Cerber Avoids Detection
- The latest strain of Cerber ransomware has been upgraded to morph every 15 seconds to avoid detection.
- Traditional AV can't update quick enough to keep up.
- 12M to 16M new malware variants created every month.
- 93% of phishing campaigns are now ransomware.
 Earlier this year WatchPoint reported on a new ransomware variant that had emerged called “Cerber” that not only encrypts files but will also use a text-to-speech function to read the ransom demand out loud to you. The ransomware is thought to have originated from Russian underground forums. The program is so effective that there is currently no way to decrypt compromised files without paying the ransom. As if that wasn’t enough to keep you awake at night, the latest upgrade to the Cerber ransomware should. Now Cerber has been upgraded to use polymorphing techniques that allow it to change the file hash every 15 seconds to avoid detection by antivirus programs.
Earlier this year WatchPoint reported on a new ransomware variant that had emerged called “Cerber” that not only encrypts files but will also use a text-to-speech function to read the ransom demand out loud to you. The ransomware is thought to have originated from Russian underground forums. The program is so effective that there is currently no way to decrypt compromised files without paying the ransom. As if that wasn’t enough to keep you awake at night, the latest upgrade to the Cerber ransomware should. Now Cerber has been upgraded to use polymorphing techniques that allow it to change the file hash every 15 seconds to avoid detection by antivirus programs.
Researchers at Invincea discovered the ability of Cerber to morph every 15 seconds while tracking the ransomware’s activities since its discovery earlier this year. According to Pat Belcher, who has tracked Cerber since its discovery earlier this year, "Invincea researchers see dozens of Cerber infection attempts every day. However, when we tried to duplicate the download for this variant, we noticed that the hash we received from the payload delivery server had a different hash than the one in the event above. When we downloaded it a third time, there was yet another hash. Fifteen seconds later, there was another, and then another. In all, we downloaded over 40 uniquely hashed Cerber payloads — all with different hashes."
Decryption of Data Impossible without Paying Ransom
“… at this point there is no known way to decrypt a victim's encrypted files for free," Lawrence Abrams, Bleeping Computer.
"When infected, a victim's data files will be encrypted using AES encryption, and they will be told they need to pay a ransom of 1.24 bitcoins or $500 to get their files back. Unfortunately, at this point there is no known way to decrypt a victim's encrypted files for free," explained Lawrence Abrams, a malware expert at BleepingComputer who has analyzed the Cerber source code. One reader that we spoke with did claim that he was able to use a decryptor he purchased from a member on another cybersecurity forum. Although he was not able to decrypt all the files, he was able to get about half of them back.
CryptoJoker – Ransomware You Can Negotiate With
A Spoken Ransom
Cerber sets itself apart from all other crypto ransomware with its ability to vocalize the ransom to the victim. I recently wrote an article about a company that has been hit with crypto ransomware three times. The third time the company was hit with ransomware, I heard the ransom message as it was playing on the victim’s computer. Even before gaining remote access to the machine to visually see the infection; I heard the ransom and confirmed the crypto ransomware infection.
"One of the ransom notes that Cerber creates is a bit more 'special' than the others. The #DECRYPTMYFILES.vbs file contains VBScript, which will cause the victim's computer to speak to them," explained Abrams.
As you can see in the screenshot below; the ransom note contains a link to a Tor-based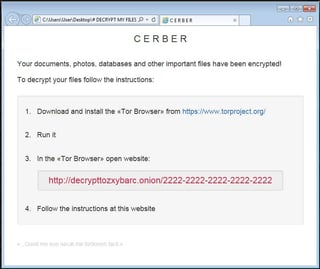 website called “Cerber Decryptor” which provides step by step instructions on how to pay the ransom with Bitcoins. If the ransom isn’t paid, the ransom amount will double the following week. Notice the quote at the bottom. Talk about adding insult to injury.
website called “Cerber Decryptor” which provides step by step instructions on how to pay the ransom with Bitcoins. If the ransom isn’t paid, the ransom amount will double the following week. Notice the quote at the bottom. Talk about adding insult to injury.
“…Quod me non necat me fortiorem facit.”
"That which does not kill me makes me stronger." - Friedrich Nietzsche
How to Decrypt Jigsaw Ransomware
As previously mentioned, there is no free option to decrypt your files. Now that Cerber can modify its payload and change its hash every 15 seconds, antivirus detection is almost impossible. If you get hit with Cerber, you will have to pay the ransom unless you have a good backup that you can use to restore your data. I highly recommend you examine your current backups to make sure they are working properly or getting hit with Cerber is going to set you back. Now is a good time to look at other no-cost ways to secure your network as well.
CryptoStopper.io Puts an End to Ransomware
Stopping Ransomware from entering your network is next to impossible. CryptoStopper.io will contain the damage and save your network from complete compromise and downtime.

CryptoStopper.io is the answer to the ransomware problem plaguing the world today. CryptoStopper.io was developed to identify ransomware by watching the data on your network. By monitoring WatchPoint files for read/write operations, we can detect the presence of ransomware the moment it happens.
CryptoStopper.io provides information about the infection such as the infected user account, the infected computer account, and most importantly it disconnects the infected workstation from the rest of the network.
- Know the moment a ransomware attack hits.
- Identify which user launched the ransomware payload.
- Identify which workstation is infected.
- Disconnect the infected workstation; stopping the ransomware attack.

Further Reading…
Banking Trojan Targeting Android Devices Can Bypass 2FA
How to Safely Download Software
Lock Down Exchange from Brute-Force Attack
Refusal to Upgrade to Windows 10 Putting Millions at Risk of Malware Infection

