A brute-force attack is a common threat faced by web developers where an attacker attempts to crack a password by systematically trying every possible combination of letters, numbers, and symbols…
Malware: Coming of Age
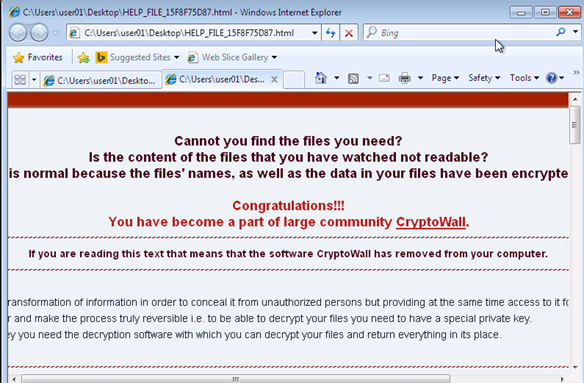
Malware, short for malicious software, covers any infectious file on a computer system. Common examples are viruses, worms, Trojan horses, and ransomware. Throughout the decades, these mal-intended…
Tips to Help Stop a Brute-force Attack
A brute-force attack is a common threat faced by web developers where an attacker attempts to crack a password by systematically trying every possible combination of letters, numbers, and symbols…
The Established Threat of Passwords
Passwords, passwords, and more passwords; this is normally the subject that websites, technology help staff, network administrators, and other computer related experts will harp on the most. I am…
When Failure to Act Results in a Compromised Network – A Sad Cryptolocker Tale
I’d like to discuss a situation that arose this week with a former backup customer and how that customer came to realize they need WatchPoint. For privacy concerns, I will address the business as…
Ransom32: The First JavaScript Ransomware
Security researchers have found a new ransomware-as-a-service (RaaS) using JavaScript (JS) framework called NW.js. The new RaaS, tabbed as Ransom32, is different from other RaaS attacks as it is…
Top 4 No-Cost Ways to Secure Your Network
Cyber criminals go after the easiest targets. Make your system as hard of a target as possible with these easy to implement suggestions. The list below assumes you have a firewall and Anti-Virus (AV)…
How Many of Your Employees Will Get Phished Today?
Phishing is an attempt by cybercriminals to steal your money and data using malicious email messages, websites and sometimes even phone calls. These criminals gain access to your information by…
Adapt or get Hacked - It takes a Village to Secure a Network We’ve all heard that it takes a village to raise a child. What you’ve probably never heard is that it takes a village to secure a network.…