It seems every week we are writing about the “newest” ransomware threat. The first ransomware variants encrypted your files and demanded small ransoms from $50 to $250 to decrypt files. Today ransomware has evolved into a much bigger money-making apparatus. We are seeing variants that are now able to delete your encrypted files if the computer is rebooted or a deadline isn’t met. We are also seeing the amount of money demanded in ransomware attacks exploding, with one Hollywood California hospital paying $17,000 to cybercriminals to decrypt medical records.
The latest crypto ransomware variant that WatchPoint has encountered is called Maktub Locker. The interesting part of the Maktub Locker phishing campaign is how personal it is. The ransom note arrives in email and looks like a past due bill. The bill contains personal information including your actual home address and appears to be a notice from a collection agency collecting a debt for another company. There is a link included for payment, and it asks for payment no later than today’s date. This is a social-engineering tactic that creates urgency for the recipient to pay the bill immediately. 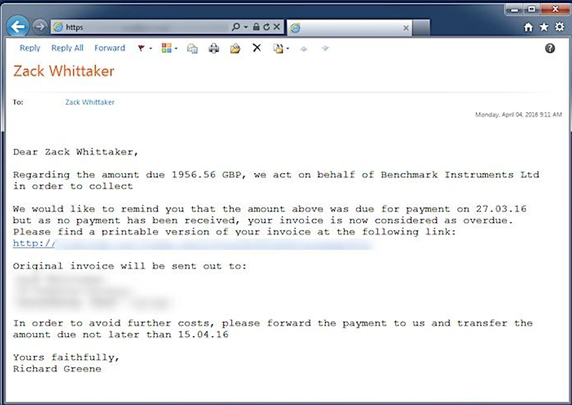
(Image: ZDNet/CBS Interactive)
Once the victim clicks on the email link and opens what appears to be a word document, the malware goes to work encrypting user files, and locks the user out of the computer until the ransom has been paid. Ransoms start at 1.4 Bitcoins and as time goes on the ransom amount will increase.
CryptoJoker – Ransomware You Can Negotiate With |
Cerber: Ransomware Speaks Bitcoin Demand |
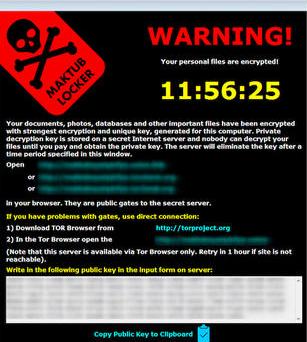
(Image: ZDNet)
So far Maktub Locker appears to be affecting computer systems overseas, mainly in Britain. BBC News reported that many of their staffers had received similar looking emails. When BBC News followed up with the companies listed in the phishing campaign, one company told them they had "more than 150 calls from people who don't owe us money."
How to Stop Ransomware Attacks
There are a number of things you can do today to prevent malicious software like banking and ransomware from entering your network.
Employee Education - Have frequent reviews with employees discussing the threat of phishing attempts and what to look for in emails to avoid getting compromised.
Run nightly backups - Backups won’t save you from all the hassles of banking Trojans, but will be useful to restore data from a ransomware attack.
Advanced Endpoint Protection – Use to detect suspicious behavior that signature-based solutions miss.
Deploy CryptoStopper.io: WatchPoint has developed CryptoStopper.io to stop ransomware. CryptoStopper.io continuously monitors your system for ransomware activity. When ransomware is detected, it will isolate the offending user, notify you of the infection and prevent any damage from occurring.
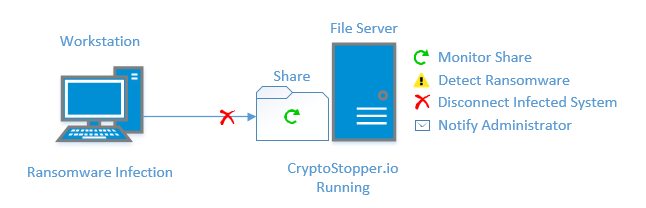 Contact us today to learn how you can become protected from the ever-prevalent threat of ransomware.
Contact us today to learn how you can become protected from the ever-prevalent threat of ransomware.
Further Reading:
Why Didn't My AntiVirus Detect CryptoWall?
Why Closing Unused Server Ports is Critical to Cyber Security
Cedar Rapids-Based WatchPoint Launches New Cybersecurity Product, CryptoStopper.io
Ransomware Destroying Business; How Do You Stop It?
FBI Releases Article on Ransomware


