I’d like to discuss a situation that arose this week with a former backup customer and how that customer came to realize they need WatchPoint. For privacy concerns, I will address the business as…
How Many of Your Employees Will Get Phished Today?
Phishing is an attempt by cybercriminals to steal your money and data using malicious email messages, websites and sometimes even phone calls. These criminals gain access to your information by…
New Banking Trojans Emerge with the Death of the Dyre Virus
In the past several months the infamous Dyre Banking Trojan has gone silent with security researchers reporting actual new infections dropping to single digits. Researchers suspect that a raid on a…
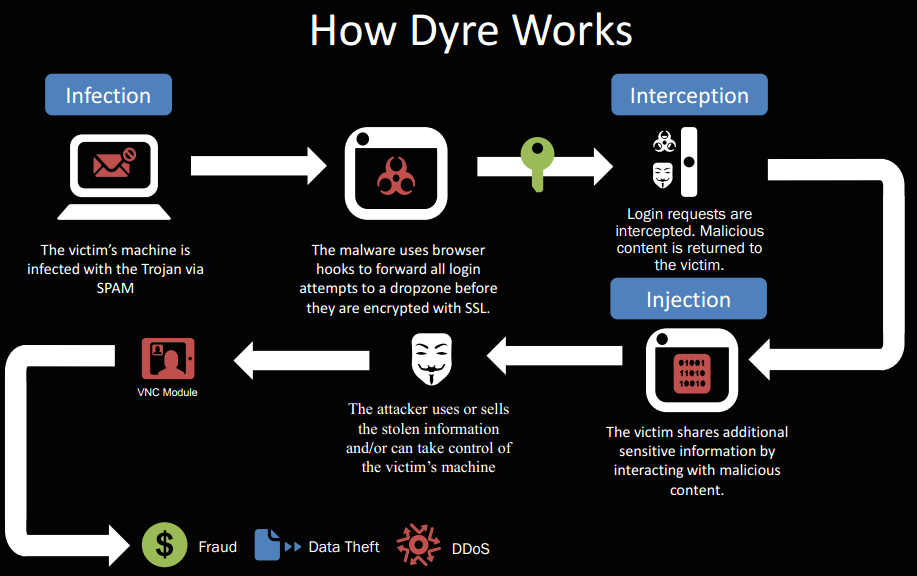
A Simple Introduction to the Dyre (Dyreza) Banking Trojan
The latest variant of the Dyre virus was discovered by Trend Micro in early 2015. Dyre is financial malware that targets banks and uses propagation and evasion techniques to reproduce itself and…
Why I’m breaking up with my Antivirus Software
Many years ago when setting up a new workstation the most important task in the entire process even before checking for updates, applying patches and updating device drivers was installing a…
How to Safely Download Software
There is a wide range of software available to download from the internet. A lot of that software is free and available on a number of different websites. It can be difficult to determine what…
Why you should worry about Application Security
Application Layer Security A lot of time and energy has been expended discussing network security. Organizations have spent millions putting network security mechanisms in place to protect their…
Will US Technology Companies Hand Over Encryption Keys To The U.S. Government?
FBI Director James Comey is holding back no punches in his quest to persuade American technology companies to hand over the encryption keys to their software that helps keep your data secure. Keeping…
Why Closing Unused Server Ports is Critical to Cyber Security
Why Closing Unused Ports on a Server is Critical to Cyber Security. Open ports on a server are a security vulnerability that can potentially allow a hacker to exploit services on your network. If…