infects an Android device, users receive a message with an ID that is used to contact the ransomware distributer. What follows is a text-to-speech conversation between the victim and the distributor where they negotiate the ransom amount. Once the ransom is paid, the victim receives a four-string unlock code to regain access to their device.
With most Android malware, the best way to avoid being infected by a banking trojan or ransomware is to avoid installing applications outside the official Google Play Store. Also, avoid giving mobile applications more permissions than they need to do their job. Unfortunately, hackers are now finding ways to infiltrate the Google Play Store where there’s virtually nothing you can do about being infected if you have the application downloaded on your phone. If you do end up becoming a victim of a banking trojan, you need to change all of your login credentials for your bank, and we recommend changing all other credentials as those may be compromised as well. As for Android ransomware, you don’t have to pay it! Make sure you regularly back up your devices so you can simply perform a factory reset and download the latest backup from the cloud or from your computer.


