 On Tuesday (July 26, 2016) the Obama administration released a framework for handling cyberattacks. The Presidential Policy Directive (PPD) on United States Cyber Incident Coordination is a new plan anticipated to create a precise standard of when and how government agencies handle incidents. At the start of his administration, President Obama made it clear that cyberattacks pose a grave threat to the economic and national security of the United States. Previous to the PPD, the Cybersecurity National Action plan was a policy based on three strategic pillars:
On Tuesday (July 26, 2016) the Obama administration released a framework for handling cyberattacks. The Presidential Policy Directive (PPD) on United States Cyber Incident Coordination is a new plan anticipated to create a precise standard of when and how government agencies handle incidents. At the start of his administration, President Obama made it clear that cyberattacks pose a grave threat to the economic and national security of the United States. Previous to the PPD, the Cybersecurity National Action plan was a policy based on three strategic pillars:
- Raising the level of cybersecurity in both the short and long-term in our public, private and consumer sectors
- Taking steps to prevent, disrupt and interfere with cyberattacks aimed at the United States
- Responding effectively to and recovering from cyberattacks
Presidential Policy Directive on US Cyber Incident Coordination
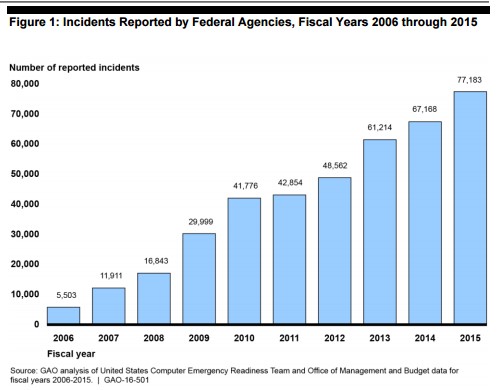
While the Obama Administration has made progress on the three pillars, the country has been faced with managing increasingly significant cyber incidents. Since 2006, cyberattacks against the US Government are up 1,300 percent. Breaches such as the attack by Russian hackers on the Office of Personnel Management where a reported 5.6 million Americans’ personally identifiable information were stolen. In late June, the Democratic National Convention (DNC) was hacked and included files from the 2012 Benghazi attack, the U.S. military intervention in Libya, and the Clinton email server controversy. Most recently, the Federal Department Insurance Corporation (FDIC) cover-up of their data breachesin 2010, 2011, and 2013 was exposed.
According to their website, the PPD is intended to build on the lessons learned from these hacks and institutionalize our cyber incident coordination efforts in numerous aspects, including:
- Establishing clear principles that will govern the Federal government’s activities on cyber incident response
- Differentiating between significant cyber incidents and steady-state incidents and applying the PPD’s guidance primarily to significant incidents
- Categorizing the government’s activities into specific lines of effort and designating a lead agency for each line of effort in the event of a significant cyber incident
- Creating mechanisms to coordinate the Federal government’s response to significant cyber incidents, including a Cyber Unified Coordination Group similar in concept to what is used for incidents with physical effects, and enhanced coordination procedures within individual agencies
- Applying these policies and procedures to incidents where a Federal department or agency is the victim
- Ensuring that our cyber response activities are consistent and integrated with broader national preparedness and incident response policies so that our response to a cyber incident can seamlessly integrate with actions taken to address physical consequences caused by malicious cyber activity.
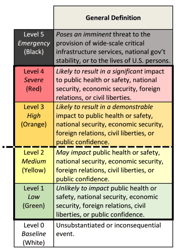
Included in the PPD, is the “Cyber Incident Severity Schema” which will unify how the federal government will respond to cyberattacks against both the government and private American companies.
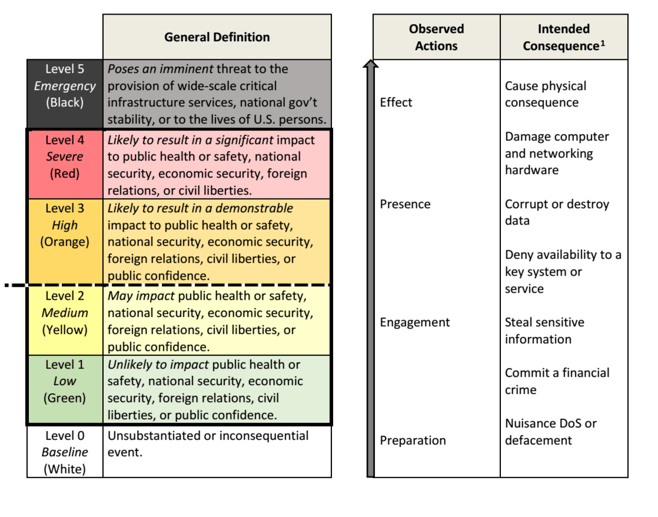
The schema, shown above, ranges from white to black, with green, yellow, orange, and red falling in between. While the scale is somewhat vague and has a lot of unanswered questions, it’s intended to ensure that the agencies involved in cybersecurity respond to threats with the same level of urgency and investment. Anything above the dotted line, separating orange and yellow, indicates a significant cyber incident that will trigger a coordinated response from government agencies.
Cybersecurity continues to be a growing concern for the US Government, and high-profile hacks have led to serious consequences for the parties involved. While it’s too early to gauge the success of the PPD, we have to hope that it will be a huge step in securing the personally identifiable information of our citizens and our most valuable data from the persistent threat of data breaches.

