
 Almost certainly by now, we’re all aware that cyber criminals use social engineering and phishing attacks to trick users into opening malicious emails. Hackers use double extensions such as myfile.doc.exe or myfile.xls.js. Hackers will change file icons, and embed malicious macros into otherwise harmless looking files.
Almost certainly by now, we’re all aware that cyber criminals use social engineering and phishing attacks to trick users into opening malicious emails. Hackers use double extensions such as myfile.doc.exe or myfile.xls.js. Hackers will change file icons, and embed malicious macros into otherwise harmless looking files.
Those classic deceptive techniques are the ones that we always hear about, but in this article, we’ll show you two other techniques that are less known and seldom discussed.
RTLO – Right To Left Override
The first lesser known deceptive tactic is called RTLO. This technique leverages the fact that not all languages are written from left to right. Some languages, like Arabic and Hebrew, are written from right to left.
To understand this better, you need to first understand that computers use something called Unicode. In fact, you use Unicode already; it’s just that the computer has been doing it for you. Essentially, computers use Unicode to distinguish between characters of different languages.
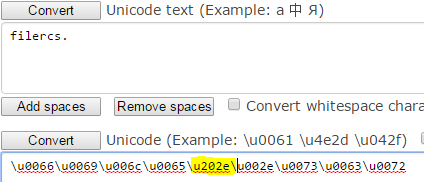
The Unicode character for today's deception is u202e. This will instruct Windows to flip the text from left to right, to right to left. Now that we have a basic understanding of what Unicode is, I’ll demonstrate how a Hacker can exploit RTLO to hide a file extension
- First, we’ll take an executable file called file.scr. The SCR file extension is for screen savers and is more deceptive than using .exe.
- Using a Unicode converter enter the file name.
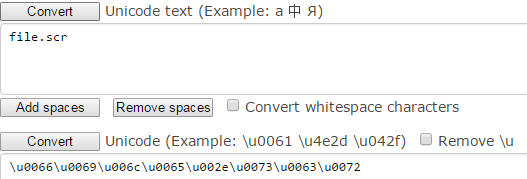
3. Next, add our u202e Unicode so we can reverse the order of the text.
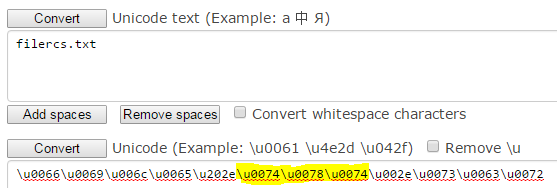
4. Now we need to add the spoofed .txt extension. To do this, edit the Unicode using the following string; u0074\u0078\u0074
 5. Now copy the filename to the file on our computer.
5. Now copy the filename to the file on our computer.
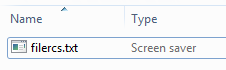 6. To prove that it worked, try to edit the file name, and you’ll see that the select pattern is not continuous.
6. To prove that it worked, try to edit the file name, and you’ll see that the select pattern is not continuous.
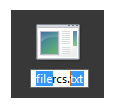
This method is very deceptive and not at all easy to spot, which is why it’s being used by hackers.
PIF Extension
This deceptive trick doesn’t rely on languages or Unicode characters. Instead, it takes advantage of the fact that Windows hides .pif extensions, even when the feature of disabling file extensions has been turned off.
This is especially dangerous because PIF files instruct Windows how ms-dos commands should be run. This provides the attacker with a unique way to disguise a malicious file. To prove that this works, follow the steps below:
- First, create a file with the .txt file extension. Note how the file is a normal looking file, and we can see the file extension.
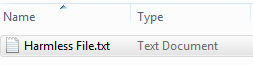
2. Next, add the .pif file extension to the file. Notice how the file type changes but the new .pif file extension is hidden.
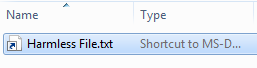
This tactic works because the changes are very subtle. When the file is stored on your computer’s hard drive, the file type changes and the image adds a shortcut arrow, but the actual file extension is hidden.
Conclusion
As they say, the devil lies in the details. And in the case of file extensions, hackers use every trick in the book to disguise their malicious files. Read more about phishing techniques and ways to protect yourself.

