
Raccoon Stealer, a new and easy to use trojan malware, is providing cybercriminals with a simple means of stealing credit card data, passwords, and cryptocurrency. The malware has already infected hundreds of thousands of Windows users around the world.
What is Raccoon Stealer?
Raccoon Stealer first appeared in April and has quickly become one of the most popular malware services for cybercriminals. Cybersecurity researchers note that while the malware is not sophisticated, it is being heavily marketed to potential criminals. For $200 a month, hackers are provided with an easy-to-use back end, bulletproof hosting, and 24/7 support. While $200 per month is considered a steep price relative to other offers on the dark web, criminals are likely to recoup the fee many times over through the financial and personal data stolen using the malware.
Raccoon Stealer’s Delivery Process
Creators of Raccoon Stealer made the malware flexible in the sense that it can be delivered to victims in several ways. However, it is most often delivered via exploit kits, phishing campaigns, or compromised software downloads. The exploit kits take advantage of vulnerabilities in common software used by victims. Raccoon then uses the Fallout exploit kit, which is used to spawn a Powershell instance from Internet Explorer and download the malware while the victim is simply browsing the web.
After successfully finishing its infection process, Raccoon communicates with a command-and-control server and begins to conduct its malicious activity. At this stage, Raccoon also gathers local settings on the target machine; if it detects the language is Armenian, Belarusian, Kazakh, Kyrgyz, Russian, Tajik, Ukrainian, or Uzbek, it will terminate the infection. As such, researchers believe the creators of Raccoon Stealer are based in Russia or Russian-speaking as it is common for malware originating from this area to avoid targeting Russian-speaking users.
Once this process is completed, Raccoon can steal system information, steal information from browsers such as login credentials and bank details, monitor emails, steal from cryptocurrency wallets, and take screenshots of the user’s activity. The capabilities of the malware combined with the ease-of-use features, allows attackers to steal large amounts of data from individuals and businesses alike. The stolen data is then either sold to the highest bidder on the dark web or used by the criminal to perpetrate identity theft, financial theft, or even as an entry vector to penetrate an organization to carry out a larger attack.
“Raccoon, like other information stealers, poses significant risks to individuals and organizations,” commented Assaf Dahan, senior director of threat hunting at Cybereason. “Any malware that is designed to steal passwords and personal information from browser and mail clients could potentially inflict great damage to its victims.”
The creators of Raccoon Stealer are active in updating the malware and are open to suggestions for ideas about new functionality. Several forum users on the dark web have suggested adding a keylogger to further weaponize the malware.
While Raccoon Stealer is relatively new as far as malware is concerned, it’s quickly gaining a large following among cybercriminals and has already infected hundreds of thousands of users across North America, Europe, and Asia. Despite its popularity, users can avoid becoming infected by the malware by applying security patches to software.
WatchPoint's Layered Security
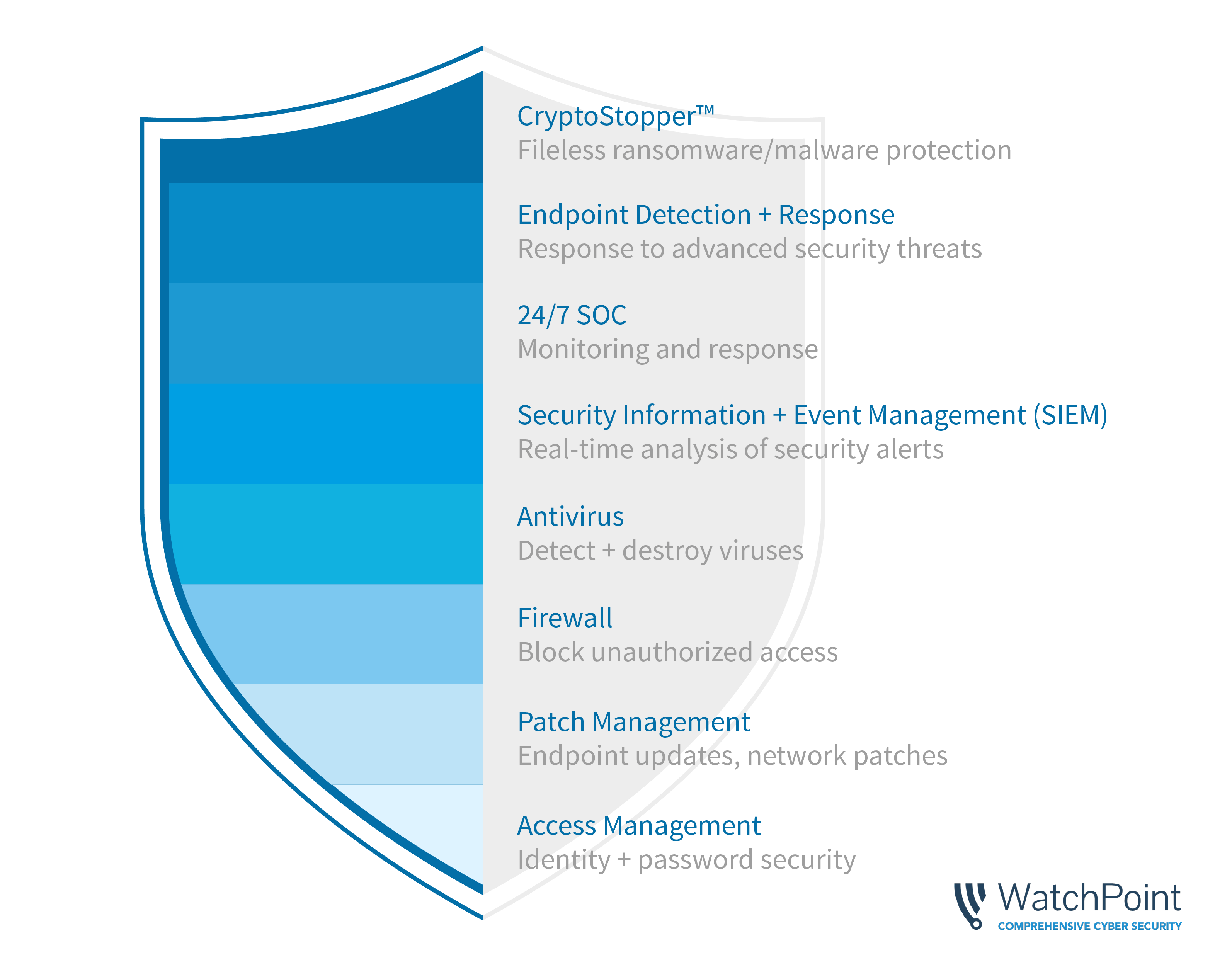
WatchPoint can also help with its Layered Security approach. Layered Security, or Defense in Depth, combines multiple layers of security which focus on prevention, detection, and response. Each one of the layers listed above protects against different types of threats. As cyber criminals get more sophisticated, your defenses need to as well - your traditional antivirus just isn't enough to protect you anymore. Contact WatchPoint to schedule a demo and learn more about Layered Security.
Photo courtesy of eyerys.com

