
The word - Ransomware. It’s an interesting word. The first half being ransom- as in, to hold for ransom; and the second half -ware, as in, software; ransom-software. As with any ransom, there are four key elements: the break-in, robbery/kidnapping, communication of demands, and exchange of money for property. With the invention of new technologies efficiency increases come with it. That being said, I beg to ask the question: why should a ransom, used in a general sense, be any different?
What is Ransomware?
When ransomware hits your network, you know. There’s no doubt about it; it’s very noisy by design. Why? Because that's the point of a ransom: they have something of yours, and they want you to know it. The software, or ransomware, gets on your computer through one of a variety of methods, executes, and the damage is done.
The Break-In
The objective here is to get on your computer. Although there are several methods, the most commonly used technique is through email. It’s an age-old trick. You receive an email, and in it there is a link to a website, which then downloads something that you’re asked to run, or the email itself has an attachment that you’re asked to open. Once the bait has been taken, they’re in.
The Kidnapping
For the kidnapping, the key here is to find something of value. I would argue that there are several assets of value on your network; however, since most of these types of attacks are opportunistic, low-hanging fruit is all they’re after. Through some basic logic, they scan your computer and locate the highest value data. Once located, the actual kidnapping begins. Piece by piece, your data is transformed into an encryption format effectively rendering it temporarily useless.
Communicating Demands
Since the software is running on your computer, this is a pretty straightforward process. Typically, a set of files is created at the root of your shared drives with the likes of: DECRYPT_INSTRUCTIONS, HELP_DECRYPT, etc. Within these files you’ll see instructions on how to recover your data. Generally speaking, a window will also pop up with similar instructions.
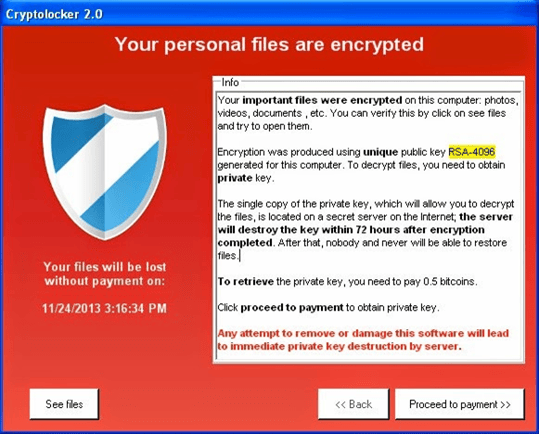
The Exchange
Within the window you’ll see a button or link of some kind to make a payment. This is how the exchange is facilitated. Usually the ransom is requested in the form of bitcoins. Once payment has been received, your data will be unencrypted. Or to put it another way, your property is then returned to you.

