Today we are going to look at how CryptoStopper.io performs against a malware attack by the dreaded TeslaCrypt ransomware. In this demonstration, I will illustrate how quickly a server running CryptoStopper.io can isolate and shut down a workstation after the workstation has been infected with TeslaCrypt ransomware.
From the workstation, I downloaded a copy of the TeslaCrypt variant from virusshare.com. I also installed the server version of CryptoStopper.io onto my Windows Server 2012 R2 box and pointed CryptoStopper.io to monitor the share.
Screenshot 1
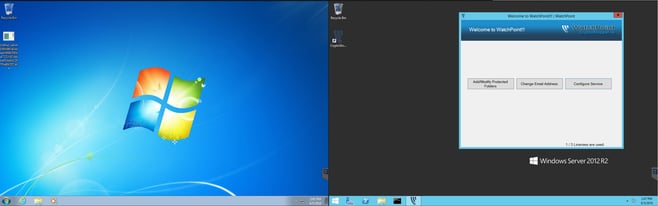
This screenshot shows the test environment. The workstation on the left is running Windows 7 Professional and has the ransomware Trojan copied on the desktop. You can see the executable under the Recycle Bin with the long file name. The system to the right is the Windows 2012 R2 server that has CryptoStopper.io installed on it.
Screenshot 2
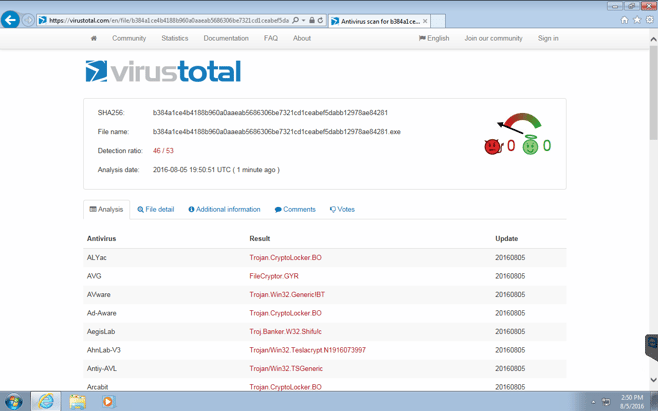
I used virustotal.com to validate that the ransomware variant is a legitimate threat and recognized by a large number of antivirus vendors.
Screenshot 3
This shot shows the running processes on the workstation prior to launching the infection. It also shows that I have a network drive mapped from the server. Once the ransomware attack is initiated from the workstation I expect it to attempt to enumerate the network share and attack the files contained within.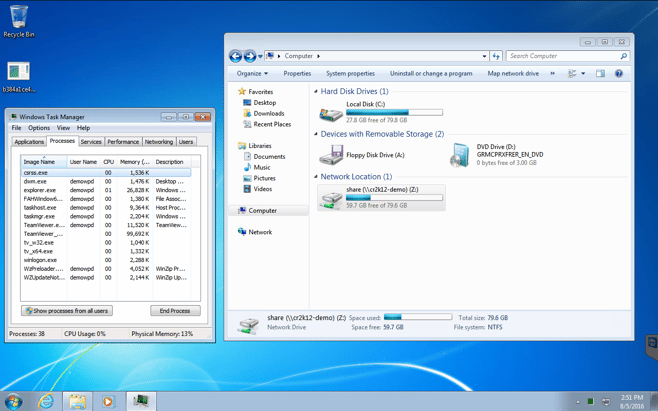
Screenshot 4
In screenshot 4 you can see the share folder on the server and some of the data populated.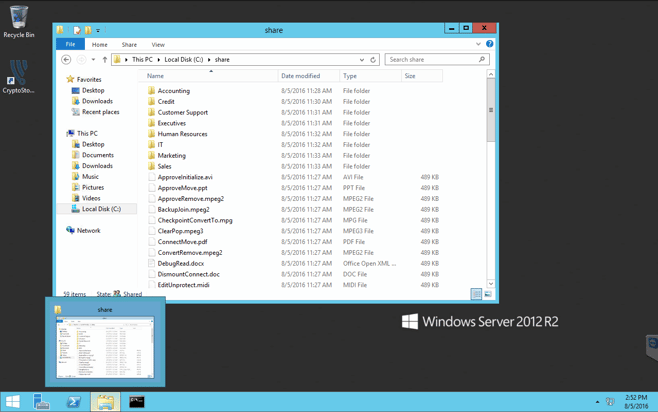
Screenshot 5
Cryptostopper.io will use Windows Firewall to isolate an infected workstation. If you look at the “Scope” tab under the CryptoStopper Properties window, you will see there are currently no remote IP addressed being blocked by the firewall.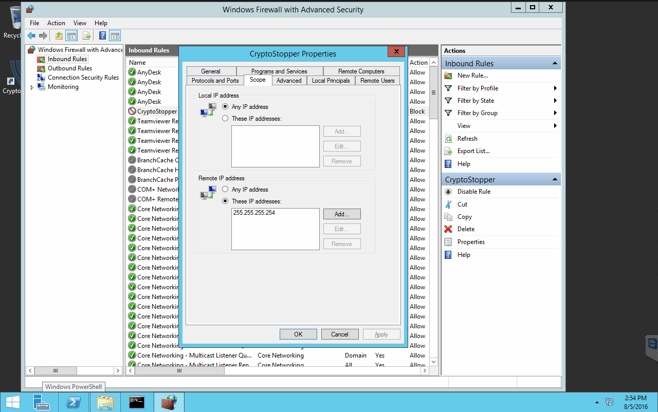
Screenshot 6
Now that the workstation and the server environment are setup and ready for testing, I will initiate the ransomware attack. I just double-clicked the Trojan executable on the desktop, and I’m being prompted to run the software.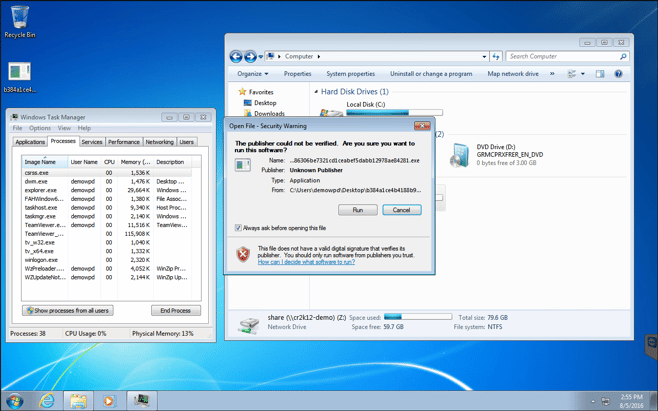
Screenshot 7
After I pressed the run button and gave the workstation permission to launch the ransomware you can see a process launch that matches the name of the ransomware. It is the top process that has the same name as the ransomware executable.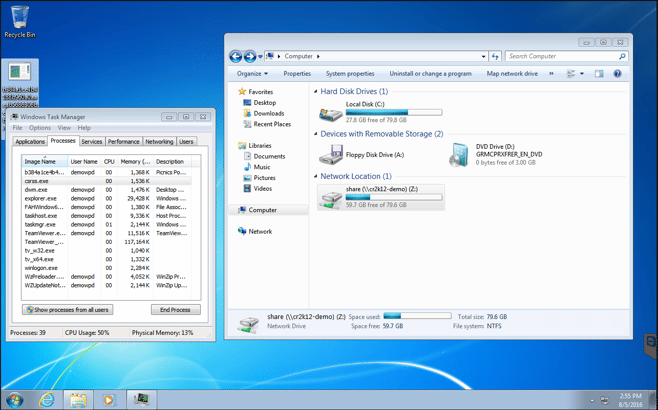
Screenshot 8
Now things start to get interesting. If you look closely at the running processes, you can see the Trojan spawned a child process called cmd.exe *32. The Trojan is using the command line to start doing its work.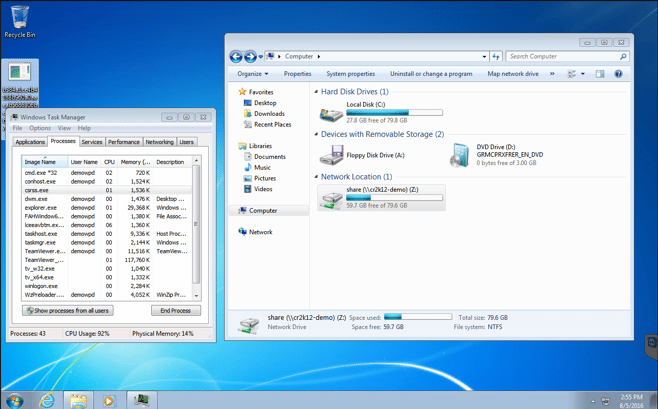
Screenshot 9
Things are heating up. It looks like another child process called Iceeavbtm.exe has kicked off. Right away I notice that the description of the process is suspicious - “Picnics Pounces Reserves.” These sound like randomly generated words. If you look closely, you will also notice that the ransomware deleted itself from the desktop of the Windows 7 workstation in an attempt to conceal its existence.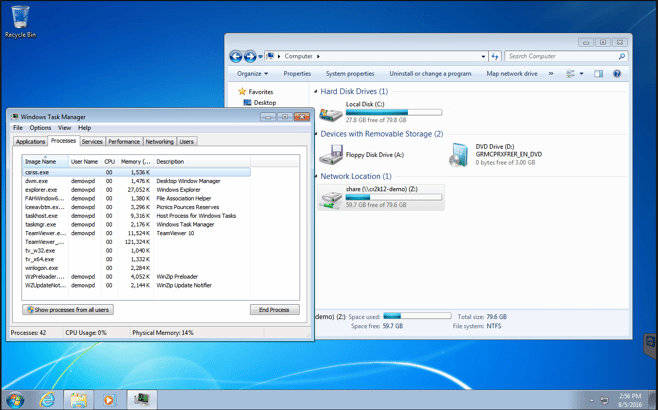
Screenshot 10
I was able to quickly right-click the suspicious process and open the file location. There are two files that catch my eye. The first one is the Iceeavbtm.exe application that is running the suspicious process. I also notice another file that has been dropped into the Documents folder named yqwld.exe.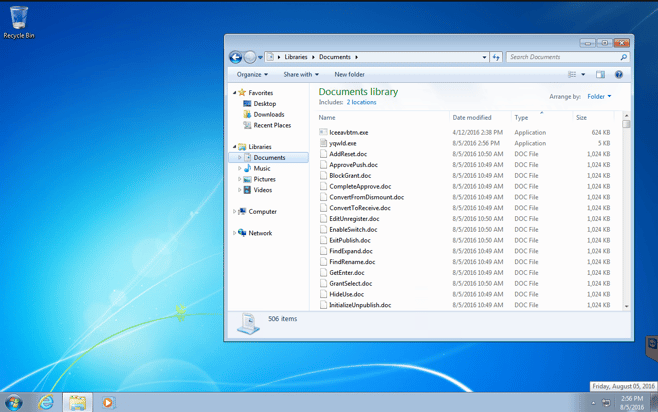
Screenshot 11
In less than 2 minutes of running the Trojan executable, the ransomware demand notices start to appear. You can see under Network Location that three new files have appeared. All are named “recovery+pmiev” and have a file extension of .txt, .png, or .html. It looks like something is trying to get our attention.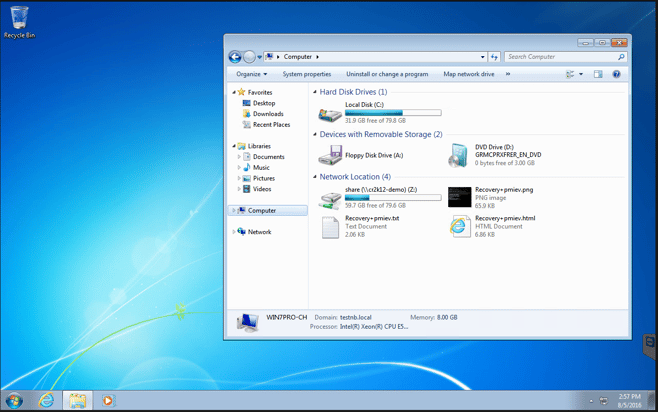
Screenshot 12
Screenshot 12 shows that within just a few minutes the ransomware was able to enumerate my network share and attempt to encrypt the data on the share. At this point CryptoStopper.io has recognized the behavior and acted to isolate the workstation by sending a command to shut down and display the message that a ransomware attack has been detected from the workstation.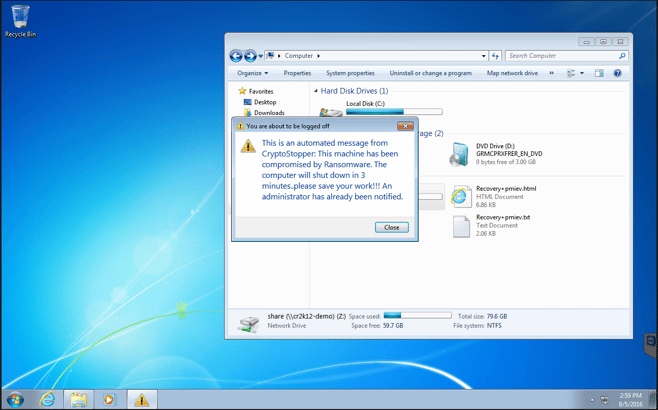
Screenshot 13
After getting the notification of the workstation shutdown, you can see the isolation of the workstation by reviewing the firewall on the server. As you can see, my workstation IP address of 192.168.15.105 is listed under Remote IP address.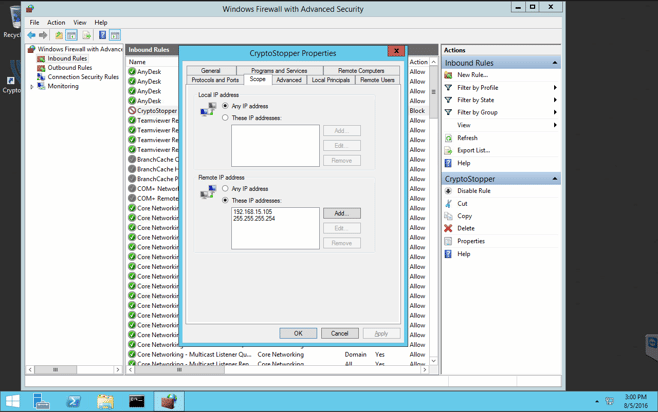
Screenshot 14
A second message popped up on the Windows 7 workstation, notifying the user that the workstation will be shutdown in 2 minutes.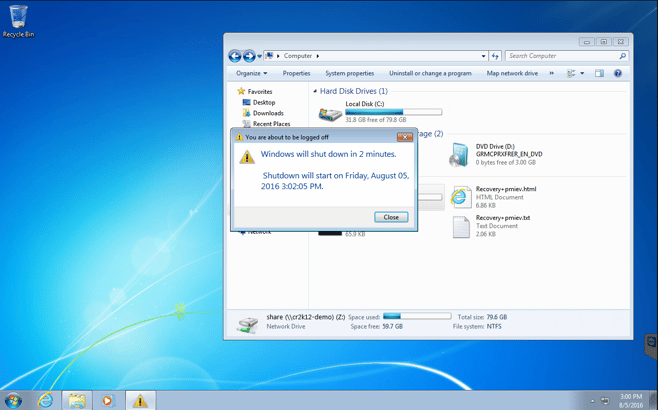
Screenshot 15
I verified the isolation of the workstation by attempting to access my server share. You’ll note that my access to the shared drive has been restricted.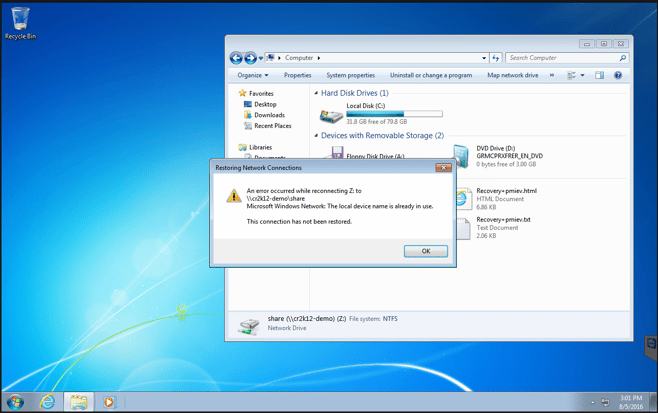
Screenshot 16
Once CryptoStopper.io detected the ransomware attack, I received an email message regarding the shutdown of my workstation.
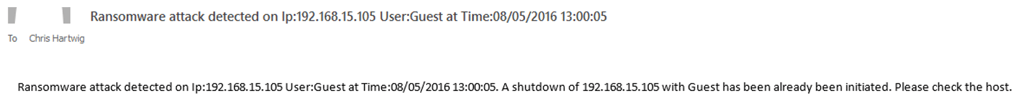
Screenshot 17
After attempting to access the share, Windows places a large red X over the drive to let me know access has been denied. I also noticed some pop-up windows that have opened up behind my active window.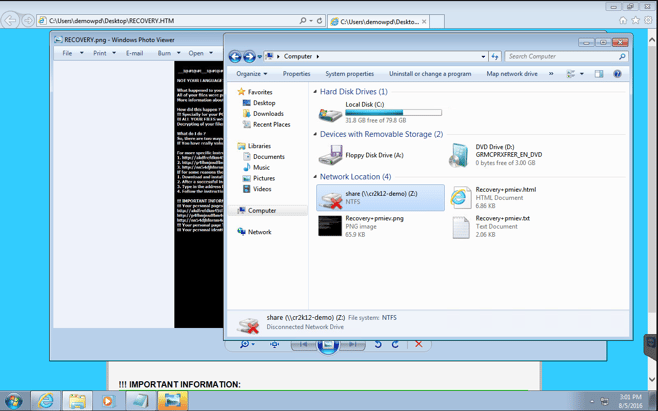
Screenshot 18
Here is my Windows 7 workstation displaying the .html, .png, and .txt ransom demand notices that just popped up unexpectedly.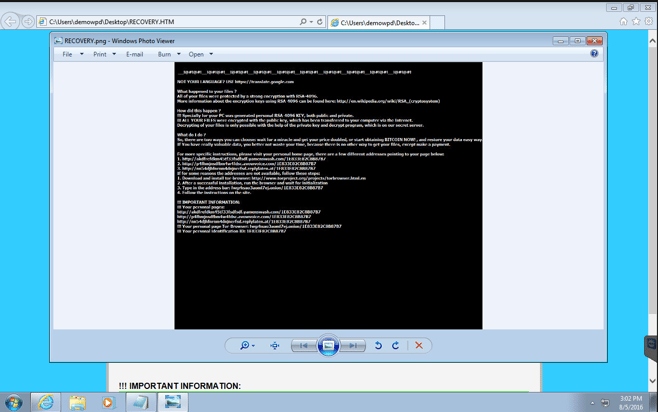
Screenshot 19
The biggest concern with this ransomware attack is how much data did it get on my server? I can verify that information by checking the events file located at C:\Program Files\CryptoStopper\events.csv
Examining this file confirms the ransomware attack was not successful. CrytpoStopper.io detected and isolated the workstation quickly and only allowed 12 files to be encrypted on the server.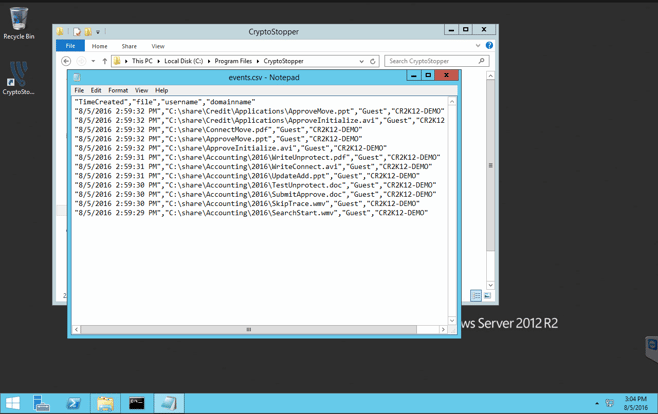
Screenshot 20
Screenshot 20 contains a shot of the registry showing the modification by TeslaCrypt.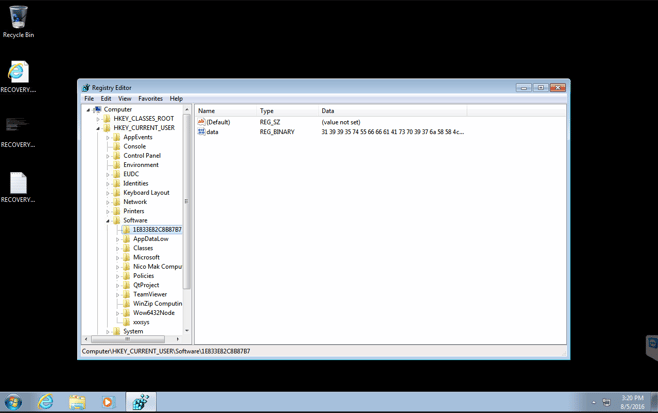
As you can see in this demonstration, CryptoStopper.io quickly identified the ransomware attack. CryptoStopper.io identified the attack in real time, isolated the infected workstation and prevented serious damage from occurring on the server. The administrator was notified immediately of the action taken by CryptoStopper.io and given the appropriate information needed to identify and repair the infected workstation.
Network Protection from the Inside-Out
CryptoStopper.io protects business networks from all forms of ransomware, saving money and time resulting from lost or stolen data. Unlike anti-virus which requires signatures, CryptoStopper is a signature-less system that stops ransomware seconds after it’s started. CryptoStopper gives businesses and techs a way to test the product before buying it with a free trial and a safe ransomware simulation system to test CryptoStopper.
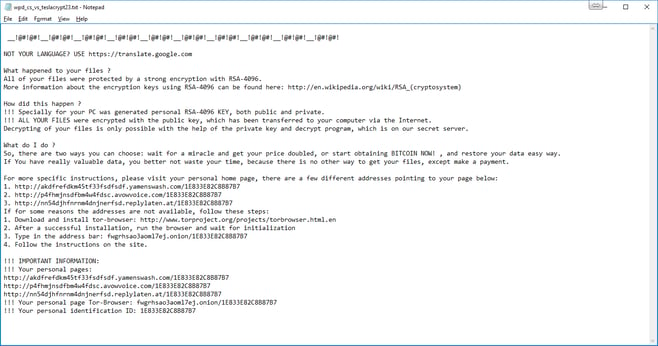
The Full Ransom Notes
Here are the full ransom notes as they appeared.
This HTML ransom was displayed in my web browser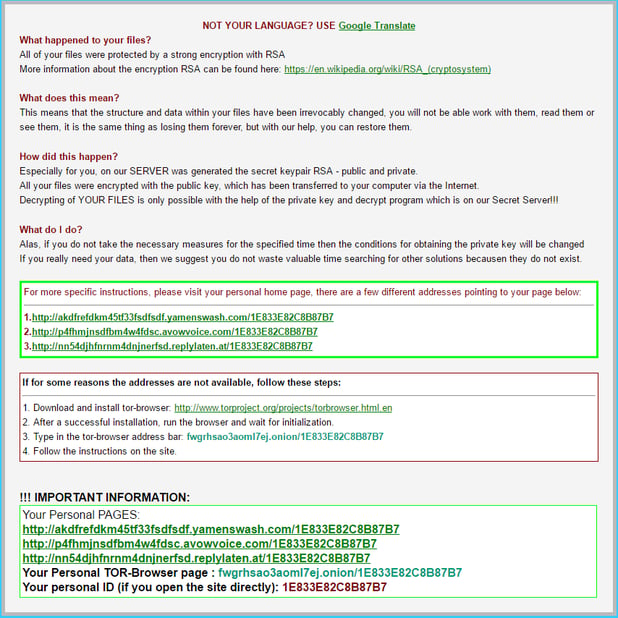
The PNG Format Ransom Note
The TXT Ransom