Stuxnet is known as the world’s first cyber weapon. Stuxnet was used to break Iran’s uranium enrichment centrifuges when it was feared they were producing chemical weapons. While there’s no proof as to who created the zero-day exploit, everyone seems to agree that it was the National Security Agency (NSA) who launched the digital weapon. Stuxnet, which was previously named ‘Olympic Games’, made its way into the Iranian nuclear enrichment facility at Natanz in 2006. The code infected specific industrial control systems the Iranians were using and proceeded to speed up or slow down the centrifuges until they destroyed themselves, all while the operators’ computer screens showed everything was working as normal.
While Stuxnet certainly worked to combat Iran’s efforts to make chemical weapons, the powerful computer code’s self-replicating behavior escaped Iran’s network and ended up infecting computers all around the world. Stuxnet became so popular and such an intriguing story that a film called ‘Zero Days’ was released in June 2016.
Sony Zero-Day Attack
In late 2014, Sony Pictures Entertainment fell victim to a zero-day attack. While the specific vulnerability that was exploited is unknown, it is clear that Sony was the victim of the worst corporate attack in history. A team of hackers by the name of Guardians of Peace crippled Sony’s network and proceeded to release sensitive corporate data on public file-sharing sites, including four unreleased featured films, business plans, contracts, and the personal emails of top executives. All-in-all, hackers claimed they had taken nearly 100 terabytes of data over the several weeks they were on Sony’s network. The motivation behind this attack wasn’t for monetary gains for the hackers, as they claimed the movie “The Interview,” which concerns a CIA-backed plot to assassinate North Korean leader Kim Jong-un, shouldn’t be allowed to make Sony any profit.
$90,000 Zero-Day Exploit For Sale
In June of 2016, a zero-day exploit was being sold for $90,000by a Russian cybercriminal named ’BuggiCorp’ on the dark web. The zero-day vulnerability was believed to be able to affect machines running any form of Windows, from Windows 2000 up to Windows 10. Should that be true, the vulnerability had the potential to impact over 1.5 billion Windows users.
This zero-day attack targeted a local privilege escalation (LPE) where, if exploited, a hacker can make any Windows user level account into an administrator account. While this exploit can’t provide an initial infection vector like most zero-day attacks do, it’s likely to be used alongside another form of malware.
“This type of flaw is always going to be used in tandem with another vulnerability to successfully deliver and run the attacker’s malicious code,” said Brian Krebs from Krebs on Security. “Chain that remote exploit with a local privilege escalation bug that can bump up the target’s account privileges to that of an admin, and your remote exploit can work its magic without hindrance.”
This exploit was originally listed for $95,000 only to be lowered to $90,000 after a couple of weeks on the market. In the listing, ‘BuggiCorp’ shows two videos of successful exploits, one which was right after ‘Patch Tuesday’ with the most updated version of Windows. While it’s uncertain whether this exploit was purchased, it could be a couple of years before it’s discovered that it was used in the next ‘big’ zero-day attack.
The DNC Hack
The DNC hack is one that we are all familiar with and have covered over the last eight months. The data that was released about the Democratic National Committee (DNC) was a result of a zero-day attack. In fact, there were at least six zero-day vulnerabilities that were exploited to gain access to the data that was stolen. The vulnerabilities were found by state-backed, Russian hackers in Microsoft Windows 10, Adobe Flash, and Java. In order for the vulnerabilities to be exploited, the gang of hackers engaged in a spear-phishing campaign.
In a spear-phishing campaign, as opposed to a phishing campaign, hackers are targeting very specific individuals instead of the general public. In this campaign, the Russian hackers sent out thousands of emails with booby-trapped links to password-stealing phishing pages to individuals involved with the DNC. Anyone who clocked on the bit.ly and tiny.cc-concealed URLs essentially handed over control of their PCs and the DNC network to the hackers.
Zero Day Defined
Zero-day attacks, also known as zero-day vulnerabilities or zero-day exploits, all have common but slightly different definitions. Some define zero-day attacks as attacks on vulnerabilities that have not been patched or made public, while others define them as attacks that take advantage of security vulnerabilities on the same day that the vulnerability becomes publicly known. With that being said, the biggest zero-day attacks that we have seen have come from software or hardware vulnerabilities that have been exploited by an attacker with no prior knowledge of the flaw in the general cyber security community. This type of zero-day attack can cause the most damage as it can go years without being detected and there is no fix or patch readily available even if it is discovered.
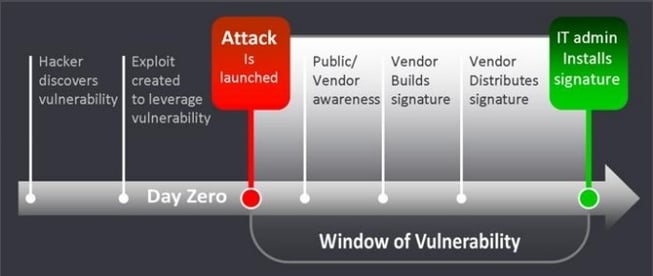
What’s the point of a zero-day attack? Zero-day attacks essentially give a hacker a master-key so they can enter any part of your network without being seen. When a hacker finds a vulnerability in a software or hardware program, they are able to gain complete access to a user’s workstation. The hacker can then do as they please; whether that be extracting the most valuable data from a company and selling it on the dark web or using that data for defamation of a company or certain individuals.
Outlook
Just like ransomware attacks, zero-day attacks aren't going anywhere. Cybercriminals are always finding Common Vulnerabilities and Exposures (CVEs) that can be used to exploit software or hardware programs. In fact, according to CVEdetails.com, there are currently 185 CVEs that register over a 9 on their scale. Any score over 9 indicates that a hacker could expose this vulnerability in the software or hardware program and gain complete control of your PC. Unfortunately, if a vulnerability is exposed and you fall victim to a drive-by download, there's nothing you can do about it.
What can you do? The first and most important thing to do is to ensure that all of your software and hardware programs are up-to-date with the latest updates and patches. Also, never clink on a suspicious link in an email or open up an attachment from an individual you don't know. If doesn't look right, chances are it's not. Be diligent with your cybersecurity and don't let your curiousity get the best of you!

