A little over a decade ago, most computer viruses were simpler than the ones we see today. Back then viruses were like a 3 function Swiss army knife; they might change the background, rename files, and take over a browser. But fast forward to today and the modern malware has grown to a 12 function Swiss army knife, capable of performing just about any malicious task.
There is no shortcut to testing your defenses against a ransomware attack. WatchPoint has created a PowerShell script to allow you to simulate an attack. Click HERE for details.
In response to today’s multi-vector malware, it’s no wonder that dozens of solutions have been adapted to combat them. In today’s article we’re going to narrow the discussion to ransomware and explore its core components.
Blockchains
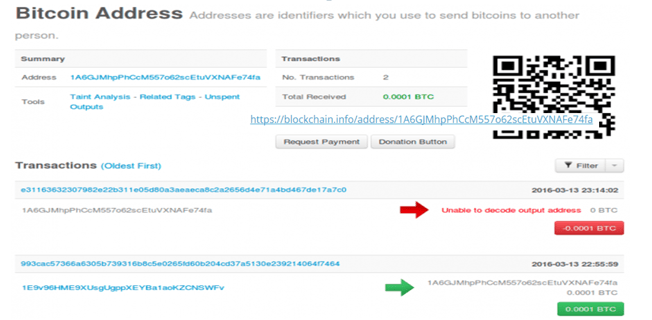
Blockchains are a fairly new development, and it’s actually quite clever. We anticipate that blockchains will replace the TOR websites that are most commonly used to collect payment. So what is a blockchain? Well, a blockchain is simply a URL that identifies a bitcoin wallet, such as
![]()
Blockchains are becoming the preferred method because it allows the cyber criminals to still collect their payment, without needing to run a dedicated website. If their website was taken down then the perpetrators would have no way to collect their ransom. And because blockchains are publicly available and integral to bitcoin, they won’t be taken down. So the bad guys have found a clever way to utilize an integral part of bitcoins to their advantage.
It works because blockchains contain metadata and programmers will use that metadata to store the decryption key. A successful blockchain payment triggers a response on the bad guy’s end, which then embeds the decryption key into the metadata, and is then sent to the victim. Thus it allows the attacker to collect payment while also staying anonymous.
File Extensions/File Name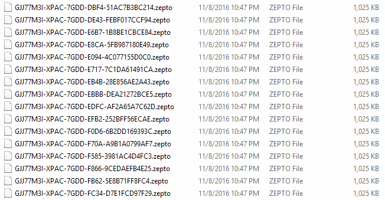
Pretty much all ransomware will change the file extension for every file that it encrypts. And certain variants, like Zepto, will also rename the file to some random file name, as seen in the graphic to the right. The odd thing about this behavior, is that you’re tipping your hand. If ransomware is a game of poker, you’ve just alerted the other players to your ace. If it were me, I would leave my victim guessing a little more about what files were encrypted and what files were not. But I suppose that if you’re confident enough in your hand, you don’t mind showing it.
In response to this behavior of using certain file extensions, companies have started arming themselves with adapted solutions like Microsoft FSRM, which can disconnect a share when certain file extensions are found on the network. This solution certainly isn’t elegant as it disconnects an entire share and thus interrupts everyone who was using it, but it could work.
Unfortunately, the malware developers have caught on to this trend and have modified their code. Variants like CryptMic use a random file extension on every file, thus making it impossible to defend yourself with something like FSRM because you can no longer anticipate what the file extension will be.
DNS
DNS is the backbone of the Internet, but here again we see ransomware tipping its hand when it comes to DNS. To understand this we first need to understand that ransomware developers need to get paid and they need to do so anonymously. Enter the TOR network. TOR is like DNS except that it provides anonymity to its users. Like we saw in our blockchain example, a blockchain website is where TOR meets the regular Internet. It allows ransomware developers to maintain privacy while also allowing their victims to make a payment via the regular Internet.
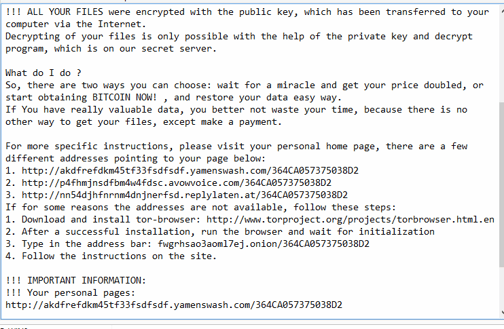
In response to this behavior, DNS filtering and DNS reputation services are being used as adapted solutions to combat ransomware. Connecting to a TOR network or a blockchain website can trigger an alert or block the connection entirely.
While DNS solutions can alert you to the presence of ransomware, it can’t do anything to stop the encryption process. This makes using DNS services as one of the least effective solutions for combating malware. It lacks a response component to actually stop the attack after it’s started.
Evasion Techniques
Malware doesn’t want to be detected. The longer they can stay on a system, the more harm they can cause. This is evident by the behavior of ransomware once it’s entered a system. This first item that we’ll explore is file deletion. TeslaCrypt, for example, deletes the original file. That’s right - it delete’s itself. Here is how that works:
- Ransomware executes.
- A process is started, so now ransomware is running in memory.
- The original file is either deleted or deleted while other files are created in its place. These other files will typically be placed in system directories in order to disguise their presence and delay or avoid detection.
The next item we’ll explore is process evasion. A computer is more than just the files on the hard-drive; it also has memory. And as long as ransomware can run in memory, it doesn’t need the original file. The idea here is that by deleting itself, it cannot be found by antivirus scans. In the graphic below we show a before and after example of the TeslaCrypt ransomware. In the before picture, we see a process called teslacrypt.exe. Then about 20 seconds into the infection, the process teslacrypt.exe process is renamed to a random process name. In this example the new process is called jprpcaher.exe. Notice how ‘Picnics Pounces Reserves’ is identical between each process.
![]()
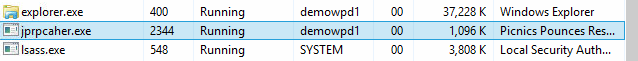
Ransomware renames the process in order to evade detection or at least slow the detection. By using a random process name it makes it more difficult to correlate the original (deleted file) with the malicious process that is running in its place.
Encryption
At the heart of all ransomware is encryption. This is where adapted solutions and even self-declared anti-ransomware solutions are lacking. They don’t address the core function of ransomware. And for every detection technique and adapted solution that is available, ransomware has a work-around for it. The only thing that ransomware can never avoid is encryption, because that’s exactly what it does.
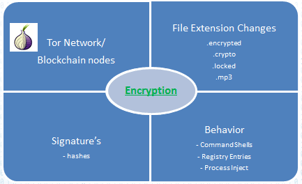 Summary
Summary
Ransomware has many components to it, but adapted solutions like FSRM, DNS filtering, Anti-Virus, and SEIMs don’t tackle ransomware head on. They are security products, but they aren’t dedicated to ransomware.
And when your defenses aren’t addressing what’s core to a problem, then it simply isn’t a reliable solution. CryptoStopper addresses ransomware head on because it identifies the encryption process.
Unavoidable
CryptoStopper works because it gives ransomware exactly what it wants, which is files to encrypt. By seeding the network with bait files, CryptoStopper becomes unavoidable. There is nowhere the ransomware can go that CryptoStopper can’t detect it.
Fast
CryptoStopper is also fast. Within seconds of the attack, CryptoStopper identifies and blocks the infected computer, thus containing the threat. Because CryptoStopper can isolate the infected host, everyone else in the company can continue working, and your customers can continue using your products and services.
Download a free trial of CryptoStopper and protect your network from ransomware once and for all!


