 Another week has gone by, and yet another cryptographic ransomware variant has emerged. The latest ransomware discovery has many in the industry concerned because it is rare for a cybercriminal to deploy ransomware that accepts a ransom payment but has no mechanism in place to actually decrypt the files.
Another week has gone by, and yet another cryptographic ransomware variant has emerged. The latest ransomware discovery has many in the industry concerned because it is rare for a cybercriminal to deploy ransomware that accepts a ransom payment but has no mechanism in place to actually decrypt the files.
In the past, cybercriminals have maintained a code of honor that required them to provide a decryption key after a bitcoin ransom was paid. They understood that in order to have continued success in extorting ransom payments, they had to follow through and decrypt the files after payment. If the cybercriminals do not decrypt the files after the ransom is paid, victims would quickly learn they were unlikely to get their files back and would then refuse payments en mass. Even so, there are a number of low-level cybercriminals who are not interested in honor but instead focus on deceiving you into paying a ransom after making you believe your files have been encrypted.
“There are a number of examples where true encryption doesn’t occur. Instead, cybercriminals rely on the social engineering edge of the attack to convince people to pay,” warns Grayson Milbourne, director of security intelligence at Webroot.
A typical ransomware attack encrypts files on network shares and then opens a ransom note with instructions to pay the ransom with bitcoins using the Tor network. The cybercriminals set up a command and control (C&C) server to gather information about your system and to provide the decryption key. The infection cycle of this strain follows that same formula but fails to live up to its promise to decrypt files after payment. In fact, it doesn’t even encrypt the files, it quite simply just deletes them! It deletes everything on attached shared folders and deletes system executables that are responsible for managing system restore points.
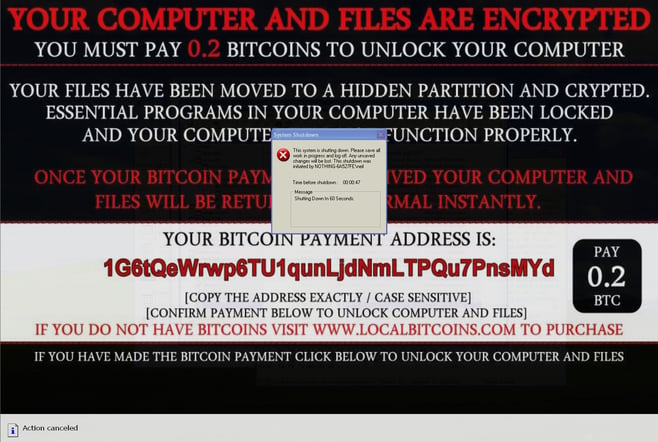
Have I Been Hit by Fake Ransomware?
It can be very difficult to tell if the ransomware strain you have been infected with is real or not. The most obvious clue that it is fake ransomware is that it doesn’t have a name like the other legitimate ransomware strains. You should also search the internet for the bitcoin payment address or search on the actual ransomware message to see what is being discussed in forums or by security researchers. Real ransomware changes the file extension of encrypted files. Try to change the file extension back to see if you can open the files. If you can, the files were not encrypted but just renamed to provide the illusion of encryption to get you to pay the ransom.
Dissecting this Fake Ransomware Strain
You can determine very quickly if you have been hit with fake ransomware in just a few steps. The most obvious clue will be the ransomware message that pops up and locks your screen. If you see this message, and your computer goes into shutdown mode, there is no need to research any further. Just get your backups ready to restore your files.
The Trojan adds the following entries into the system registry.
- %APPDATA%\winstrsp.exe [Detected as GAV: FakeRansom.A (Trojan)]
- %TEMP%\winopen.exewinopen.exe [Detected as GAV: Fakelock.C (Trojan)]
- %TEMP%\~8.bat
Check your running processes. The Trojan runs on reboot using schtasks.exe. The file z544 is an XML file that contains the task data.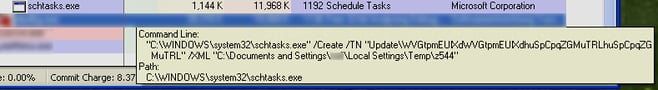
How to Fight Fake Ransomware
Thoroughly Inspect All Emails Received
Ransomware attacks are primarily delivered through email campaigns where the cybercriminals spoof a fax delivery, bank statement or utility bill. Check the email address, check for spelling and grammar errors and most importantly ask yourself “Was I expecting this email?”
Employee Education
A study by Security Affairs concluded that 97% of those surveyed failed to identify phishing emails from a group or random samples. Employees are the weakest link and need to be educated regarding ransomware attack vectors and what to look for in phishing emails.
Backups are Critical
Backups are critical to restoring your data that has been encrypted and will save you from having to pay the ransom. Restoring files from backup can be time-consuming so make sure your backups are up to date and that they are tested regularly. Having to restore from backup will cause downtime that costs your company money and could damage the business reputation.
Deception Technology
Deception Technology sets traps to misdirect the attacker and prevent them from going deeper into your network and reaching their intended target. These traps can be as simple as a document with a deceiving title that was created exclusively to lure in the cybercriminals. For example, you could create a trap using a simple word document and give that doc an attractive name like “Passwords.docx”. When the document is opened, it triggers an alert to the system administrator.
Ransomware Protection
According to the FBI, ransomware is on track to be a $1 billion dollar business in 2016. It is a safe bet to say that new ransomware strains will continue to be released at rates never seen before as more and more cybercriminals flock to ransomware. Cybersecurity companies have been slow to respond but ransomware prevention technology is available.
Enhance Your Network Defenses Today!
Protecting your network isn’t something to put off until tomorrow. Use the tips outlined above to educate your employees about the threat of ransomware and what to look for when examining emails for signs of a possible attack. Making sure your backups are in good working order is critical and using deception technology and installing ransomware protection will stop an attack when it gets past your initial defenses. Prevention is key, but protection is a must.

